Best Threat Intelligence Platforms A Deep Dive
Best threat intelligence platforms are crucial for modern cybersecurity. They provide a panoramic view of the ever-evolving threat landscape, enabling proactive defenses against sophisticated attacks. This exploration delves into the key features, data sources, and overall value proposition of leading threat intelligence platforms, ultimately helping you make informed decisions for your organization.
From understanding the different types of platforms like SIEM, SOAR, and threat hunting platforms to comparing their pricing models and scalability, we’ll cover all the essentials to empower your cybersecurity strategy. This in-depth look will highlight the vital role threat intelligence plays in today’s digital world.
Introduction to Threat Intelligence Platforms
Threat intelligence platforms are crucial tools for modern cybersecurity. They provide organizations with the information they need to understand and respond to emerging threats. These platforms collect, analyze, and disseminate threat data, allowing security teams to proactively identify vulnerabilities and mitigate risks before they cause significant damage. The sophistication of these platforms is constantly evolving to keep pace with the ever-changing cyber landscape.Threat intelligence platforms are vital for navigating the complexities of the digital world.
Picking the best threat intelligence platforms can be tricky, but it’s crucial for security. Thinking about recent cases like the after hung jury shooter in el sobrante homicide takes 34 years to life highlights the need for proactive intelligence gathering. These platforms need to constantly adapt and stay ahead of emerging threats. Ultimately, choosing the right tools is essential for preventing future incidents.
They act as a central hub for collecting, processing, and distributing critical information about threats. This information helps security teams make informed decisions, enabling proactive threat response and reducing the risk of costly security breaches.
Core Functionalities of Threat Intelligence Platforms
Threat intelligence platforms are designed to collect, analyze, and disseminate information related to various cyber threats. Key functionalities include threat identification, analysis, correlation, and visualization. These platforms typically offer a centralized view of threat activity, enabling security teams to quickly identify patterns and trends. This consolidated approach facilitates quicker incident response and improves overall security posture.
Different Types of Threat Intelligence Platforms, Best threat intelligence platforms
Several types of threat intelligence platforms cater to different security needs. These include Security Information and Event Management (SIEM) systems, Security Orchestration, Automation, and Response (SOAR) platforms, and threat hunting platforms. Each type plays a specific role in the broader threat intelligence ecosystem.
Security Information and Event Management (SIEM) Systems
SIEM systems are foundational for threat intelligence. They collect and analyze security logs from various sources, such as servers, applications, and network devices. This comprehensive log aggregation allows for the detection of suspicious activity and the identification of potential threats. A well-configured SIEM system is an essential component of any security strategy, providing a historical record of events and enabling threat detection through pattern recognition.
Security Orchestration, Automation, and Response (SOAR) Platforms
SOAR platforms enhance the efficiency of incident response. They automate tasks like threat analysis, incident triage, and remediation. This automation streamlines incident handling processes, enabling security teams to respond faster to threats. Automation minimizes manual intervention, reducing response time and the risk of human error.
Threat Hunting Platforms
Threat hunting platforms focus on proactive threat identification. They are specifically designed to uncover hidden threats that might not be detected by traditional security tools. These platforms leverage advanced analytics and machine learning techniques to identify subtle indicators of compromise. By proactively seeking out and addressing potential threats, threat hunting platforms contribute to a stronger overall security posture.
Comparison of Threat Intelligence Platforms
| Platform Type | Features | Pricing | Target Audience |
|---|---|---|---|
| SIEM | Log aggregation, threat detection, correlation, reporting | Variable, often based on volume of data processed | Security teams requiring comprehensive log analysis and threat detection |
| SOAR | Automation of incident response tasks, playbooks, orchestration | Variable, often based on features and scalability | Security teams seeking to improve incident response efficiency and reduce manual intervention |
| Threat Hunting | Advanced analytics, machine learning, proactive threat identification | Variable, often higher than SIEM or SOAR due to advanced features | Security teams focused on proactive threat hunting and advanced threat detection |
Key Features of Best Platforms
Threat intelligence platforms are crucial for organizations to stay ahead of evolving cyber threats. Their effectiveness hinges on a combination of robust features, reliable data sources, and user-friendly interfaces. Understanding these key components is paramount for choosing the right platform to meet your specific security needs.
