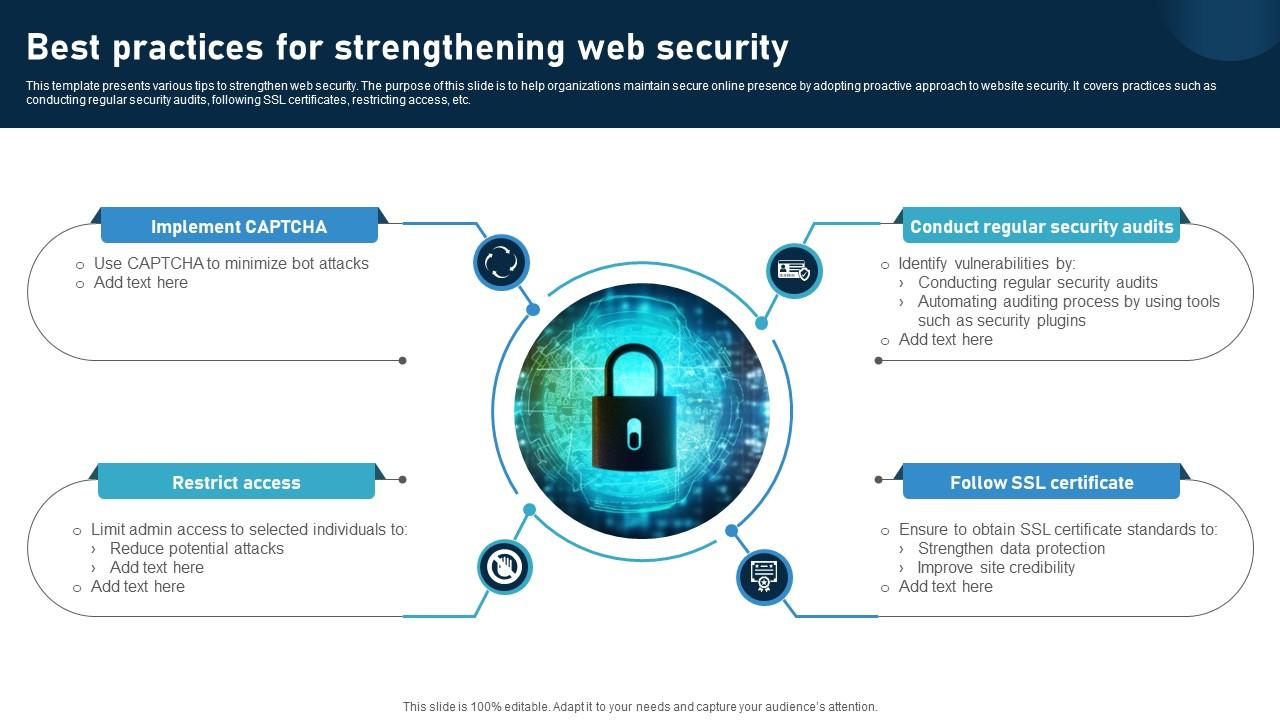
Website Security Best Practices A Deep Dive
Website security best practices are crucial for any online presence. From fundamental protocols like HTTPS to securing user data and implementing robust security measures, a strong defense is paramount. This exploration dives into the essential steps for safeguarding your website from various threats, including common attacks like SQL injection and cross-site scripting.
We’ll cover everything from choosing secure hosting to handling security incidents, ensuring your website remains a safe and reliable platform for users. Understanding vulnerabilities and implementing proactive security measures is key to protecting your site and users’ sensitive information. This guide will walk you through essential practices, empowering you to make informed decisions for a more secure online experience.
Fundamentals of Website Security
Protecting websites from malicious attacks is crucial in today’s digital landscape. A robust security posture safeguards sensitive user data, maintains the integrity of the site, and builds trust among users. A well-designed security strategy considers various layers, from the infrastructure to the application code. This understanding is essential for developers and website administrators alike.A strong foundation in website security relies on a comprehensive approach, encompassing both technical measures and proactive strategies.
