Install ModSecurity on Nginx A Complete Guide
Install ModSecurity on Nginx: This comprehensive guide walks you through the process of securing your Nginx web server with ModSecurity. We’ll explore the fundamentals of ModSecurity, its integration with Nginx, and the various methods for installation and configuration. You’ll learn how to tailor ModSecurity rules to your specific needs, troubleshoot common issues, and optimize performance.
ModSecurity is an open-source web application firewall (WAF) that enhances the security of your web server by filtering malicious traffic. Integrating it with Nginx, a popular and high-performance web server, provides a robust defense against various attacks. This guide will detail the steps involved, from installation to configuration, allowing you to implement a strong security layer for your applications.
Introduction to ModSecurity and Nginx
ModSecurity is an open-source, web application firewall (WAF) that enhances the security posture of web applications. It acts as a crucial intermediary between web servers and applications, inspecting incoming traffic for malicious activity and blocking or mitigating threats before they reach the application. This proactive approach significantly reduces the risk of various attacks, protecting sensitive data and maintaining application integrity.Nginx, a high-performance web server, reverse proxy, and load balancer, is widely used for its efficiency and scalability.
Setting up ModSecurity on Nginx is a crucial step for web security, and it’s something I’ve been digging into lately. It’s all about beefing up your defenses against common attacks. Thinking about how Meghan Markle is reportedly seeking a fresh start on Instagram after a few challenging years as a duchess here , it made me ponder how important a clean slate can be for online security too.
Hopefully, this new security measure will keep my website safe and sound. It’s a fascinating technical challenge, and I’m excited to see the results.
Its architecture allows it to handle a large volume of concurrent connections, making it suitable for demanding web applications. Crucially, Nginx’s modular design enables seamless integration with security extensions like ModSecurity, further bolstering its defensive capabilities.
Benefits of Integrating ModSecurity with Nginx, Install modsecurity on nginx
Integrating ModSecurity into Nginx provides substantial security enhancements. By placing ModSecurity in front of the application, Nginx acts as a shield, filtering out harmful requests before they reach the application server. This approach protects the application from a wide range of attacks, reducing the load on the application server and improving overall performance. This combination allows for more robust protection against malicious attacks without compromising the speed and efficiency of the web server.
Types of Attacks ModSecurity Mitigates
ModSecurity can mitigate a diverse range of attacks, including cross-site scripting (XSS), SQL injection, cross-site request forgery (CSRF), and command injection. It also protects against more sophisticated attacks like session hijacking and denial-of-service (DoS) attacks by scrutinizing the requests and responses. This proactive approach significantly reduces the risk of data breaches and application vulnerabilities.
ModSecurity and Nginx Version Compatibility
Proper version compatibility between ModSecurity and Nginx is critical for optimal performance and security. Incorrect versions can lead to incompatibility issues, preventing ModSecurity from functioning as intended. A well-maintained system with appropriate versions of both components ensures seamless security and performance.
| ModSecurity Version | Nginx Version | Compatibility Notes |
|---|---|---|
| ModSecurity 3.x | Nginx 1.14.x and above | ModSecurity 3.x is generally compatible with newer Nginx versions. Refer to ModSecurity documentation for specific compatibility details. |
| ModSecurity 4.x | Nginx 1.18.x and above | ModSecurity 4.x is often compatible with more recent Nginx versions. Consult official documentation for exact requirements. |
| ModSecurity 3.x (older versions) | Older Nginx versions | Compatibility may vary; older versions may require configuration adjustments or compatibility libraries. |
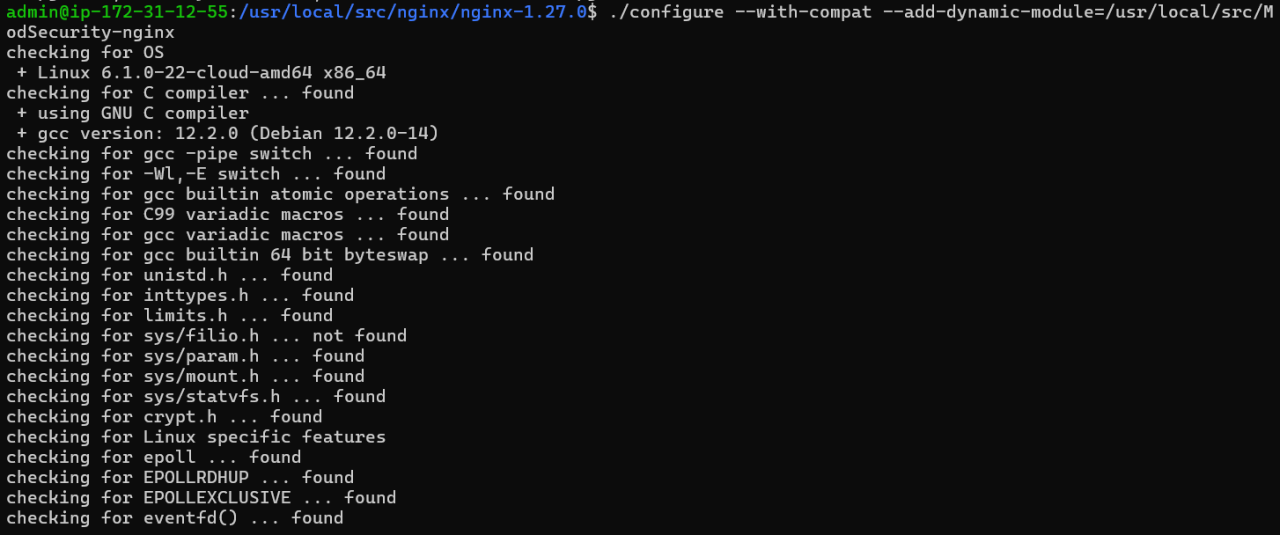
Installing ModSecurity on Nginx
ModSecurity is a powerful web application firewall (WAF) that can significantly enhance the security of your Nginx web server. Installing it correctly is crucial for leveraging its protection. This section will Artikel various installation methods and guide you through the process.Installing ModSecurity on Nginx can be achieved through several methods, each with its own advantages and disadvantages. Understanding these differences allows you to select the most suitable approach for your specific environment.