Data Sources and Integration
The quality and breadth of data sources significantly impact a threat intelligence platform’s value. Top-tier platforms leverage diverse sources to provide a comprehensive view of the threat landscape. These sources include public and private repositories, threat feeds from security vendors, and even open-source intelligence (OSINT). Effective integration of these data streams is essential to ensure accurate and timely threat detection.
Inaccurate or delayed data can lead to missed opportunities to mitigate potential risks. For instance, a platform failing to integrate information from a compromised network quickly can leave the organization vulnerable to further attacks.
Reporting and Visualization
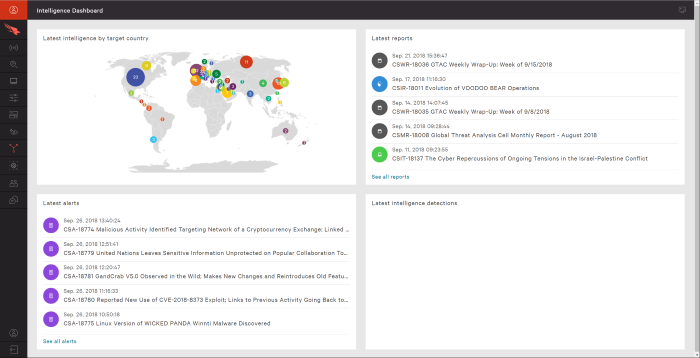
Powerful reporting and visualization capabilities are critical for actionable insights. Effective platforms translate raw threat data into understandable formats, enabling security analysts to identify patterns, trends, and potential risks. Sophisticated dashboards and interactive visualizations facilitate quick analysis and dissemination of key information. Visualization tools allow security teams to easily identify critical threats and prioritize their response efforts, potentially saving time and resources.
For example, a heatmap visualization of attack vectors across different systems can quickly highlight areas needing immediate attention.
User Interface and Ease of Use
A user-friendly interface is crucial for efficient threat analysis and response. The platform should provide intuitive navigation, clear visualizations, and well-organized data presentation. Accessibility and ease of use contribute to faster threat detection and response. Security analysts should be able to quickly access and interpret relevant information without extensive training. A platform with a cluttered or poorly designed interface can hinder productivity and increase response times.
Support for Various Threat Models
Modern threat intelligence platforms must support a diverse range of threat models, from known vulnerabilities to advanced persistent threats (APTs). These models encompass various attack vectors and tactics. The ability to adapt to different threat landscapes is essential for effective risk mitigation. For example, a platform that only recognizes traditional malware attacks will struggle to detect targeted attacks leveraging social engineering techniques.
Advanced Analytics and Machine Learning
Advanced analytics and machine learning play a significant role in identifying sophisticated threats. Platforms should incorporate algorithms to detect anomalies, predict future attacks, and correlate events to provide a more comprehensive threat picture. These advanced capabilities allow for proactive threat hunting and enhance incident response. For instance, machine learning algorithms can identify unusual network traffic patterns, potentially signaling an intrusion attempt.
