Password Cracking with Hashcat A Deep Dive
Password cracking with hashcat is a powerful technique used to recover passwords from hashed data. This guide delves into the intricacies of hashcat, exploring its functionality, methodology, and crucial considerations for ethical and responsible use. We’ll cover everything from the fundamentals of password cracking to advanced techniques like wordlist and mask attacks, configuration, and performance optimization.
Understanding hashcat’s capabilities and limitations is vital. This exploration covers the different hash types hashcat supports, providing a comparison of various versions. We’ll also delve into the various attack methods hashcat employs, from brute-force to dictionary attacks, illustrating the practical steps for setting up a testing environment and demonstrating the use of wordlists and mask attacks.
Introduction to Hashcat
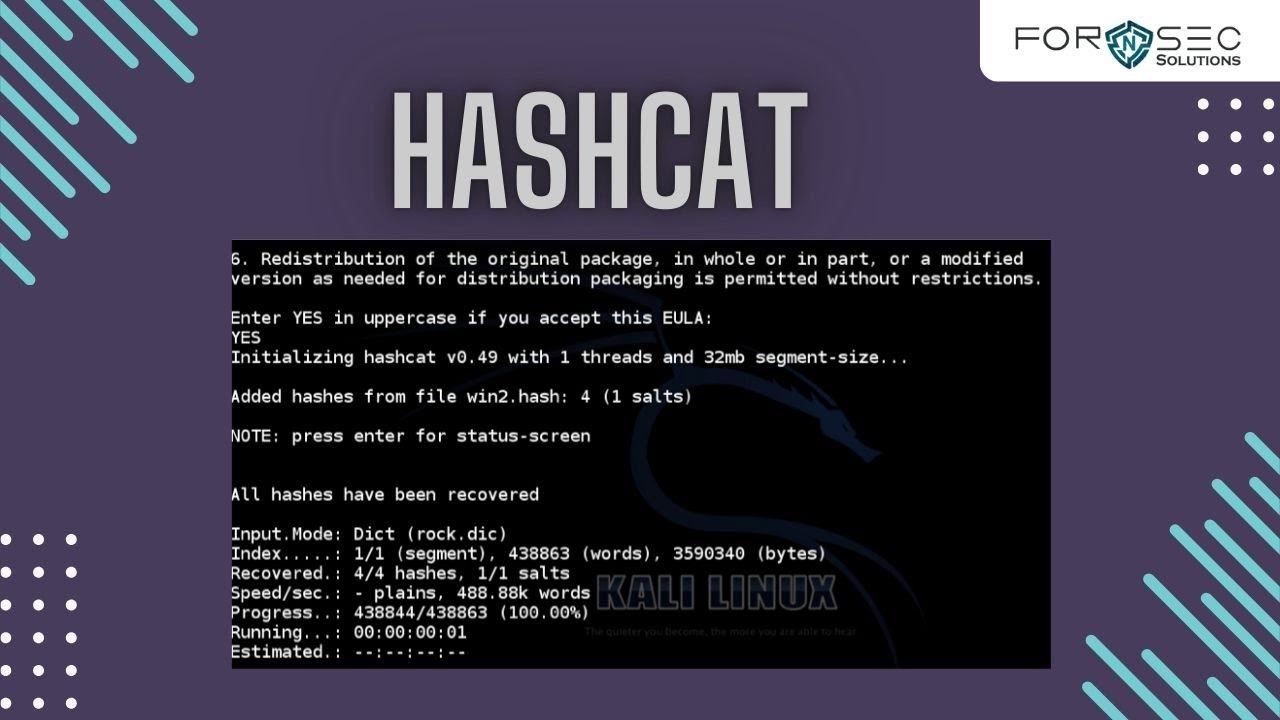
Hashcat is a powerful open-source password recovery tool. It’s widely used by security professionals, penetration testers, and researchers to crack passwords by attempting to match known hash values with potential password candidates. Its versatility lies in its ability to handle various hashing algorithms, making it a crucial tool in forensic investigations and vulnerability assessments.Hashcat’s core function is to efficiently test a vast number of potential passwords against a target hash.
This brute-force approach, combined with dictionary attacks and custom wordlists, enables it to recover passwords from compromised systems. The effectiveness of Hashcat hinges on the quality and size of the password lists used in attacks.