This includes understanding the underlying vulnerabilities and employing appropriate security protocols to mitigate potential risks. A holistic view of website security fosters a resilient online presence.
Core Security Principles
Website security is built upon several fundamental principles. These principles are interconnected and should be considered in a holistic approach to website security. Security should be integrated into every phase of the development lifecycle. These principles include, but are not limited to, the principles of least privilege, defense in depth, and a proactive approach to threat detection and response.
Security Protocols, Website security best practices
Robust security protocols play a critical role in protecting sensitive user data. These protocols provide a secure channel for communication between the user’s browser and the website’s server. HTTPS, using TLS/SSL encryption, is fundamental for protecting user data. This protocol encrypts the communication between the browser and the server, preventing eavesdropping and tampering with data. This encryption is vital for safeguarding information such as passwords, credit card details, and other sensitive data.
Proper configuration and implementation of these protocols are paramount for effective security.
Vulnerabilities and Exploits
Website vulnerabilities are weaknesses in the system that attackers can exploit to gain unauthorized access or cause damage. These vulnerabilities can range from flaws in the application code to misconfigurations in the server infrastructure. Understanding these vulnerabilities is essential to mitigating potential attacks. Thorough security testing and penetration testing can help identify vulnerabilities before they are exploited.
Strong website security practices are crucial, especially when dealing with sensitive data. Thinking about the recent volatility in the cannabis industry, like the challenges and opportunities presented by cannabis stocks under Trump’s administration, cannabis stocks under trump challenges and opportunities highlights the need for robust online defenses. After all, a secure website protects not only your data but also your reputation.
Types of Website Attacks
Various types of attacks target websites, ranging from simple denial-of-service attacks to sophisticated exploits targeting specific vulnerabilities. Understanding these attacks and their potential consequences is critical for developing effective countermeasures.
| Attack Type | Description | Potential Consequences |
|---|---|---|
| SQL Injection | Attackers inject malicious SQL code into user input fields, manipulating database queries to gain unauthorized access or modify data. | Data breaches, unauthorized access to sensitive information, data modification, website defacement. |
| Cross-Site Scripting (XSS) | Attackers inject malicious scripts into web pages viewed by other users, allowing them to steal session cookies, redirect users to malicious sites, or perform other malicious actions. | Session hijacking, data theft, phishing attacks, website defacement. |
| Denial-of-Service (DoS) | Attackers flood the website with traffic, overwhelming the server and making it unavailable to legitimate users. | Service disruption, loss of revenue, damage to reputation, potential for data loss. |
| Malware Infections | Attackers inject malicious code into the website, often through compromised plugins or files. | Data breaches, website defacement, compromise of user accounts, potential for data loss. |
Protecting User Data

Protecting user data is paramount in today’s digital landscape. Compromised user information can lead to significant financial losses, reputational damage, and legal repercussions for both individuals and organizations. Robust security measures are essential to safeguard sensitive data from unauthorized access, use, disclosure, disruption, modification, or destruction.Effective data protection strategies go beyond simply implementing security measures; they require a comprehensive understanding of the potential threats and a proactive approach to mitigating risks.
This involves understanding the various types of user data, the methods used to collect and store it, and the potential vulnerabilities associated with each stage of the data lifecycle. This detailed approach ensures that sensitive information remains confidential, accessible only to authorized users, and is handled with the utmost care.
Password Security Strategies
Robust password security is crucial for protecting user accounts and sensitive data. Weak or easily guessed passwords are a primary vector for unauthorized access. Implementing strong password practices is a fundamental aspect of user authentication.
- Strong Passwords: Creating strong passwords involves using a combination of uppercase and lowercase letters, numbers, and symbols. The length of the password is also critical, with longer passwords being significantly more secure. A strong password should be at least 12 characters long and include a diverse set of characters.
- Password Managers: Password managers are specialized software applications that generate, store, and manage passwords securely. They eliminate the need to memorize numerous passwords, reducing the risk of password reuse and making it easier to maintain strong passwords across multiple accounts. This approach significantly enhances the overall security posture of user accounts.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security to user accounts by requiring multiple verification methods beyond a simple password. This could involve receiving a one-time code via SMS, authenticator app, or biometric verification. This greatly reduces the risk of unauthorized access even if a password is compromised.