Comparative Analysis of Key Features
| Feature | Platform A | Platform B | Platform C |
|---|---|---|---|
| Data Sources | Extensive public and private repositories, vendor feeds, OSINT | Focus on industry-specific data, limited OSINT | Strong focus on open-source intelligence, limited private sources |
| Reporting & Visualization | Interactive dashboards, customizable reports | Static reports, limited visualization options | Real-time dashboards, advanced charting |
| User Interface | Intuitive, easy navigation | Complex interface, steep learning curve | User-friendly, accessible |
| Threat Models | Supports various threat models, including APTs | Primarily focused on malware and known vulnerabilities | Covers a wide range of attack vectors |
| Advanced Analytics | Strong machine learning capabilities, anomaly detection | Basic analytics, limited machine learning | Extensive machine learning, predictive capabilities |
Data Sources and Integration
Threat intelligence platforms are only as good as the data they use. A robust platform needs a diverse and reliable collection of information, seamlessly integrated to provide a holistic view of the threat landscape. This section dives into the various data sources powering these platforms and how they effectively combine internal and external information to generate actionable insights.The cornerstone of any effective threat intelligence platform lies in its data sources.
These sources range from open-source intelligence (OSINT) feeds to internal security logs, each contributing unique and critical perspectives on potential threats. The key is not just gathering data, but integrating it in a meaningful way, allowing analysts to quickly identify patterns and trends. Effective data normalization and enrichment processes are crucial for accurate correlation and analysis.
Data Sources Utilized by Leading Platforms
Leading threat intelligence platforms utilize a wide array of data sources, each providing a unique facet of the threat landscape. These sources include:
- Security Information and Event Management (SIEM) data: Internal logs from firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) systems are vital for understanding internal security events. This allows for a real-time view of activities within the organization’s network, enabling the detection of anomalies and suspicious behavior.
- Open-Source Intelligence (OSINT) feeds: Publicly available information, such as news articles, social media posts, and forums, provides a wealth of data on emerging threats, vulnerabilities, and attacker tactics. This can be critical for identifying new malware or exploits in real-time.
- Industry and threat intelligence feeds: Specialized threat intelligence providers offer curated feeds focused on specific threat actors, malware families, and vulnerabilities. These curated feeds provide valuable contextual information, improving the accuracy and relevance of threat assessments.
- Vulnerability databases: Databases like NVD (National Vulnerability Database) offer a comprehensive catalog of known vulnerabilities, enabling organizations to proactively address potential weaknesses in their systems.
- Malware analysis reports: Reports from malware analysis labs provide detailed information about the functionality, behavior, and potential impact of malicious software, crucial for understanding the nature of the threat.
Integration Methods for External and Internal Data
The integration of diverse data sources is a critical aspect of threat intelligence platforms. Effective integration allows analysts to correlate information from various sources, creating a more comprehensive view of the threat landscape.
- API integrations: Platforms often utilize Application Programming Interfaces (APIs) to connect to external threat feeds and internal security systems. This allows for automated data ingestion and ensures the latest information is always available.
- Data pipelines: Data pipelines are essential for moving data from disparate sources to a central repository. This process involves transforming and normalizing data to make it usable for analysis.
- Custom scripting: For complex data integration requirements, custom scripting allows for specific data transformations and transformations to ensure accurate correlation and analysis.
Data Normalization and Enrichment
Normalization is the process of transforming data from various sources into a consistent format. This is crucial for accurate correlation and analysis, ensuring that data from different sources can be effectively compared. Enrichment involves adding context and details to the data, improving its understanding and value.
Normalization ensures consistency, while enrichment adds context, leading to a more insightful threat intelligence picture.
Data Visualization Options
Effective data visualization is crucial for quickly identifying patterns and trends in threat intelligence data. Various visualization tools are available, including dashboards, graphs, and maps.
- Dashboards: Dashboards provide a high-level overview of key threat indicators, allowing for quick identification of emerging threats and trends.
- Graphs: Graphs can be used to visualize relationships between different threat actors, malware families, and vulnerabilities.
- Maps: Maps can be used to visualize the geographic distribution of threats, enabling organizations to understand the global scope of a particular threat.