Hash Types Handled by Hashcat
Hashcat supports a wide array of hashing algorithms, making it a valuable tool for diverse security scenarios. This extensive support is critical for handling various types of compromised data, allowing analysts to recover passwords from systems using different hashing methods. Commonly supported hash types include:
- MD5: A widely used but now outdated hashing algorithm. Its vulnerability to collisions makes it unsuitable for modern security applications.
- SHA-1: An older, less secure SHA variant, also prone to collisions and cracking.
- SHA-256, SHA-512: More robust hashing algorithms, still used in many modern systems. Hashcat can handle these, but cracking them takes more time and resources.
- bcrypt, Argon2: Modern, strong hashing algorithms designed to resist brute-force attacks. These are often used for password storage in secure systems.
- LM, NTLM: Legacy Windows authentication hashes. Hashcat can be used to recover passwords from systems using these protocols, but cracking them may still be feasible.
- MySQL, PostgreSQL, Oracle, vBulletin, and many others: Hashcat’s versatility extends to various database systems and proprietary applications.
Fundamental Concepts of Password Cracking
Password cracking relies on the comparison of candidate passwords against a known hash. This comparison involves transforming the candidate password into a hash using the same algorithm the original password was hashed with. If the generated hash matches the target hash, the candidate password is considered a valid match.
Hashcat leverages this principle by attempting a large number of candidate passwords until a match is found. Its speed and efficiency in performing this process are key to its effectiveness.
Hashcat Versions and Features
The following table Artikels the features and improvements in different Hashcat versions. The improvements illustrate the ongoing development and enhancements aimed at increasing the tool’s capabilities and performance.
Learning password cracking with hashcat is pretty cool, but it’s also important to remember that using these tools ethically is crucial. While exciting new retail spaces are being planned on key downtown San Jose blocks, like this one , it’s equally vital to understand responsible security practices. This knowledge about cracking passwords with hashcat can help secure systems and prevent cyberattacks.
| Version | Supported Hash Types | Notable Improvements |
|---|---|---|
| Hashcat 3.0 | Various common hash types | Initial release, laying the foundation for future development. |
| Hashcat 4.0 | Expanded support, including newer algorithms | Improved performance and efficiency in handling complex hashes. |
| Hashcat 4.x (current versions) | Extensive coverage of modern and legacy hashing algorithms. | Continuous enhancements, bug fixes, and optimizations for speed and reliability. |
Hashcat’s Methodology
Hashcat, a powerful password cracking tool, employs various attack methods to recover passwords from hashed data. Understanding these methods is crucial for assessing the security of systems and implementing appropriate countermeasures. Its flexibility and adaptability to different password structures are key factors in its effectiveness.
Attack Methods Supported
Hashcat supports a range of attack strategies, including brute-force, dictionary, and hybrid attacks. These methods vary in their approach and efficiency, making them suitable for different situations. Each method targets specific vulnerabilities in the password hashing process.
- Brute-Force Attacks: These attacks systematically try every possible combination of characters within a specified character set, up to a certain length. This method is computationally intensive and can take a considerable amount of time, especially for complex passwords.
- Dictionary Attacks: These attacks leverage pre-compiled wordlists containing common passwords, usernames, and combinations. They are more efficient than brute-force attacks when passwords follow predictable patterns. These attacks can be highly effective for weak passwords.
- Hybrid Attacks: These combine elements of brute-force and dictionary attacks. They are often used to improve the speed and efficiency of cracking passwords.
Brute-Force Attack Process
A brute-force attack using Hashcat involves systematically testing all possible character combinations. The process begins by defining the character set and the password length. Hashcat then generates all possible combinations and compares them against the hashed password. This exhaustive search is time-consuming but can be effective against weak passwords.
Handling Different Password Types
Hashcat can handle various password structures. It can accommodate alphanumeric passwords, passwords containing special characters, and mixed-case passwords. The user defines the character set during the attack configuration.
- Alphanumeric Passwords: These passwords typically use a combination of letters and numbers. Hashcat can easily handle these types of passwords by considering all possible combinations of letters and numbers within the specified length.
- Special Characters: Hashcat can incorporate special characters (e.g., !@#$%^&*) into the character set during the attack. This ensures that all possible combinations with special characters are tested.