Data Encryption and Storage
Protecting sensitive data, such as credit card details and personal information, necessitates employing robust encryption techniques. Encryption converts readable data into an unreadable format, making it virtually impossible for unauthorized individuals to access the information.
- Data Encryption in Transit: Encrypting data during transmission (e.g., when a user enters their credit card information on a website) prevents eavesdropping and unauthorized access by third parties. Secure protocols like HTTPS are essential for this purpose. This ensures the confidentiality of data throughout its transmission.
- Data Encryption at Rest: Encrypting data stored in databases or on file systems ensures that even if the storage system is compromised, the data remains protected. This practice is crucial for safeguarding sensitive information when it’s not actively being used.
- Secure Storage Solutions: Choosing secure storage solutions, such as secure servers with robust access controls and regular security audits, is vital for maintaining the confidentiality of user data. These measures prevent unauthorized access to the storage system and protect data integrity.
User Authentication and Authorization
Effective user authentication and authorization processes are essential to control access to sensitive data and applications. These procedures verify the identity of users and grant them access only to the resources they are permitted to use.
- Authentication Methods: Authentication methods verify the identity of users. Common methods include username/password combinations, multi-factor authentication, and biometric authentication. Choosing the appropriate method depends on the sensitivity of the data and the level of security required.
- Authorization Policies: Authorization policies define which users have access to specific resources. These policies establish clear guidelines for data access, ensuring that only authorized personnel can access sensitive information.
Password Management Strategies Comparison
| Strategy | Effectiveness | Advantages | Disadvantages |
|---|---|---|---|
| Strong Passwords | Low | Simple to implement | Difficult to remember, prone to reuse |
| Password Managers | High | Generates strong passwords, securely stores passwords, auto-fills forms | Requires software installation and potentially subscription |
| Multi-Factor Authentication | High | Adds an extra layer of security | Requires user setup and can be inconvenient |
Implementing Security Measures
Building a secure web application requires a multifaceted approach. Simply having strong passwords and encryption isn’t enough. A robust security strategy involves proactively implementing measures at various stages of the development lifecycle, from design to deployment. This proactive approach involves understanding and addressing potential vulnerabilities, anticipating threats, and implementing safeguards to mitigate risks.Security measures should be integrated into the entire software development lifecycle (SDLC).
This includes identifying potential vulnerabilities during the design phase, implementing appropriate security controls during development, and conducting thorough security testing before deployment. Security should be a core consideration throughout the project, not an afterthought.
Securing Web Applications Against Common Threats
Web applications are susceptible to various attacks, including cross-site scripting (XSS), SQL injection, and cross-site request forgery (CSRF). Implementing robust input validation and output encoding is crucial in preventing these vulnerabilities. These measures, when properly implemented, can effectively mitigate these risks and significantly improve the overall security posture of the application.
Input Validation
Input validation is a fundamental security technique that involves checking user-supplied data to ensure it conforms to expected formats and constraints. This process is critical in preventing malicious input from compromising the application’s integrity. For example, validating user input to ensure it adheres to specific length requirements, data types, and formats can prevent attacks like SQL injection and cross-site scripting.
Output Encoding
Output encoding is equally important. It involves transforming data before displaying it to the user. This transformation prevents the application from interpreting malicious code as part of the output. This crucial step prevents XSS attacks by escaping special characters, ensuring that potentially harmful input is rendered harmlessly within the context of the application’s output.
Security Headers
Implementing appropriate security headers can significantly enhance the security of web applications. These headers provide a layer of defense against various attacks, including cross-site scripting (XSS) and cross-site request forgery (CSRF). Security headers, such as Content-Security-Policy (CSP) and X-Frame-Options, are essential for securing the application from attacks that exploit vulnerabilities in the browser. These headers are critical in protecting against malicious content and unauthorized access attempts.
Security Testing Methodologies
Security testing is a crucial component of any secure web application development. Thorough testing methodologies help identify vulnerabilities before they can be exploited. This proactive approach prevents significant issues and potential financial or reputational damage.
