Linux Auto-Start Services The Complete Guide
How to auto start services on boot in Linux is a crucial skill for any Linux user. Understanding how to automatically launch essential services when your system boots can streamline your workflow and ensure your applications are always running smoothly. This guide delves into the world of system initialization, exploring different methods, from the foundational to the advanced.
We’ll cover everything from the basics of auto-starting to troubleshooting common issues and securing your system against vulnerabilities.
This comprehensive guide provides a step-by-step approach to auto-starting services on Linux. We’ll cover systemd, the modern service manager, as well as older methods like upstart and SysV init. This allows for a thorough understanding of the entire spectrum of service management. Expect practical examples, detailed explanations, and actionable advice to make your Linux setup more efficient and secure.
Introduction to Auto-starting Services
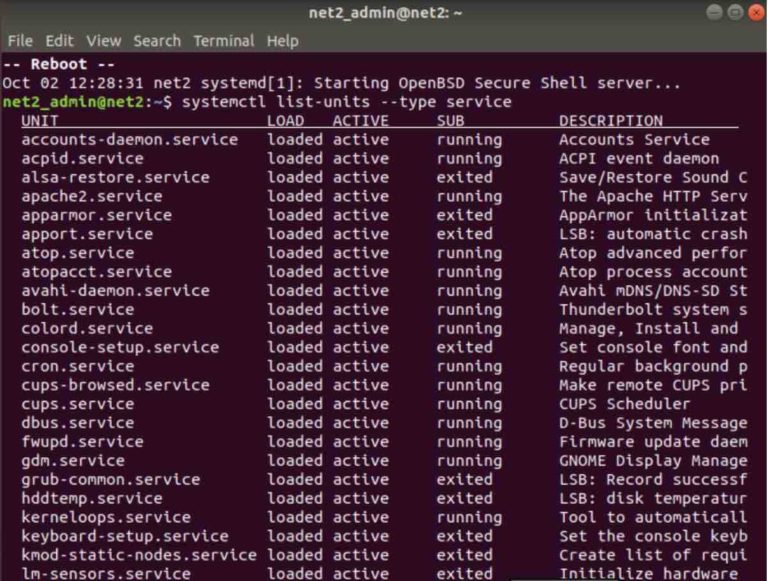
Auto-starting services in Linux is a crucial aspect of system administration. It ensures that essential applications and background processes are automatically initiated upon system boot, guaranteeing smooth operation and optimal performance. This approach eliminates the need for manual intervention, simplifying the startup process and enhancing the user experience. The seamless integration of services with the boot process streamlines system functionality, improving overall efficiency.Automating service startup offers numerous benefits, ranging from improved system responsiveness to enhanced security.
Services running automatically at boot provide a consistent and reliable platform for various tasks. The predictable and automated approach allows administrators to focus on other critical system maintenance and configuration tasks, leading to increased productivity.
Importance and Benefits
Automatic service startup is vital for a multitude of reasons. Firstly, it ensures that essential services are readily available upon system boot. This guarantees the prompt availability of applications and functionalities, leading to a more responsive system. Secondly, automated service initiation simplifies system administration, minimizing manual intervention and potential errors. Thirdly, auto-starting services enhances system security.
By ensuring only authorized services start up, it prevents unauthorized processes from running, reducing the risk of malicious activity.
Common Use Cases
Auto-starting services is applicable across a broad spectrum of system tasks. These include:
- Running daemons for network services (like web servers, mail servers, and FTP servers): These services are fundamental for providing network connectivity and communication. Automatic startup ensures these services are available whenever the system is online.
- Managing database servers: Database servers are critical components for storing and retrieving data. Automatic startup ensures data accessibility and maintainability, preventing downtime and data loss.
- Running background tasks and processes (like file transfers, backups, and scheduled jobs): These types of tasks are vital for system maintenance and data integrity. Auto-starting ensures that these tasks run reliably in the background.
Comparison of Auto-starting Methods
The following table Artikels various methods for auto-starting services, highlighting their advantages and disadvantages:
| Method | Description | Advantages | Disadvantages |
|---|---|---|---|
| Systemd (init system) | The default init system in most modern Linux distributions. It uses unit files to define services and their dependencies. | Highly flexible, powerful, and robust. Supports complex service dependencies and provides excellent control over startup order and resource allocation. | Steeper learning curve compared to other methods. Requires understanding of systemd unit files. |
| Upstart | An init system used in some Linux distributions. It uses configuration files to define services and their startup conditions. | Generally easy to use for simple services. | Less flexible than systemd, especially for complex service interactions and dependencies. Its use is declining. |
| rc.d scripts | A legacy approach that uses scripts in the /etc/rc.d directory. | Relatively straightforward for simple services. Familiar to users with experience with older systems. | Difficult to manage complex dependencies and maintain. Lacks the flexibility and robustness of systemd. |
Systemd and Service Management
Systemd is the system and service manager in modern Linux distributions. It’s responsible for starting, stopping, and monitoring various services, including daemons, applications, and system utilities. This centralized approach provides a more robust and efficient way to manage services compared to older methods. It offers a structured and standardized way to handle service initialization, dependencies, and resource management.