- Mixed-Case Passwords: Hashcat can also test passwords containing both uppercase and lowercase letters. It generates combinations considering the case sensitivity of the password.
Attack Strategies
Hashcat employs various attack strategies to optimize the cracking process. These strategies include wordlist attacks and mask attacks.
- Wordlist Attacks: These attacks utilize pre-compiled wordlists. The tool checks the wordlist against the target hash. This approach is efficient when passwords follow predictable patterns.
- Mask Attacks: Mask attacks allow the user to define a template for the password using special characters (e.g., `?` for any character, `#` for a number, `a` for ‘a’). This significantly reduces the number of combinations needed to be tested while targeting a particular pattern in the password.
Setting Up a Basic Hashcat Environment
To set up a basic Hashcat environment for testing, you need to install Hashcat on your system. This generally involves downloading the appropriate binary for your operating system and placing it in a convenient location. Next, you need the target hash and a wordlist or mask if needed.
Wordlists and Mask Attacks
Wordlists are fundamental to password cracking with Hashcat. They act as a dictionary of potential passwords, allowing Hashcat to systematically test against a target hash. A well-crafted wordlist can significantly improve the chances of success in a penetration test or security audit. Effective wordlist creation and management is critical for efficient and targeted attacks.
Significance of Wordlists
Wordlists provide a crucial starting point for password cracking. Hashcat iterates through each entry in the wordlist, attempting to match it against the target hash. The quality and relevance of the wordlist directly impact the success rate and efficiency of the cracking process. A comprehensive wordlist increases the likelihood of finding a valid password. Conversely, an insufficient or irrelevant wordlist can lead to wasted time and resources.
Creating and Managing Wordlists
Several methods exist for creating and managing wordlists. These methods vary depending on the target and the type of attack being performed. One common method involves using pre-existing wordlists, such as those found online. However, these often contain generic passwords and are less effective against strong or personalized passwords. A more targeted approach involves creating a customized wordlist based on known information about the target.
This could include common misspellings, concatenations of common words, or even leveraging information from leaked data breaches.
Hashcat’s a powerful tool for cracking passwords, but the complexities of modern revenue-sharing models, like those being debated by the rebuilt PAC 12 in their rebuilt pac 12 pondering minimum investment standards in revenue sharing era , highlight the need for equally sophisticated security measures. Ultimately, understanding these intricate financial models is crucial for safeguarding sensitive data, just as understanding hashcat’s algorithms is vital for robust password security.
Tailoring Wordlists for Specific Targets
To enhance the effectiveness of a wordlist, tailor it to the specific target. Consider the type of user, company, or industry. For example, a wordlist for a financial institution might include financial terms, account numbers, or employee names. If the target is a specific individual, information about their hobbies, interests, or family members might be useful. The more precise the wordlist, the greater the likelihood of success.
Wordlist Formats and Their Properties
| Format | Strengths | Weaknesses |
|---|---|---|
| Simple text files (e.g., .txt) | Easy to create and manage, widely supported by tools. | Can be less efficient for complex attacks, no built-in structure. |
| Custom formats (e.g., using specific delimiters or structures) | Can be more efficient for complex attacks and reduce noise | May require specific tools or scripts to parse the data |
| Dictionaries | Include common words and their variations. | May not be effective against more complex or personalized passwords. |
| Pattern-based lists | Suitable for attacks based on common password patterns. | Limited applicability to complex passwords. |
Mask Attacks with Hashcat
Mask attacks are a powerful technique for password cracking with Hashcat. They leverage wildcards to create a set of possible passwords based on a pattern or template. This significantly reduces the time required to test all combinations. This approach is very effective when you have partial information about the password. Consider using wildcard characters like `?` (for a single character) or `*` (for multiple characters) in a mask.
A mask attack is more efficient than a complete brute-force attack.
Example of Mask Attack
For instance, a mask attack could target passwords like `passwOrd123`, `p@$$wOrd`, or `Pa$$wOrd123`. Hashcat can use the mask `passwOrd???` to find similar passwords. The `?` wildcard represents any single character. This approach can significantly speed up the cracking process by reducing the number of combinations that need to be tested.