Penetration Testing
Penetration testing involves simulating real-world attacks to identify vulnerabilities in the application. Ethical hackers use various techniques to try and gain unauthorized access, providing valuable insights into potential weaknesses. This process, often involving multiple attempts to exploit potential vulnerabilities, can uncover blind spots in security defenses.
Vulnerability Scanning
Automated vulnerability scanning tools are used to identify known vulnerabilities in the application’s code and configuration. This automated process helps to identify security flaws before they are exploited by malicious actors. Scanning tools frequently check for known vulnerabilities in the code, library dependencies, and configurations to proactively identify and mitigate potential security risks. Vulnerability scanning is a critical proactive measure in ensuring the application’s safety and integrity.
Security Testing and Audits
Securing your website is an ongoing process, not a one-time fix. Regular testing and audits are crucial for identifying and mitigating potential vulnerabilities before they can be exploited. This proactive approach ensures your site remains resilient against evolving threats.Thorough security testing and audits are essential to assess the effectiveness of your implemented security measures. They provide a realistic view of your system’s resilience to attacks and help you identify weaknesses that automated scans may miss.
This proactive approach allows for the identification and remediation of security flaws, ultimately strengthening your website’s overall security posture.
Different Security Testing Methods
Various methods exist for assessing website security. Understanding their strengths and limitations helps in choosing the right approach for specific needs. Each method offers unique insights into different aspects of security, allowing for a comprehensive evaluation.
- Penetration Testing (Pen Test): A simulated attack on your system to identify vulnerabilities. Ethical hackers attempt to exploit weaknesses, mimicking real-world attacks, to determine the potential impact and exploitability of vulnerabilities. This method often reveals complex vulnerabilities that automated scans might miss.
- Vulnerability Scanning: Automated tools scan your website for known vulnerabilities in software, configurations, and other security issues. These tools often identify common flaws but may not be effective in finding more advanced or customized attacks. This method provides a quick overview of potential risks.
- Security Audits: A systematic review of your website’s security policies, procedures, and controls. This includes examining the implementation of security measures, access controls, and the overall security architecture. This method provides a holistic view of your security posture, identifying gaps in your overall strategy.
- Source Code Review: A manual or automated examination of the source code to identify potential security flaws. This method often uncovers vulnerabilities that automated tools might miss, particularly those arising from programming errors or design flaws. This approach helps ensure security is built into the very fabric of the application.
Importance of Regular Audits and Penetration Testing
Regular security audits and penetration testing are vital for maintaining a secure website. These assessments are essential to stay ahead of evolving threats and ensure the website’s ongoing resilience against potential attacks. They highlight security flaws, which if left unaddressed, can lead to significant breaches.Regular testing and audits allow for a proactive approach to security management. This means identifying weaknesses and vulnerabilities before malicious actors can exploit them.
This approach prioritizes the long-term security of the site.
Identifying and Fixing Security Vulnerabilities
The process of identifying and fixing vulnerabilities involves a structured approach. It begins with a thorough assessment, followed by remediation and validation.
- Vulnerability Identification: Utilize security testing methods to pinpoint vulnerabilities. This step involves analyzing the results of penetration tests, vulnerability scans, and audits. The process involves understanding the implications of each vulnerability.
- Risk Assessment: Evaluate the potential impact of each identified vulnerability. This step involves considering the likelihood of exploitation, the potential damage, and the overall risk to the website and its users. The outcome helps in prioritizing remediation efforts.
- Remediation: Implement fixes for identified vulnerabilities. This involves patching software, configuring security controls, and implementing appropriate security measures. Effective remediation is key to minimizing risks.
- Validation: Verify that the implemented fixes effectively address the vulnerabilities. This involves retesting the website to ensure the vulnerabilities are no longer present. This crucial step confirms the effectiveness of the security measures.
Secure Coding Practices
Proper coding practices can prevent many common vulnerabilities. Implementing these practices during development helps to reduce the likelihood of security issues later. This proactive approach minimizes the risk of common vulnerabilities.
