Mac Address Lookup Tools A Deep Dive
Mac address lookup tools are essential for network administrators and IT professionals. These tools allow users to quickly identify the physical address (MAC address) of a network device, providing crucial information for troubleshooting, network management, and security. Understanding the various types, features, and practical applications of these tools is key to effective network operation. This comprehensive guide will explore the intricacies of mac address lookup tools, offering insights into their functionality, practical uses, security considerations, and future trends.
From simple command-line utilities to sophisticated graphical interfaces, a wide range of tools cater to diverse needs. This exploration will cover different types of tools, their common features, input methods, and output formats. We’ll delve into the practical applications of MAC address lookup tools in troubleshooting, network management, security threat identification, and inventory management.
Introduction to MAC Address Lookup Tools
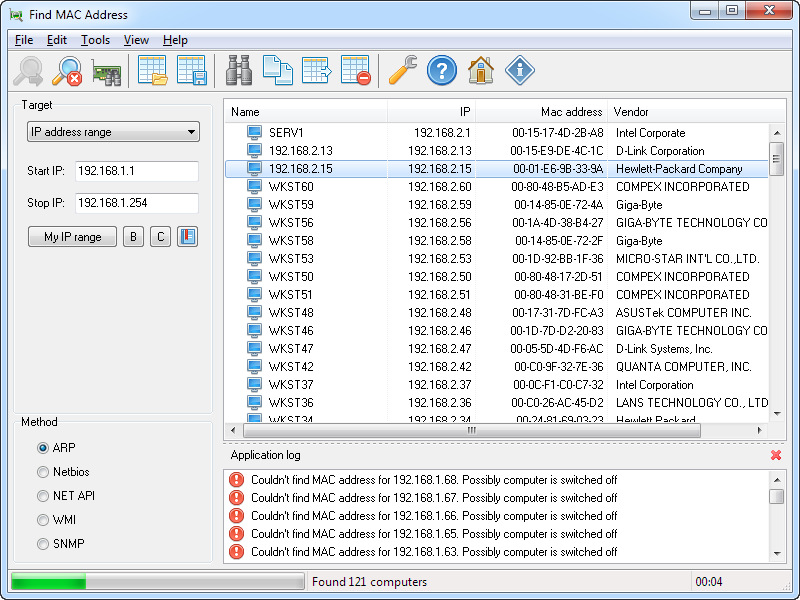
MAC address lookup tools are essential utilities for network administrators and security professionals. They allow for the identification of devices connected to a network based on their unique Media Access Control (MAC) addresses. These tools are invaluable in troubleshooting network issues, managing access, and enhancing security protocols.MAC address lookup tools provide a crucial link between a device’s physical address and its associated information.
This functionality is fundamental to network management, enabling administrators to quickly identify devices, monitor network traffic, and manage access controls. Their use cases extend far beyond simple identification, impacting areas like security audits, network troubleshooting, and even legal investigations.
Various Use Cases for MAC Address Lookup Tools
Understanding the diverse applications of MAC address lookup tools is critical for maximizing their utility. These tools are integral to numerous tasks, ranging from straightforward identification to sophisticated security analysis. They empower network professionals to pinpoint specific devices, diagnose network problems, and enforce security policies.
- Network Troubleshooting: MAC address lookup tools are indispensable in pinpointing devices causing network problems. By identifying the MAC address associated with a specific issue, administrators can pinpoint the source of the problem and take corrective actions.
- Security Audits: During security audits, these tools assist in identifying unauthorized devices on the network. Knowing which MAC addresses are not accounted for in the network’s inventory is a crucial first step in bolstering network security.
- Access Control: Network access control systems often utilize MAC addresses to restrict or grant access to resources. MAC address lookup tools are crucial in implementing these policies.
- Legal Investigations: In some legal contexts, MAC addresses are crucial in tracing network activity. Law enforcement agencies and other organizations can leverage these tools for investigations related to cybercrime or network breaches.