Hashcat’s Configuration and Usage
Hashcat, a powerful password cracking tool, boasts a vast array of options for tailoring its behavior to various situations. Mastering these options allows for optimized performance and efficiency in diverse scenarios. This section delves into the intricacies of configuring Hashcat, providing practical examples and a structured guide for effective utilization.Understanding Hashcat’s command-line options is paramount to leveraging its full potential.
These options, meticulously crafted, enable precise control over the cracking process, ranging from selecting the attack type to specifying the wordlist and hardware resources.
Hashcat Command-Line Options
The command-line interface is the primary method for interacting with Hashcat. A multitude of options are available, allowing for intricate configurations. The `-a` option, for instance, dictates the attack type, while `-w` specifies the wordlist. Understanding and correctly utilizing these options is critical for effective password cracking.
- -a: This option specifies the attack type, ranging from simple dictionary attacks to more complex mask attacks. Different attack types cater to various scenarios and levels of complexity. For instance, a simple dictionary attack (`-a 0`) utilizes a pre-defined wordlist, while a mask attack (`-a 3`) uses a template to generate variations.
- -w: This option is crucial for specifying the wordlist file to be used. The wordlist contains a collection of potential passwords, and the choice of wordlist directly impacts the effectiveness of the attack. A comprehensive wordlist, including common passwords, special characters, and variations, is key to success.
- -m: This option is used to specify the hash type. Different hash types require different methods for cracking, and choosing the correct hash type is essential for success.
- -o: This option directs Hashcat to output the results to a specified file. This file will contain the cracked passwords, along with relevant details.
- -r: This option allows Hashcat to read a configuration file, enabling automation and simplifying complex setups.
- -O: This option controls the number of threads, significantly influencing performance. The optimal number of threads depends on the hardware resources, particularly the number of CPU cores.
Optimizing Hashcat Performance
Several options contribute to maximizing Hashcat’s performance. Choosing the right combination of options is crucial for achieving optimal results.
- Thread Optimization: The number of threads directly impacts performance. On multi-core processors, increasing the number of threads can improve speed, but it’s crucial to avoid exceeding the available CPU cores. Excessive threads can lead to performance degradation.
- Hardware Utilization: Hashcat’s performance is heavily influenced by the hardware resources available. A machine with more CPU cores, a faster processor, and more RAM will generally result in faster cracking times.
- Wordlist Selection: A targeted wordlist is more effective than a generic one. Tailoring the wordlist to the specific target system can significantly increase the chances of success.
Practical Hashcat Usage Examples
These examples demonstrate the application of Hashcat for various scenarios.
- Simple Dictionary Attack: To crack SHA-256 hashes using a wordlist named `passwords.txt`, use the command:“`hashcat -a 0 -m 1000 -w passwords.txt hashes.txt“`This command performs a dictionary attack on the SHA-256 hashes stored in `hashes.txt` using the wordlist `passwords.txt`. The `-m 1000` parameter specifies the hash type.
- Mask Attack: To crack hashes using a mask, use the following command:“`hashcat -a 3 -m 1000 –show ‘abc?xyz’ hashes.txt“`This example uses a mask attack on SHA-256 hashes, specifying the mask `abc?xyz`. The `–show` flag displays the matched passwords.
Hashcat Configuration for Different Situations
Hashcat’s adaptability extends to various hardware configurations. Proper configuration ensures optimal performance.
- Single-Core Systems: On single-core systems, running Hashcat with a single thread (`-O 1`) is optimal to avoid unnecessary overhead.
- Multi-Core Systems: On multi-core systems, increasing the number of threads (`-O`) up to the number of CPU cores can significantly improve speed.
- Large Datasets: For large datasets, using a configuration file (`-r`) to automate the process is beneficial. This allows for a more structured and manageable approach.
Configuring Hashcat for a Given Wordlist
A step-by-step guide for configuring Hashcat for a specific wordlist is as follows:
- Identify the hash type: Determine the hash type (e.g., SHA-256, MD5). This information is crucial for correct Hashcat operation.
- Select an attack type: Decide on the appropriate attack type (e.g., dictionary attack, mask attack). This will depend on the nature of the target system.
- Choose the wordlist: Select the wordlist (`-w`) that best suits the attack scenario. A tailored wordlist will yield better results.
- Specify the hash file: Input the hash file (`hashes.txt`) containing the encrypted passwords.