This allows for better system stability and reliability.Systemd’s core function is to provide a standardized interface for interacting with services, ensuring consistent behavior across different applications and system components. This standardized approach improves the reliability and stability of the entire system. This sophisticated management system is crucial for a smooth and predictable system startup and shutdown.
Systemd Service File Structure
Systemd service files are configuration files that define how a service should be managed. They use a specific format and structure to describe the service’s behavior, dependencies, and resource usage. These files are typically located in the `/etc/systemd/system` directory. This centralized location ensures all services are easily managed and accessible.
Example Systemd Service File
Here’s a sample systemd service file (my_service.service):“`[Unit]Description=My Custom ServiceAfter=network.target[Service]Type=simpleUser=myuserWorkingDirectory=/home/myuser/service_dirExecStart=/home/myuser/service_dir/myscript.shRestart=alwaysRestartSec=5[Install]WantedBy=multi-user.target“`This file configures a service named “My Custom Service.” It ensures the service starts after the network is fully configured.
Essential Components of a Systemd Service File
The example service file demonstrates the key components of a systemd service file:
- [Unit] section: This section defines metadata about the service, such as its description and dependencies. The “After=network.target” line is crucial for ensuring the network is operational before the service starts.
- [Service] section: This section specifies how the service should run, including the execution command, user, working directory, and restart policy. The “Restart=always” ensures the service restarts automatically if it fails. The “RestartSec=5” specifies a delay before restarting.
- [Install] section: This section specifies how the service should be installed and enabled to start automatically at boot time. The “WantedBy=multi-user.target” line ensures the service starts when the system is in multi-user mode.
Systemd Service File Options
A table outlining various options within a systemd service file:
| Option | Description | Example Usage |
|---|---|---|
Type |
Specifies the service type (e.g., simple, forking). | Type=simple |
User |
Specifies the user under which the service should run. | User=myuser |
WorkingDirectory |
Specifies the working directory for the service. | WorkingDirectory=/home/myuser/service_dir |
ExecStart |
Specifies the command to execute when starting the service. | ExecStart=/home/myuser/service_dir/myscript.sh |
Restart |
Specifies the service’s restart policy. | Restart=always |
RestartSec |
Specifies the delay in seconds before restarting a failed service. | RestartSec=5 |
EnvironmentFile |
Specifies a file containing environment variables for the service. | EnvironmentFile=/etc/myenv.conf |
TimeoutStopSec |
Specifies the maximum time in seconds to wait for the service to stop. | TimeoutStopSec=30 |
Using `systemd` Units
Systemd, the system and service manager for Linux, provides a powerful mechanism for managing services. This approach is more flexible and reliable than older methods, offering precise control over service startup, dependencies, and more. A crucial aspect of this management is the use of systemd unit files. These files define how a service should behave, including when it starts, stops, and monitors its status.Understanding systemd units unlocks a deeper level of control over your Linux system.
You can precisely tailor service behavior, ensuring services start reliably and at the appropriate time. This includes the ability to manage dependencies between services, guaranteeing the proper order of startup and shutdown. Furthermore, systemd units offer sophisticated error handling, logging, and monitoring capabilities.
Creating a Systemd Unit File
A systemd unit file defines the characteristics of a service. It specifies the commands to start and stop the service, and the conditions under which it should run. The file typically resides in the `/etc/systemd/system/` directory. The file’s extension is `.service`.
Unit File Syntax and Structure
The syntax of a systemd unit file is structured around key-value pairs, defining the service’s properties. A critical aspect is the `[Service]` section, which Artikels the service’s behavior. Within this section, parameters such as the executable path, user, group, working directory, and environment variables are specified. Other crucial sections include `[Install]`, which defines how the service should be enabled for startup, and `[Unit]`, which provides information about the unit itself, such as dependencies.“`[Unit]Description=My Custom ServiceAfter=network.target[Service]Type=simpleUser=myuserGroup=mygroupWorkingDirectory=/home/myuser/serviceExecStart=/home/myuser/service/myscript.shRestart=alwaysRestartSec=10[Install]WantedBy=multi-user.target“`This example demonstrates a basic unit file.