“Input validation is crucial. Always sanitize user inputs to prevent injection attacks.”
For example, validating user input prevents SQL injection attacks. This means ensuring that user-supplied data is properly sanitized and checked before it is used in queries. This critical step prevents attackers from manipulating queries and gaining unauthorized access.
Security Updates and Maintenance
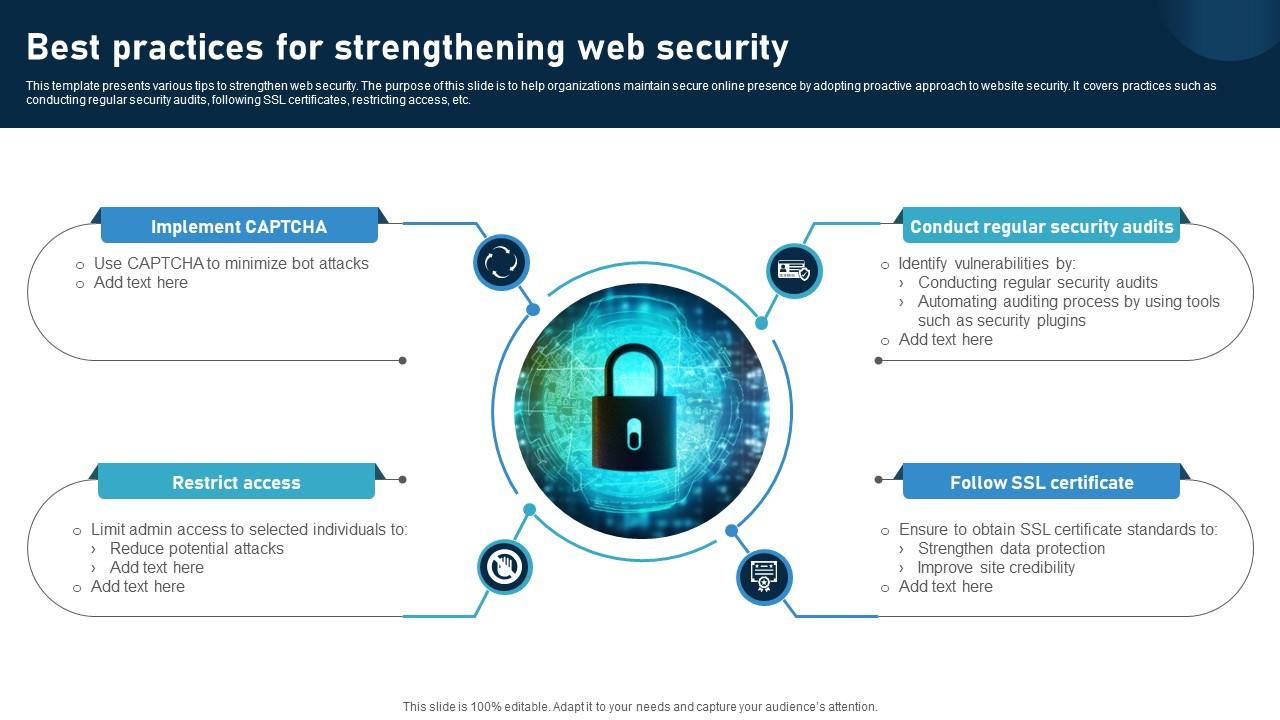
Staying ahead of evolving cyber threats requires a proactive approach to website security. Regular updates and maintenance are crucial for patching vulnerabilities and ensuring the continued resilience of your online presence. Ignoring these essential steps can leave your site susceptible to exploitation, leading to data breaches, reputational damage, and significant financial losses.The digital landscape is constantly shifting, and cybercriminals are always developing new techniques to exploit weaknesses.
Implementing robust security update and maintenance procedures is paramount to mitigating these threats and safeguarding your website and user data.
Importance of Software Updates and Patches
Software updates and patches are essential for addressing security vulnerabilities. These updates often contain critical fixes that eliminate known exploits, thereby significantly strengthening the security posture of your website. Failing to apply these updates exposes your site to potential attacks, allowing attackers to potentially gain unauthorized access, compromise data, and disrupt operations. Cybersecurity incidents involving unpatched software are frequently reported, highlighting the criticality of staying current.