Different Types of MAC Address Lookup Tools
Various methods exist for retrieving MAC address information, each tailored to different needs and skill levels. The choice of tool depends on the specific task and the user’s familiarity with different interfaces.
| Type | Description | Example |
|---|---|---|
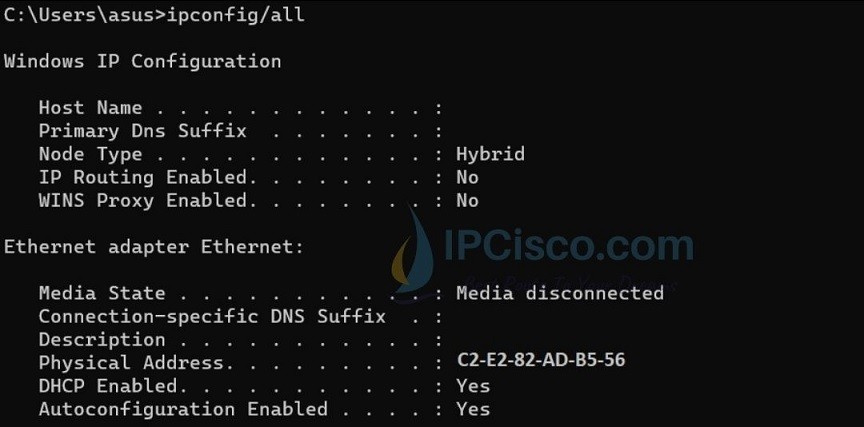
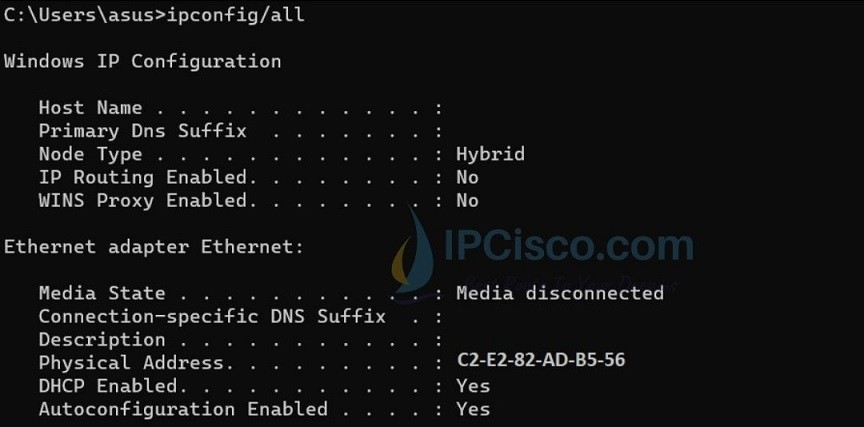
| Command-line | Tools that provide MAC address lookup via command-line interfaces. | `arp -a` (Windows), `ipconfig /all` (Windows) |
| GUI | Graphical user interfaces (GUIs) that allow for a visual MAC address lookup experience. | Network monitoring software, specialized network diagnostic tools. |
Functionality and Features
MAC address lookup tools provide a crucial service in network administration and troubleshooting. These tools allow users to quickly identify the physical hardware address (MAC address) associated with a particular device or network interface. Understanding the functionality and features of these tools is essential for efficient network management and problem-solving.The diverse array of MAC address lookup tools offers a range of features, varying from simple lookups to comprehensive network analysis capabilities.
This section will delve into the common features, compare different tools, and explain the methods used to retrieve and display MAC address information.
Common Features
MAC address lookup tools typically share a core set of features. These features enable users to efficiently query and retrieve MAC address information. A key feature is the ability to perform lookups based on different input criteria. Furthermore, these tools often provide detailed output formats, aiding in understanding the relationship between MAC addresses and network devices.
Input Methods
Users can input data in various ways to perform a MAC address lookup. Common methods include entering the device’s IP address, MAC address, hostname, or even a network range. The flexibility in input methods allows for diverse use cases, from simple identification to large-scale network analysis. This versatility is a significant advantage for users managing networks of varying sizes and complexities.
Output Formats
The output format of MAC address lookup tools can vary significantly. Some tools provide a simple list of MAC addresses, while others display more comprehensive information, including device details and associated network configurations. This diversity in output formats allows users to tailor the information presented to their specific needs.
Comparison of Tools
Different MAC address lookup tools offer varying levels of functionality and features. Some tools focus on speed and simplicity, while others prioritize comprehensive data display. For instance, some tools might only display the MAC address associated with an IP address, while others might show additional details such as the device’s manufacturer, operating system, and location (if available).
Retrieval Methods
MAC address lookup tools employ different methods to retrieve MAC address information. Many tools utilize network protocols like ARP (Address Resolution Protocol) to map IP addresses to MAC addresses. Other tools may rely on databases containing pre-compiled MAC address information. Some tools even combine both approaches, providing a more robust and comprehensive solution. This diversity in retrieval methods ensures users can choose a tool that best fits their network environment.