- Run Hashcat: Execute the Hashcat command with the specified options.
Practical Considerations and Security Implications
Hashcat, a powerful tool for password cracking, offers valuable insights into the vulnerabilities of systems. However, its use necessitates a deep understanding of ethical considerations, legal boundaries, and responsible practices. Misuse can lead to severe consequences, while responsible application can foster a stronger understanding of cybersecurity.Understanding the potential for misuse and the need for ethical application of tools like Hashcat is paramount.
Using this tool without adhering to ethical guidelines and legal boundaries can have severe consequences.
Ethical Implications of Using Hashcat
The ethical use of hashcat hinges on respecting digital property rights and avoiding unauthorized access. Using this tool for cracking passwords of systems without explicit permission constitutes a violation of ethical and often legal standards.
Importance of Responsible Use and Avoiding Illegal Activities
Responsible use of hashcat is critical. It is essential to obtain explicit permission from the system owner before attempting any password cracking. Furthermore, unauthorized access to systems or data is illegal and carries severe penalties. Examples include fines, imprisonment, and reputational damage.
Legal Aspects of Password Cracking, Password cracking with hashcat
Password cracking, even for legitimate purposes like security audits, requires adherence to legal frameworks. Laws regarding unauthorized access to systems vary by jurisdiction and should be meticulously reviewed before conducting any cracking activities. Unauthorized access, even with permission to test, can result in legal ramifications.
Handling Cracking Results Responsibly and Ethically
Handling cracking results requires careful consideration. When testing system security, it’s crucial to document all findings, including vulnerabilities and exploited weaknesses, in a detailed report. This report should be shared with the system owner and used to strengthen security measures. Ethical use of the tool dictates the responsible handling of discovered weaknesses.
Learning how to crack passwords with tools like hashcat is a fascinating but potentially dangerous skill. Understanding these techniques can help you secure your own systems, but it’s also crucial to stay informed about the latest security vulnerabilities. To truly grasp the broader context of cybersecurity, exploring resources like internet of things iot learning resources can provide a valuable perspective.
Ultimately, the knowledge gained from both practical tools and theoretical understanding is vital for responsible and effective password cracking analysis.
Strategies for Mitigating Password Cracking Risks
Various strategies exist to mitigate the risks associated with password cracking. These strategies range from strengthening password policies to implementing robust security measures, such as multi-factor authentication and intrusion detection systems. These strategies address the vulnerabilities that make systems susceptible to attacks.
- Strong Password Policies: Implementing policies that encourage users to create complex and unique passwords is a fundamental step. These policies should emphasize the importance of strong passwords and how to create them.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring more than one authentication factor (e.g., password plus a code from a mobile device). This makes it harder for attackers to gain access even if they manage to crack a password.
- Intrusion Detection Systems (IDS): IDSs monitor network traffic for suspicious activity and can alert administrators to potential attacks, giving them time to respond.
Methods for Strengthening Password Security
Strengthening password security is crucial in mitigating the risks of password cracking. This involves implementing a combination of strong password policies, multi-factor authentication, and robust security measures. User education is also vital in preventing attacks.
- Regular Password Changes: Enforcing regular password changes helps to limit the impact of compromised passwords.
- Password Managers: Password managers can generate and store complex passwords, making it easier for users to maintain strong credentials.
- Principle of Least Privilege: Limiting access to only the necessary resources reduces the impact of a compromised account.
Potential Vulnerabilities of Different Systems to Hashcat Attacks
Systems with weak hashing algorithms or outdated software are vulnerable to hashcat attacks. Older systems or systems with default configurations often lack robust security measures. Modern systems, with advanced encryption and authentication protocols, are generally more resistant.
| System Type | Vulnerability | Mitigation |
|---|---|---|
| Systems with weak hashing algorithms | Hashcat can easily crack passwords | Upgrade to stronger hashing algorithms |
| Outdated software | Exploitable vulnerabilities | Keep software up-to-date |
| Systems with default configurations | Lack of security measures | Configure security settings |
Hashcat’s Performance and Optimization

Hashcat’s performance is heavily dependent on the underlying hardware and the specific algorithms employed. Optimizing its usage for different scenarios can significantly impact the speed and efficiency of cracking attempts. Understanding these factors and implementing appropriate strategies are crucial for successful password recovery.Hashcat’s speed isn’t solely determined by the power of the CPU; it’s a complex interplay of hardware resources, algorithm choices, and the specific data being processed.