`Description` provides a helpful label. `After=network.target` ensures the service starts only after the network is ready. `Type=simple` indicates a straightforward service. `ExecStart` specifies the command to execute. `Restart=always` configures the service to restart automatically if it crashes.
`RestartSec` sets the delay before a restart attempt. `WantedBy=multi-user.target` ensures the service is enabled for a multi-user session.
Figuring out how to automatically start services on boot in Linux can be a lifesaver. You can avoid manual intervention every time you boot up. Meanwhile, the recent news surrounding a new offshore oil drilling ban in California, announced by President Biden, new offshore oil drilling ban biden california , highlights the growing urgency for alternative energy sources.
This ban, coupled with the need to keep systems running smoothly, emphasizes the importance of understanding Linux boot processes. Fortunately, adjusting startup configurations is straightforward with a few simple commands.
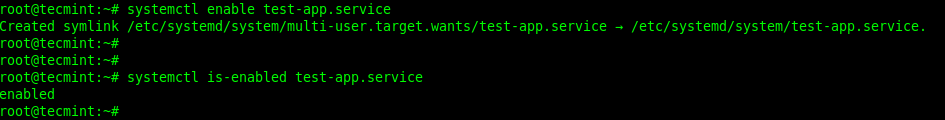
Enabling a Service to Start on Boot
To enable a service to automatically start during boot, you need to use the `systemctl` command. The `enable` command links the unit file to the system’s startup process. The command `systemctl enable Systemd offers several ways to control service startup behavior. `After` directives in the `[Unit]` section specify dependencies, ensuring services start in the correct order. `Restart` directives determine how the service handles crashes. The `TimeoutStartSec` and `TimeoutStopSec` parameters control how long the system waits for a service to start or stop, respectively, before considering it failed. Delaying startup can be achieved through dependencies.
1. Create the service script
Write the script (`myscript.sh`) that will run your service. This script should contain the commands to execute your application.
2. Create the systemd unit file
Create a file named `my-service.service` in `/etc/systemd/system/` with the content as shown in the previous example, ensuring the paths and commands are correct.
3. Enable the service
Figuring out how to automatically start services on boot in Linux can be tricky, but it’s crucial for smooth system operation. Similar to the recent, massive award in the Santa Clara HOA lawsuit, this major California HOA case highlighting extensive deception over an abandoned well under a condo highlights the importance of transparency and proper procedure.
Ultimately, knowing how to set up auto-start ensures your services are ready to go every time you power on, just like a well-maintained system.
4. Start the service
Use `systemctl start my-service.service` to immediately start the service.
5. Check the status
Use `systemctl status my-service.service` to verify the service’s status and operation.By following these steps, you can effectively integrate custom services into your Linux system’s boot process.
While systemd has become the dominant init system in modern Linux distributions, understanding older approaches like upstart and SysV init provides valuable context. These legacy systems, while less prevalent today, still run in some environments and offer insights into the evolution of service management. This section delves into their functionalities, limitations, and how they compare to systemd.Systemd’s design aims for greater efficiency and control over services, but understanding the historical context of other methods illuminates the motivations behind its development.
Examining their strengths and weaknesses will help you appreciate the improvements introduced by systemd and apply that knowledge to your own service management strategies.
Automating services to start up on boot in Linux is super handy. You’ll often find yourself needing to tweak systemd configuration files, like `systemd.service`. Meanwhile, it’s interesting to see how local officials are reacting to recent events, like they said it local official dares president trump , and how this might influence future political discourse. Ultimately, understanding service startup configurations is a great way to keep your Linux system running smoothly.
Upstart, a successor to SysV init, improved upon its predecessor by introducing a more modular and dynamic approach to service management. Upstart employed a more event-driven architecture, allowing for more responsive service startup and better management of dependencies between services.Upstart’s primary strength lies in its ability to handle more complex service interactions efficiently. It supports the notion of dependencies, allowing services to be started only after their prerequisite services have completed.
This modularity made it easier to manage intricate service relationships.
SysV init, the predecessor to both upstart and systemd, is a traditional approach to service management in Linux. It’s based on a simple runlevel system, where services are started or stopped based on the system’s operational mode (runlevel).
The strength of SysV init resided in its simplicity and widespread adoption across various distributions. Its straightforward configuration made it easier to understand and implement, though it lacked the advanced features of later init systems.
Auto-starting services reliably is crucial for any Linux system.
However, problems can arise, from simple typos to complex system configurations. Understanding these potential issues and how to diagnose them is essential for maintaining a stable and functional environment. This section will guide you through common problems, how to identify them, and effective troubleshooting steps.