Package Manager Installation
Using a package manager like apt-get (Debian/Ubuntu) or yum (CentOS/RHEL) is often the simplest method for installing ModSecurity. It automates the download, installation, and configuration of the necessary packages, minimizing manual intervention.
- Debian/Ubuntu (apt-get): This method typically involves updating the package list, then installing the necessary ModSecurity package for your Nginx version. Example commands might include:
sudo apt update
sudo apt install libapache2-modsecurity
Note that the package name may vary slightly depending on the specific distribution and version. Always check the package repository for the most current and accurate information. - CentOS/RHEL (yum): A similar approach applies for CentOS/RHEL systems, using the yum package manager. The command structure mirrors that of apt-get. The installation command will vary depending on the exact package name and repository.
sudo yum update
sudo yum install mod_security
Compilation from Source
While more involved, compiling ModSecurity from source offers greater control over the installation process. It allows for customization and the ability to install specific versions tailored to your Nginx setup. However, this method requires familiarity with command-line tools and potentially the compilation of additional prerequisites.
- Prerequisites: Before compiling, ensure you have the necessary development tools and libraries installed. These will vary depending on your operating system and version of Nginx. For instance, you might need to install build tools, C compilers, and libraries related to your specific Nginx configuration.
- Obtaining the Source Code: Download the latest ModSecurity source code from the official website or repository. Following the instructions for downloading and unpacking the source code will be critical.
- Compilation and Installation: The compilation process typically involves using a make command, which will build the ModSecurity modules. Specific commands will vary greatly depending on the version and setup, so always consult the ModSecurity documentation for your exact configuration.
Installation and Configuration
Once ModSecurity is installed, configure it to work with your Nginx server. This typically involves editing Nginx configuration files to include the necessary directives to enable ModSecurity.
The configuration typically includes the ModSecurity load module, as well as rules for detecting and preventing various types of web attacks.
Comparison of Installation Methods
| Installation Method | Pros | Cons |
|---|---|---|
| Package Manager | Simpler, automated installation; usually less error-prone. | Limited control over configuration; may not always have the latest version. |
| Compilation from Source | Greater control over configuration and version; potential for customization. | More complex, requires familiarity with command-line tools; potential for errors during compilation. |
Configuring ModSecurity Rules

ModSecurity’s power lies not just in its installation but in its configuration. Properly configured rules are crucial for tailoring security measures to specific application needs, effectively blocking malicious traffic while allowing legitimate users through. This involves understanding the various rule sets and how to leverage them to create a robust defense against a wide range of threats.Effective ModSecurity configuration involves selecting the right rules and configuring them to match specific vulnerabilities or patterns of attack.
This granular approach ensures a more focused security posture, reducing false positives and optimizing performance. By understanding common attack vectors and their corresponding ModSecurity rules, administrators can fine-tune security responses.
Common ModSecurity Rules and Their Effects
ModSecurity rules are written in a specialized syntax. They define conditions that, if met, trigger specific actions. Common rules include those that detect SQL injection attempts, cross-site scripting (XSS) vulnerabilities, and various HTTP protocol violations. For instance, a rule might examine incoming requests for specific strings or patterns associated with SQL injection, triggering a block action if found.
Rule Sets for ModSecurity
ModSecurity offers a variety of rule sets, each focusing on different aspects of web application security. These sets often cover common vulnerabilities, and administrators can select the sets that best address their application’s specific security needs.Choosing the right rule set is crucial for maintaining optimal performance and minimizing false positives. A rule set tailored for a high-traffic e-commerce site will likely differ from one used for a low-traffic personal blog.
Careful consideration is vital to avoid blocking legitimate users or slowing down legitimate requests. Selecting a rule set that aligns with the application’s specific threats and security requirements is essential.
Configuring ModSecurity to Block Specific Attacks
Configuring ModSecurity to block specific attacks involves writing or selecting rules that match the attack patterns. For example, to block SQL injection attempts, a rule would be designed to identify malicious SQL code within incoming requests. This rule would trigger a block action upon detection.Configuring ModSecurity to block specific attacks involves careful rule design. For example, to block a known exploit, a rule would be crafted to identify the specific attack pattern.
This includes not only the exact strings or patterns but also their context within the request.
ModSecurity Rule Categories and Use Cases
Understanding the different categories of ModSecurity rules allows for more targeted and effective configuration. Each category serves a specific purpose in web application security.
| Rule Category | Description | Example Rule |
|---|---|---|
| SQL Injection Prevention | Prevents malicious SQL code from being executed. | SecRule ARGS:QUERY_STRING "^.*'; DROP TABLE users; --.*$" "phase:2,id:100,nolog,capture,t:none,t:none,auditlog,deny,msg:'SQL Injection attempt'" |
| Cross-Site Scripting (XSS) Prevention | Prevents attackers from injecting malicious scripts into web pages. | SecRule REQUEST_HEADERS:User-Agent "^.*
|