Different cracking methods and wordlists require varying levels of computational effort. Effective optimization considers these elements to maximize efficiency and reduce time-to-solution.
Hardware Considerations
Factors like the CPU’s architecture, number of cores, and clock speed, along with the GPU’s processing power and memory, significantly influence hashcat’s performance. Modern CPUs and GPUs offer varying degrees of parallel processing capabilities. Leveraging these capabilities through appropriate settings in hashcat is critical for optimal performance.
- CPU Architectures: Different CPU architectures, like x86-64, ARM, or others, may affect hashcat’s performance depending on the optimized code base for that particular architecture. Older architectures may show slower results compared to modern processors.
- GPU Utilization: Utilizing GPUs, if available, dramatically increases hashcat’s cracking capacity. Hashcat’s GPU mode can perform massive parallel computations, accelerating the process significantly, especially for complex passwords or large wordlists.
- RAM Capacity: Sufficient RAM is crucial for hashcat, especially when handling large wordlists or complex masks. Insufficient RAM can lead to swapping, which significantly slows down the process. Allocating sufficient RAM is essential for efficient operation.
Algorithm Selection
Hashcat offers various algorithms, each with its strengths and weaknesses in handling different types of hash functions. Selecting the appropriate algorithm is essential for optimal performance.
- Algorithm Suitability: Algorithms like `BF` (Brute-Force), `Hybrid`, and `Mask` have varying efficiencies for different types of passwords. A brute-force attack is suited for simple passwords, whereas a hybrid approach may be better for a combination of character sets.
- Tuning for Specific Hashes: Some algorithms are more optimized for specific hash types (like bcrypt or Argon2). Choosing the algorithm best suited for the hash type will generally yield better performance.
Optimizing Hashcat’s Configuration
Hashcat’s configuration plays a vital role in optimizing its performance. Adjusting settings based on the hardware and the target hashes is crucial for speed and efficiency.
- Thread Management: Adjusting the number of threads to match the CPU’s core count can improve performance. Using more threads than cores can lead to performance degradation due to increased overhead. Optimizing the thread count is crucial for utilizing the available processing power effectively.
- Memory Allocation: Adjusting memory allocation according to the size of the wordlist and the hash data can prevent memory bottlenecks. This ensures the hashcat process runs smoothly and avoids potential performance drops due to memory constraints.
- Hardware-Specific Options: Leveraging hardware-specific options, such as GPU acceleration, can significantly speed up cracking processes. Activating these options can greatly improve performance, especially when dealing with extensive data sets.
Parallelization Strategies
Parallelization is a key aspect of optimizing hashcat’s speed. Utilizing multiple cores and/or GPUs allows for simultaneous processing, drastically reducing the time required for cracking.
- Multi-Core Processing: Hashcat’s ability to utilize multiple CPU cores is crucial for speed. Leveraging multiple cores enables parallel processing, significantly accelerating the password cracking process.
- GPU Acceleration: Utilizing GPUs offers an even greater degree of parallelism. This approach can dramatically reduce the time needed to crack hashes, especially when dealing with large or complex passwords. The availability of suitable GPUs directly affects the potential performance gain.
Effective Use on Different Hardware
Matching hashcat’s configuration to the specific hardware (CPU, GPU, RAM) is crucial for optimal performance.
- CPU-Based Cracking: For CPU-based cracking, the thread count should align with the number of CPU cores. Over-threading can lead to performance degradation.
- GPU-Based Cracking: Optimizing GPU settings for specific hardware configurations is important. Adjusting the GPU memory allocation to the available memory on the GPU can prevent performance issues.
Last Word: Password Cracking With Hashcat
In conclusion, password cracking with hashcat, while a powerful tool, requires careful consideration of ethical implications and legal aspects. Responsible use, a strong understanding of the tool’s capabilities, and knowledge of security best practices are paramount. We’ve explored the various facets of hashcat, from its core functionality to advanced techniques and performance optimization. Ultimately, the aim is to empower users with the knowledge to leverage this tool effectively while upholding ethical and legal standards.