Identifying and Implementing Security Updates
Proactive identification of necessary security updates is crucial. Regularly checking for available updates from software vendors is a vital step. Automated systems and tools can significantly streamline this process, making it easier to track updates and ensure timely implementation. A vulnerability management system is a useful tool in this regard, helping to prioritize and address vulnerabilities based on their potential impact.
Furthermore, security advisories and bulletins from reputable sources provide crucial information about potential risks and the associated solutions.
Best Practices for Maintaining a Secure Website Environment
Maintaining a secure website environment requires a multi-faceted approach. Regular backups are essential to ensure data recovery in case of security incidents or system failures. Access controls should be carefully managed, limiting access to authorized personnel only. Security awareness training for personnel involved in website management is critical to educate them about potential threats and best practices.
Employing robust firewalls and intrusion detection systems to monitor and block malicious traffic is also a critical part of a well-rounded security strategy.
Timeline for Routine Security Checks and Updates
Regular security checks and updates are vital to maintain a strong security posture. A consistent schedule helps ensure vulnerabilities are addressed promptly. This schedule should be customized based on the specific needs and risk profile of the website.
| Task | Frequency | Description |
|---|---|---|
| Software Update Check | Weekly | Verify for available updates from all software components. |
| Security Patch Application | Bi-Weekly | Apply all identified critical security patches immediately. |
| Vulnerability Scan | Monthly | Conduct automated vulnerability scans to identify potential weaknesses. |
| Security Audit | Quarterly | Perform a comprehensive security audit to assess overall security posture. |
| Backup Verification | Weekly | Verify the integrity of recent backups to ensure data recovery capabilities. |
Security Awareness and Training
A strong website security posture isn’t just about technical measures; it’s equally vital to cultivate a culture of security awareness among both administrators and users. Proactive training empowers individuals to recognize and avoid potential threats, significantly bolstering the overall defense against malicious actors. This proactive approach is crucial to prevent common attacks and to minimize the impact of breaches.Security awareness training equips individuals with the knowledge and skills to identify and mitigate security risks.
It fosters a collective responsibility for safeguarding sensitive data and the website itself. This shared understanding translates to a stronger overall security posture.
Keeping your website secure is crucial, especially these days. Robust security measures are vital for protecting sensitive data. Interestingly, recent reports show a significant decline in Tesla sales in California, with the Model 3 plunging 36% here. While this might seem unrelated, it highlights the importance of safeguarding online assets, no matter the industry.
Strong website security practices remain paramount.
Importance of Training for Administrators
Website administrators are the gatekeepers of security, responsible for implementing and maintaining security measures. Thorough training empowers them to make informed decisions about security policies, technologies, and procedures. This includes understanding the latest attack vectors, vulnerability assessments, and incident response protocols. Administrators are the first line of defense, and proactive training keeps them informed and equipped.
Importance of Training for Users
User training is equally vital. Users often interact with the website more frequently than administrators, making them a potential point of vulnerability. Empowering users with security best practices reduces the risk of falling victim to phishing scams and social engineering attacks. Educating users about secure passwords, recognizing suspicious emails, and safe browsing practices directly contributes to a more resilient website environment.
Examples of Phishing and Social Engineering Attacks
Phishing attacks often involve deceptive emails or websites that mimic legitimate entities. These attacks aim to trick users into revealing sensitive information, such as login credentials or credit card details. A common example is an email that appears to be from a bank, requesting account verification. Another example involves a malicious link disguised as a legitimate download.Social engineering attacks leverage psychological manipulation to gain access to sensitive information.
Attackers may impersonate trusted individuals or exploit users’ natural inclination to trust, such as a seemingly legitimate request from a colleague. A simple example is a phone call from a seemingly legitimate technical support representative claiming a system issue and requesting access to credentials. A more sophisticated attack might involve a carefully crafted message exploiting a user’s personal circumstances or fears.