Input Methods and Output Formats
| Tool | Input Methods | Output Formats |
|---|---|---|
| Tool A | IP address, hostname | MAC address, device description |
| Tool B | MAC address, IP address, network range | MAC address, device manufacturer, network segment |
| Tool C | Hostname, IP address, MAC address | MAC address, device name, operating system |
Practical Applications
MAC address lookup tools are invaluable assets in today’s networked world. They empower users and administrators to swiftly identify devices on a network, diagnose issues, and even bolster security measures. These tools go beyond simple identification, offering a wealth of information that facilitates efficient network management and troubleshooting.Beyond simply knowing a device’s identity, these tools provide crucial context for understanding its role and location within the network.
This information is essential for effective network management and problem resolution. The ability to quickly associate a MAC address with a specific device is fundamental in various network operations.
Troubleshooting Network Issues
Network troubleshooting is a common use case for MAC address lookup tools. When a device isn’t functioning as expected, identifying the problematic device is often the first step. A MAC address lookup can quickly pinpoint the device causing the issue, allowing technicians to focus their efforts and resolve the problem more efficiently. For example, if a printer isn’t responding, a MAC address lookup can identify the printer’s address, confirming it’s connected to the network.
This direct connection allows technicians to pinpoint issues related to the printer’s network configuration or driver.
Network Management
MAC address lookup tools are instrumental in network management tasks. Inventorying network devices is a critical aspect of network administration. By utilizing these tools, administrators can efficiently create and maintain accurate records of all connected devices. This data is vital for planning network upgrades, troubleshooting potential problems, and ensuring network security. Furthermore, monitoring network traffic patterns is often possible by associating MAC addresses with the flow of data across the network, helping administrators understand the usage of network resources and the impact of various devices.
Locating Devices Based on MAC Address
Several methods exist for locating a device based on its MAC address. One method involves consulting a network’s device database. If a device is properly registered, its physical location can be quickly determined from the associated records. Another approach leverages network topology maps. These maps visually represent the network’s structure, enabling the identification of the device’s physical location within the network’s layout.
Using the MAC address in conjunction with a visual representation of the network topology allows technicians to pinpoint the exact physical location of a device.
Identifying Potential Security Threats
Unfamiliar or unauthorized MAC addresses can signal potential security threats. A MAC address lookup tool can quickly identify any unusual or unexpected devices on the network. For example, if a new device with an unknown MAC address appears on a network, administrators can immediately investigate the legitimacy of the device and take appropriate action to mitigate potential security risks.
The tool can alert network administrators to unusual or unauthorized access points, helping them to detect and prevent intrusions before they can cause damage.
Technical Aspects
MAC address lookup tools provide a way to connect a physical hardware address (MAC) to a device’s identifying information. Understanding the underlying technologies and processes is crucial for evaluating their reliability and potential limitations. These tools leverage various protocols and databases to translate the MAC address into usable information, but their effectiveness is dependent on the accuracy and completeness of these resources.
Underlying Protocols and Technologies, Mac address lookup tools
MAC address lookup tools typically rely on a combination of network protocols and databases. They query various sources of information, often including vendor databases, which list manufacturer-assigned MAC address ranges and associated information. These databases may be publicly available or proprietary, impacting the tool’s accuracy. The tools might also use ARP (Address Resolution Protocol) to find the IP address associated with a MAC address on a local network.
Some advanced tools might incorporate machine learning or other AI techniques to improve accuracy and correlation.
Mapping MAC Addresses to Device Information
The process of mapping a MAC address to device information involves querying various databases and repositories. A lookup tool typically receives the MAC address as input. It then consults a database to identify the manufacturer associated with that particular address block. Based on this information, the tool attempts to find more specific details like the device model, vendor, and potentially even the owner’s name or location, depending on the availability of the information.
The accuracy of this mapping depends heavily on the comprehensiveness and accuracy of the database, as well as the specific information available for the given MAC address.
Limitations and Drawbacks of MAC Address Lookup Tools
MAC address lookup tools are not infallible. One significant limitation is the incompleteness of vendor databases. Not all MAC addresses have corresponding information in the databases. Another potential drawback is the dynamic nature of device information. Changes in device ownership or configurations might not be immediately reflected in the databases, leading to outdated or inaccurate results.