Service startup failures can stem from various sources. Incorrect unit file configurations, dependencies not met, insufficient permissions, or even hardware issues can disrupt the boot process. Precise identification of the root cause is vital for effective resolution.
The systemd journal is a comprehensive log of system events, including service startup attempts. `journalctl` is a powerful tool for inspecting these logs, providing detailed information about service startup failures. It allows filtering, sorting, and searching for specific messages related to a particular service. This is critical in pinpointing the exact cause of a startup problem.
The following table Artikels common startup problems and their diagnostic steps:
Log messages often provide crucial clues about the cause of service startup failures. Here are some examples:
Explanation: This indicates that the system cannot find the unit file for the httpd service. Check if the file exists and has the correct path. Explanation: This often points to a problem with the systemd service manager’s ability to connect to a necessary daemon. Verify the daemon is running and check its logs for further clues. Explanation: The service process terminated unexpectedly. Check the service logs for any error messages that explain the reason for termination. Examine the service’s configuration for potential problems. Auto-starting services on boot offers convenience, but it introduces security risks if not implemented carefully. Malicious actors could exploit vulnerabilities in these services to gain unauthorized access or compromise the system. Understanding these risks and employing robust security measures are crucial for maintaining system integrity.
Careful configuration and proactive security measures are essential to mitigate potential threats when services are automatically started during boot. Ignoring these security considerations could leave the system susceptible to various attacks, impacting its overall stability and security posture.
Auto-starting services, especially those with network access or privileged permissions, introduce several security vulnerabilities. A compromised service can provide attackers with entry points to the system, potentially escalating privileges and causing significant damage. For example, a vulnerable service running as root could allow attackers to gain root access, leading to complete system compromise. Another risk is the possibility of unauthorized access to sensitive data through a compromised service.
Secure configuration is paramount when auto-starting services. Services should be configured with the least privilege possible, meaning they should only have the necessary permissions to perform their intended functions. Restricting network access to only necessary ports and IPs is vital. Using strong, unique passwords for service accounts is crucial, as well as implementing multi-factor authentication where feasible.
Regular security audits and vulnerability assessments are essential to identify and address potential weaknesses in service configurations.
Implementing secure configurations within systemd units is critical. Using appropriate user and group assignments is crucial, ensuring services run with minimal privileges. Limiting network access to specific IPs and ports, as well as enforcing strict firewall rules, is a key aspect of secure configuration. For example, a web server service should only listen on the designated port for external communication, preventing unauthorized access.
Regularly reviewing and updating service configurations to address any potential security gaps is essential for maintaining a strong security posture.
A well-defined security strategy is necessary to protect the system from various threats.
Systemd’s power extends far beyond basic service management. It allows for intricate control over service startup behavior, enabling precise configuration for diverse needs. This section delves into advanced options, including environment variables, command-line arguments, customized startup timing, dependency management, and advanced systemd directives. These features empower administrators to tailor service behavior to match specific system requirements and application needs.
Systemd’s flexibility empowers administrators to fine-tune services for optimal performance and reliability. This granular control enables precise management of service behavior, ensuring seamless integration with the wider system. By understanding and applying these techniques, you can optimize your system for specific needs and ensure smooth operation.
Environment variables and command-line arguments offer dynamic ways to customize services at startup. They allow passing data and configuration settings that modify service behavior without altering the service’s core code.
This dynamic approach allows services to adapt to varying system environments. For instance, a web server might use an environment variable to specify its listening port, or a database service might receive a command-line argument dictating its data directory. This flexibility is essential for applications that need to adjust to different configurations across various systems.
Systemd provides mechanisms to precisely control when services start. This is critical for maintaining service order and ensuring dependencies are met.
Using `TimeoutSec`, `RemainAfterExit`, and `StartLimitInterval` directives, you can set specific time limits and conditions for service startup. For instance, you can prevent a service from starting repeatedly within a certain timeframe. This control is essential for avoiding service conflicts or resource exhaustion. You can define startup delays or prevent multiple instances from launching simultaneously, improving stability.
Services often depend on other services to function properly. Systemd allows explicit definition of these dependencies. This feature is vital for maintaining the integrity of the system.
Using `Requires`, `Wants`, and `BindsTo` directives, you can define precise relationships between services. For example, a database service might require a network service to be up before starting. This ensures that crucial services start in the correct order, preventing errors and ensuring the system functions as expected. This structure guarantees a predictable and reliable startup sequence.
Systemd offers numerous directives for fine-grained control over service behavior. These directives can be utilized to optimize service startup and execution.