Educating Users About Security Best Practices
Educating users about security best practices is paramount. This involves clear communication of security protocols and risks. Training should be engaging and accessible, utilizing various mediums like interactive modules, videos, and infographics. Emphasis should be placed on recognizing phishing attempts, creating strong passwords, and maintaining secure browsing habits.
Implementing a Security Awareness Training Program
Implementing a comprehensive security awareness training program requires a structured approach. A phased rollout, tailored to different user groups, is recommended. This approach ensures that the training is relevant and effective.
- Establish clear training objectives. These objectives should be specific, measurable, achievable, relevant, and time-bound (SMART).
- Develop engaging and interactive training materials. Use various formats like videos, quizzes, and simulations to maintain user interest and comprehension.
- Schedule regular training sessions. Regular reinforcement through periodic updates is critical to maintain knowledge retention.
- Track and measure training effectiveness. Monitor user participation and assess knowledge retention to evaluate the program’s success.
Regular training and reinforcement are essential to build a strong security culture and mitigate risks.
Choosing Secure Hosting and Infrastructure: Website Security Best Practices
Selecting a secure web hosting provider and setting up a robust infrastructure are crucial for safeguarding your website and user data. A compromised hosting environment can expose your entire site to vulnerabilities, leading to data breaches and reputational damage. Therefore, careful consideration must be given to every aspect of the hosting and infrastructure setup.A strong hosting platform acts as the bedrock of your online presence.
It’s not just about storage space; it’s about the security measures employed by the provider and the ability to implement your own robust defenses. This includes the technical capabilities to safeguard against threats, and the level of support available to address potential issues.
Factors to Consider When Choosing a Hosting Provider
Choosing the right hosting provider goes beyond simply picking the cheapest option. Key factors include the provider’s security posture, their commitment to patching vulnerabilities, and the level of support they offer. A reliable provider will have robust security measures in place, such as firewalls, intrusion detection systems, and regular security audits. Their commitment to staying ahead of evolving threats is equally important.
- Security Features: Look for providers with robust security features like firewalls, intrusion detection systems (IDS), and regular security audits. These features help to protect against unauthorized access and malicious activities. A provider’s security policies should be clearly documented and regularly updated.
- Vulnerability Management: A reliable provider proactively addresses security vulnerabilities. This includes promptly patching known weaknesses and implementing measures to prevent future exploits. Regular updates and security patches are crucial to maintaining a secure environment.
- Server Security: The provider’s server security measures are paramount. This includes the type of hardware, operating system, and the security protocols used. Ensure the provider utilizes up-to-date security practices and has a proven track record of preventing attacks.
- Support and Expertise: Reliable support and expertise are critical in case of security incidents. A provider with knowledgeable support staff can assist in troubleshooting and resolving issues quickly. Look for providers with a dedicated security team or support channels.
Comparing Different Hosting Providers
A comparative analysis of hosting providers based on their security features can help make an informed decision. Different providers offer varying levels of security, and a thorough comparison is essential.
| Hosting Provider | Firewall | IDS | Security Audits | Support Response Time |
|---|---|---|---|---|
| Provider A | Yes (Advanced) | Yes (Proactive) | Quarterly | Within 24 hours |
| Provider B | Yes (Basic) | No | Annually | Within 48 hours |
| Provider C | Yes (Advanced) | Yes (Reactive) | Monthly | Within 12 hours |
Note: This table is a simplified representation and may not encompass all the features of each provider. Always consult the provider’s documentation for a complete overview.
Strong website security practices are crucial, especially with the rise of online threats. Think about the importance of robust passwords and regular updates. Interestingly, a recent article about Harry Diamond, a caddie, found on harry diamond caddie wikipedia , highlights the need for security in all areas, from professional sports to the digital realm. Ultimately, prioritizing website security is essential for protecting user data and maintaining trust.
Secure Infrastructure Setup
A secure infrastructure involves more than just the hosting provider. Implementing a firewall, load balancers, and intrusion prevention systems (IPS) on your server adds another layer of protection. These components play a crucial role in preventing attacks and managing traffic effectively.