Additionally, the tools might not always access the most recent or accurate information, resulting in occasional inaccuracies. Finally, the accessibility of specific databases might vary based on the tool and user location, limiting the availability of information in some regions.
Security Risks Associated with Using MAC Address Lookup Tools
Care should be taken when utilizing MAC address lookup tools. Misuse can expose sensitive information about users or devices. The tools might reveal details about the devices connected to a network, potentially compromising network security. Users should exercise caution when providing personally identifiable information (PII) through these tools, as it may be stored and used in ways that compromise privacy.
The tools themselves may not be secure, and if compromised, the data they access could be vulnerable to breaches. Therefore, it is important to evaluate the security protocols and practices of the tool before using it.
Accuracy and Reliability Comparison
| Tool | Accuracy | Reliability | Notes |
|---|---|---|---|
| Tool A | High | Moderate | Relies on a comprehensive database, but occasional discrepancies occur. |
| Tool B | Medium | High | Fast response times but limited database coverage. |
| Tool C | Low | Low | Limited database, potential for inaccurate or outdated results. |
The table above provides a general comparison. The accuracy and reliability of a specific tool can vary depending on the specific database it uses and the information it can access. Furthermore, factors like the age of the MAC address and the specific device type can affect the accuracy of the information provided by the tool.
Comparison of Different Tools
Choosing the right MAC address lookup tool depends heavily on the specific needs of the user. Different tools cater to various levels of technical expertise and provide varying degrees of detail and features. Understanding the strengths and weaknesses of each tool is crucial for efficient and accurate results.
Functionality Comparison
Various MAC address lookup tools offer different functionalities, from basic lookups to more advanced features. Some tools focus solely on finding the associated device name, while others provide comprehensive details like the device manufacturer, model, and operating system. This variation in capabilities reflects the different purposes these tools serve.
Platforms and Ease of Use
The platform on which a MAC address lookup tool operates significantly impacts its ease of use. Web-based tools are generally user-friendly and accessible from any device with an internet connection. Desktop applications, on the other hand, might offer more customization options and potentially faster processing speeds, but require installing software on the user’s computer.
Accuracy and Reliability
The accuracy and reliability of MAC address lookup tools are essential factors. Tools relying on publicly available databases or real-time information are generally more accurate. Tools that utilize less reliable or outdated information may yield inaccurate results. Thorough testing and validation are important to ensure reliable results.
Detailed Description of Tools
Different tools employ various methods for MAC address lookups. Some use locally stored databases, while others query external services or databases. The method used directly impacts the accuracy and speed of the lookup. For example, real-time databases are generally more accurate than static databases. Furthermore, tools with comprehensive databases may offer more accurate and reliable results.
Comparative Table
| Tool | Platform | Ease of Use | Accuracy | Features | Description |
|---|---|---|---|---|---|
| Tool A | Web-based | High | High | Basic (device name) | Simple tool for quickly finding device names. Relies on a publicly accessible database for quick lookups. |
| Tool B | Desktop application | Medium | High | Advanced (manufacturer, model, OS) | Offers more detailed information about the device associated with the MAC address. Potentially faster processing speeds due to local processing. |
| Tool C | Web-based | High | Medium | Limited (basic information) | Simple tool with a smaller database than Tool A. Results might not be as comprehensive or accurate as Tool A or B. |
The table above provides a general comparison of three different tools, highlighting their platforms, ease of use, accuracy, features, and detailed descriptions.
Security Considerations: Mac Address Lookup Tools
MAC address lookup tools, while useful for network diagnostics, present potential security vulnerabilities if not used cautiously. Understanding these risks and implementing appropriate safeguards is crucial for protecting personal and organizational data. Misuse or unauthorized access to these tools can lead to serious consequences.Using MAC address lookup tools without proper security protocols can expose your network and personal information to various threats.
Unauthorized individuals might exploit these tools to gain access to sensitive data or manipulate network configurations. The potential for misuse and malicious activity necessitates a proactive approach to security.
Potential Security Risks
MAC address lookup tools can be exploited by malicious actors to gather information about a network, identify vulnerabilities, and potentially gain unauthorized access. This information can be used for various malicious activities, including network reconnaissance, denial-of-service attacks, and unauthorized access to resources. Furthermore, some tools might collect or store user data, potentially exposing sensitive information.
Unauthorized Access
Unauthorized access to MAC address lookup tools can lead to severe consequences. An attacker with access could potentially:
- Identify and exploit vulnerabilities in your network.
- Gain access to sensitive data by tracking network traffic.