Using directives such as `EnvironmentFile`, `User`, `Group`, and `WorkingDirectory`, you can control the environment variables, user and group contexts, and working directory for a service. This customization allows services to operate within specific user contexts and environments. Understanding these directives is crucial for creating services that integrate smoothly with existing system security and resource management policies. For instance, `EnvironmentFile` allows for the dynamic loading of environment variables from external files, allowing greater flexibility.
In conclusion, mastering how to auto start services on boot in Linux empowers you to create a more efficient and reliable system. By understanding the various methods, particularly systemd’s powerful features, you can tailor your system’s startup to precisely meet your needs. This guide has provided a thorough overview, equipping you with the knowledge to troubleshoot any issues and safeguard your system.
Now you’re ready to optimize your Linux environment for optimal performance and reliability.
Controlling Service Startup Behavior
Step-by-Step Procedure to Create and Enable a Custom Service
Alternative Methods (upstart, SysV init)
Upstart
# /etc/init/myservice.conf (Upstart example)
start on runlevel [2345]
stop on runlevel [06]
script
echo "Starting myservice..."
/usr/bin/myservice start
end script
SysV init
# /etc/init.d/myservice (SysV init example)
#!/bin/sh
# Check for the existence of the script and its execution rights
if [ ! -x "$0" ]; then
echo "Error: Script not executable."
exit 1
fi
case "$1" in
start)
echo "Starting myservice..."
/usr/bin/myservice start
;;
stop)
echo "Stopping myservice..."
/usr/bin/myservice stop
;;
-)
echo "Usage: $0 start|stop"
exit 1
;;
esac
Comparison Table
Feature
systemd
upstart
SysV init
Example 1: Dependency Management
Sophisticated dependency graphs, ensuring proper order
More robust than SysV init, but not as sophisticated as systemd
Simple runlevels, lacking explicit dependencies
Example 2: Service Activation
Flexible and dynamic activation based on system events
Event-driven, enabling more responsive startups
Based on system runlevels, less dynamic
Flexibility
Highly flexible with a broad range of features
More flexible than SysV init, offering more advanced management
Limited flexibility, primarily focused on runlevels
Complexity
Higher complexity due to advanced features
Higher complexity than SysV init but lower than systemd
Lower complexity, but less adaptable to modern needs
Troubleshooting Common Issues
Common Service Startup Failures
Using `journalctl` to Examine Logs
journalctl. This displays a chronological log of all system events, including service startup attempts. journalctl -u httpd. This command will show only the entries related to the `httpd` service. journalctl -u httpd -p err -o cat | grep "permission denied" to narrow down the search to error messages containing “permission denied”. Identifying and Diagnosing Issues with Service Startup
Problem
Possible Cause
Troubleshooting Steps
Service fails to start
Incorrect unit file, missing dependencies, insufficient permissions, or resource constraints.
Verify the unit file for typos, ensure dependencies are met, check user and group permissions, and monitor system resources.
Service starts but does not function correctly
Configuration issues, resource limitations, or conflicts with other services.
Examine the service logs for error messages, check the configuration files, and identify any potential conflicts with other services. Monitor system resources.
Service starts, but then immediately stops
Resource conflicts, configuration errors, or problems with the service itself.
Examine the service logs, check the configuration file, and verify system resources. Restart the service and monitor its behavior.
Examples of Log Messages Indicating Startup Issues
Security Considerations
Potential Vulnerabilities and Risks
Best Practices for Securing Services
Secure Configurations for Auto-Starting Services
Security Risk Mitigation Strategies
Risk
Description
Mitigation
Unnecessary Permissions
Services running with excessive privileges, potentially enabling escalation of privileges.
Configure services to run with the least necessary permissions, limiting access to resources and sensitive data. Use non-root users and groups whenever possible.
Vulnerable Dependencies
Exploitable vulnerabilities in the libraries or packages used by the service.
Keep system and service dependencies up-to-date with the latest security patches. Regularly scan for vulnerabilities.
Improper Network Configuration
Lack of network access controls or inappropriate port openings, enabling unauthorized access.
Restrict network access to only necessary ports and IPs. Employ firewall rules to block unwanted traffic.
Weak Passwords
Using weak or easily guessable passwords for service accounts.
Implement strong, unique passwords for all service accounts. Consider using a password manager and implementing multi-factor authentication where possible.
Advanced Configurations and Customization: How To Auto Start Services On Boot In Linux
Environment Variables and Command-Line Arguments
Customizing Service Startup Timing
Configuring Service Dependencies
Advanced Systemd Directives, How to auto start services on boot in linux
Wrap-Up