- Firewall: A firewall acts as a gatekeeper, controlling network traffic and blocking unauthorized access attempts. It’s a critical component for safeguarding your website from malicious traffic.
- Load Balancers: Distributing traffic across multiple servers prevents overload and enhances resilience. This helps in maintaining website availability and performance, even under high traffic conditions.
- Intrusion Prevention Systems (IPS): IPS continuously monitors network traffic for malicious activities and blocks suspicious traffic in real-time. This proactive approach helps in mitigating potential threats.
Impact of Server-Side Security Measures
Server-side security measures significantly impact the overall security of a website. These measures protect the core infrastructure, ensuring that data remains secure and accessible only to authorized users. By implementing these measures, you reduce the risk of vulnerabilities and enhance the overall security posture of your website. This proactive approach strengthens the defense against threats and protects user data.
Handling Security Incidents
A website’s security posture is only as strong as its response to threats. A robust incident response plan is crucial for minimizing damage and restoring operations quickly following a security breach or incident. This section details essential procedures for handling such events effectively.Effective incident response goes beyond simply reacting to a problem; it’s about proactively anticipating potential threats and establishing clear procedures for handling them.
A well-defined plan will guide the organization through each step, from initial detection to complete recovery.
Incident Response Planning
A comprehensive incident response plan is a critical safeguard. It Artikels procedures for identifying, containing, eradicating, recovering, and learning from security incidents. This plan serves as a roadmap, ensuring a coordinated and efficient response. A well-structured plan will clearly define roles and responsibilities, allowing individuals to act quickly and decisively. This includes documenting the expected response, communication protocols, and escalation paths for different severity levels of incidents.
Incident Detection and Reporting
Early detection is paramount for containing the impact of a security incident. Establishing clear reporting procedures and monitoring systems is essential. This includes automated alerts and designated personnel for promptly reviewing security logs and monitoring systems for suspicious activities. Security information and event management (SIEM) tools can aid in automating this process, while designated personnel ensure human oversight to avoid false positives.
Incident Containment and Mitigation
Containing a security incident involves immediately limiting the damage and preventing further exploitation. This may include isolating affected systems, disabling compromised accounts, and implementing temporary security measures. A comprehensive plan will dictate how to contain the impact, minimize data loss, and prevent the incident from escalating. The goal is to halt the spread of the threat and prevent further compromise of sensitive data.
This involves understanding the scope of the incident and implementing measures to prevent further data breaches.
Incident Eradication and Recovery
Once containment is established, eradication focuses on removing the threat and restoring systems to a secure state. This includes identifying and patching vulnerabilities, restoring data from backups, and implementing security enhancements to prevent future occurrences. The recovery phase focuses on getting back to normal operations while also ensuring that security protocols are strengthened. This involves a detailed plan for restoring systems, applications, and data to their previous state.
This also includes a plan to ensure that all necessary security controls are in place and that any vulnerabilities identified during the incident are addressed.
Post-Incident Analysis and Improvement
Post-incident analysis is crucial for learning from the experience and preventing similar incidents in the future. This includes conducting a thorough review of the incident response process, identifying weaknesses, and implementing improvements to the plan. Analyzing the incident will help to understand the root cause, identify any vulnerabilities, and determine how the response could be improved. A detailed report of the incident, including the root cause, the impact, and the corrective actions taken, should be documented for future reference.
Example Incident Response Flow Chart
| Step | Action |
|---|---|
| Detection | Identify suspicious activity in logs or alerts. |
| Containment | Isolate affected systems, disable compromised accounts. |
| Eradication | Identify and patch vulnerabilities, restore data. |
| Recovery | Restore systems to normal operations. |
| Analysis | Review the incident, identify lessons learned. |
End of Discussion
In conclusion, safeguarding your website involves a multifaceted approach encompassing security protocols, user data protection, implementation strategies, and ongoing maintenance. By understanding and implementing these best practices, you can significantly reduce the risk of security breaches and ensure a trustworthy online environment for both your business and your users. Regular updates, awareness training, and proactive incident response are key components of a robust security posture.
Remember, website security is an ongoing process, not a one-time fix.