- Conduct network reconnaissance to plan more sophisticated attacks.
- Disrupt network operations through denial-of-service attacks.
Unauthorized access can cause significant disruptions, financial losses, and reputational damage.
Mac address lookup tools are handy for network troubleshooting, but have you considered the potential of using blockchain technology for something similar? Imagine a secure, immutable record of network devices, managed using a system like create a blockchain with python. This decentralized approach could offer a more robust and transparent way to track MAC addresses, preventing spoofing and enhancing network security.
Ultimately, mac address lookup tools would benefit from such a system, providing more reliable data.
Mitigation Measures
Implementing robust security measures can minimize the risks associated with MAC address lookup tools. These measures include:
- Strong Passwords and Access Control: Employing strong, unique passwords for all accounts associated with the tool and implementing strict access controls can prevent unauthorized access.
- Network Segmentation: Dividing your network into smaller, isolated segments can limit the impact of a potential breach.
- Firewall Protection: Configuring firewalls to restrict access to the tools and block suspicious network traffic is essential.
- Regular Updates: Keeping the software and operating systems of the tools up-to-date can address security vulnerabilities.
Implementing these security measures significantly reduces the risk of malicious actors exploiting vulnerabilities.
Protecting Personal Information
Protecting personal information while using MAC address lookup tools requires vigilance and caution. Users should avoid entering sensitive information into these tools unless absolutely necessary. Avoid using tools from untrusted sources.
- Verify the legitimacy of the tool: Ensure the tool’s origin and purpose are trustworthy.
- Do not share personal details unnecessarily: Limit the amount of personal information provided to the tool.
- Use secure connections: Use tools only over secure connections (HTTPS) to prevent data interception.
- Review data collection policies: Carefully review the privacy policies of the tools before using them to understand how data is handled.
These precautions are vital to maintaining personal information safety.
Security Best Practices
| Security Best Practice | Description |
|---|---|
| Use strong passwords and multi-factor authentication | Implementing strong passwords and multi-factor authentication adds an extra layer of security to protect against unauthorized access. |
| Regularly update software | Keeping software up-to-date addresses known vulnerabilities and improves security posture. |
| Restrict access to the tool | Limit access to the MAC address lookup tool to authorized personnel only. |
| Review data collection policies | Thoroughly examine the privacy policies of the tool to understand how user data is collected, used, and protected. |
| Use secure connections | Connecting to the tool through a secure connection (e.g., HTTPS) safeguards data transmitted between the user and the tool. |
Adhering to these best practices can significantly enhance the security of your network and personal information.
Mac address lookup tools are handy for identifying network devices. While I’m currently digging into the latest developments in the Stanford football Troy Taylor coaching search, I’ve noticed that these tools can be super helpful in troubleshooting network issues, especially when paired with other diagnostics. A good understanding of these tools can be invaluable in a variety of situations, similar to how knowing a coaching candidate’s background might be vital for a successful search like the one at stanford football troy taylor coaching search.
Ultimately, these lookup tools are essential for maintaining a smooth and efficient network operation.
Practical Examples and Use Cases
MAC address lookup tools are invaluable for troubleshooting network problems, managing device inventories, and identifying potential security risks. They provide a direct link between a physical network device and its assigned network address, facilitating efficient identification and management. Understanding how to utilize these tools effectively can significantly streamline IT operations across various industries.
Identifying Specific Devices
Knowing a device’s MAC address allows for its precise identification on a network. For instance, if a printer is malfunctioning, a MAC address lookup tool can pinpoint the specific printer’s MAC address. This enables IT support personnel to quickly isolate the problematic device from the rest of the network. A network administrator might also need to identify a particular laptop connected to the network, potentially for troubleshooting network connectivity issues.
A simple MAC address lookup can confirm if the device is indeed online and functional.
Resolving Network Issues
MAC address lookup tools can be instrumental in diagnosing network problems. If a user reports slow internet speeds, a network administrator can use the tool to identify the MAC address of the affected device. This allows the administrator to check the device’s network configuration and potential conflicts. For example, if a new device is causing network congestion, the MAC address lookup can help determine the source and enable the administrator to implement appropriate network adjustments.
Ever need to track down a specific device’s MAC address? These lookup tools can be super handy, especially if you’re trying to troubleshoot network issues. Speaking of handy, I just heard about this new coffee shop in Burlingame, Burlingame’s new GoodThing Coffee , that’s serving up delicious Japanese cheesecakes alongside their java. Knowing a MAC address lookup tool is a lifesaver for diagnosing problems, which makes a good coffee even better.
A quick look-up can often clear up confusing connectivity problems.
Use Cases in Different Industries
MAC address lookup tools find diverse applications in various industries. In IT support, they facilitate rapid identification of problematic devices, enabling swift resolution of network issues. In network administration, they allow administrators to track network devices, monitor usage patterns, and maintain an accurate inventory. Network security teams leverage MAC address lookups to monitor unusual activity, identifying potential intruders and maintaining network security.
Inventory Management
MAC address lookup tools are crucial for network inventory management. Maintaining an accurate inventory of all devices connected to a network is vital for network administrators. By using the MAC address lookup tool, administrators can quickly compile a list of all devices on the network. This information can then be used to create a comprehensive inventory database, allowing for efficient tracking and management of network resources.
The tool can also aid in verifying the presence of all expected devices on the network, helping in the detection of missing or unauthorized devices.
Table Summarizing Use Cases
| Use Case | Application |
|---|---|
| Identifying Specific Devices | Troubleshooting device malfunctions, verifying device connectivity, locating specific devices on a network. |
| Resolving Network Issues | Diagnosing slow internet speeds, identifying network congestion sources, troubleshooting connectivity problems. |
| Industry Applications | IT support, network administration, network security. |
| Inventory Management | Tracking network devices, maintaining an accurate database of network resources, verifying the presence of all expected devices. |
Future Trends and Advancements
MAC address lookup tools are constantly evolving to meet the demands of a rapidly changing technological landscape. Predicting the precise future of these tools is challenging, but examining emerging trends provides valuable insights into potential developments. This exploration considers how AI, cloud computing, and other advancements will shape the future of these tools.
Potential Developments in MAC Address Lookup Tools
The future of MAC address lookup tools hinges on several key advancements. Enhanced data processing capabilities and integration with broader network intelligence systems will be crucial. This includes not only faster lookup speeds but also more accurate and comprehensive results. The inclusion of real-time data feeds and predictive analysis capabilities could transform how network administrators manage and troubleshoot issues.
This ability to proactively identify potential problems before they arise will be highly valuable.
Impact of Artificial Intelligence (AI)
AI has the potential to significantly impact MAC address lookup tools. AI-powered tools could automatically categorize and analyze MAC addresses, identifying patterns and anomalies in network traffic. This could lead to more efficient troubleshooting and security analysis. For instance, AI algorithms could learn to recognize unusual MAC address behavior associated with malicious activity, alerting administrators to potential threats.
Influence of Cloud Computing
Cloud computing is another significant factor in the evolution of MAC address lookup tools. Cloud-based platforms offer scalability, accessibility, and cost-effectiveness. Storing and processing massive datasets of MAC addresses in the cloud can improve the speed and accuracy of lookups. Moreover, cloud-based tools can facilitate collaborative work between network administrators, allowing for centralized management and real-time data sharing.
Emerging Trends in MAC Address Lookup Tools
The field of MAC address lookup tools is poised for significant transformation. Here are some key emerging trends:
- Integration with Network Management Systems (NMS): MAC address lookup tools are likely to be integrated more deeply into NMS platforms. This integration will streamline network management tasks, providing a holistic view of network devices and their associated MAC addresses. Network administrators will benefit from automated data collection and analysis.
- Predictive Analysis: Leveraging historical data and AI algorithms, these tools may develop predictive capabilities. They could forecast potential network issues, allowing for proactive mitigation strategies. This capability would significantly reduce downtime and improve network stability.
- Real-time Data Feeds: Real-time data feeds from various network devices and sources could enhance the accuracy and speed of MAC address lookups. This integration will improve the timeliness of information, providing up-to-the-second insights into network activity.
- Enhanced Security Features: The security of MAC address lookup tools will become increasingly important. Features like robust authentication mechanisms, encryption, and access control will be essential to prevent unauthorized access and data breaches. Advanced threat detection capabilities based on AI analysis of MAC address behavior will be crucial in securing networks.
Closing Notes
In conclusion, mac address lookup tools are powerful tools that enable efficient network management and troubleshooting. Understanding their various types, features, and applications is crucial for anyone working with networks. This guide has provided a comprehensive overview, highlighting the technical aspects, practical examples, and security considerations. As technology advances, these tools will continue to evolve, adapting to new challenges and requirements in the ever-changing world of networking.