Data Source Integration Table
| Data Source Type | Integration Method |
|---|---|
| Security Information and Event Management (SIEM) data | API integration, Data pipelines |
| Open-Source Intelligence (OSINT) feeds | API integration, Data pipelines, Custom scripting |
| Industry and threat intelligence feeds | API integration, Data pipelines |
| Vulnerability databases | API integration, Data pipelines |
| Malware analysis reports | API integration, Data pipelines |
Reporting and Visualization Capabilities
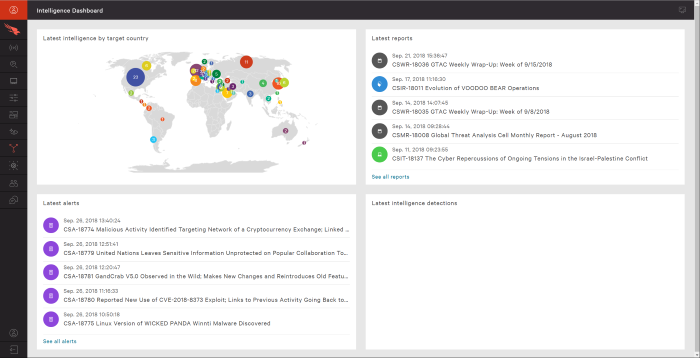
Threat intelligence platforms are not just about collecting data; they’re about understanding and acting on it. Effective reporting and visualization are crucial for turning raw information into actionable insights. A well-designed platform should provide clear, concise, and customizable reports that highlight emerging threats, vulnerabilities, and potential attack vectors. This allows security teams to make informed decisions, prioritize responses, and ultimately improve their overall security posture.The reporting and visualization capabilities of a threat intelligence platform are key to its effectiveness.
They empower security analysts to easily identify trends, patterns, and anomalies within the threat landscape, enabling proactive security measures. A strong platform should provide a variety of ways to present data, allowing for customization and tailored views based on specific needs. This flexibility is essential for effective threat hunting and incident response.
Reporting Functionalities
Threat intelligence platforms offer a range of reporting functionalities, from basic summaries to complex analyses. Some platforms provide pre-built reports on common threat actors, attack patterns, and emerging vulnerabilities. Others allow for custom reports based on specific criteria, enabling targeted investigations. The ability to generate reports in various formats (PDF, CSV, Excel) is also essential for sharing and collaboration.
Moreover, advanced platforms offer scheduled reporting, ensuring that security teams receive regular updates on the evolving threat landscape.
Customization of Reports and Dashboards
Customizable dashboards and reports are vital for tailoring threat intelligence to specific organizational needs. A platform should allow users to select data points, filters, and visualizations relevant to their particular threat landscape. This allows for focused analysis and efficient threat response. Security teams can personalize their dashboards with widgets displaying key metrics and relevant data. This level of customization ensures that the platform remains a valuable resource for continuous monitoring and proactive security.
Real-Time Threat Monitoring and Alerting
Real-time threat monitoring and alerting are essential for immediate threat response. A platform should provide dashboards that dynamically display current threats, vulnerabilities, and emerging attack patterns. This allows security analysts to react swiftly to emerging threats. Automated alerts based on pre-defined criteria can trigger immediate responses, potentially mitigating the impact of a security incident. The speed and accuracy of real-time threat monitoring are critical for maintaining a robust security posture.
Examples of Visualizations
Visualizations are key to understanding threat intelligence data. A platform should offer various chart types to effectively represent the data, including:
- Timeline charts illustrating the progression of an attack or the frequency of a threat actor’s activity.
- Heat maps showing the geographic distribution of threats or the severity of vulnerabilities across different systems.
- Network graphs visualizing the relationships between different threat actors, compromised systems, and attack vectors. This type of visualization helps analysts understand the scope of an attack and identify potential entry points.
These visualizations allow for quick identification of patterns and anomalies, helping security analysts make informed decisions.
Summary of Reporting and Visualization Features
| Feature | Description | Example |
|---|---|---|
| Basic Reporting | Pre-built reports on common threats. | Summary of ransomware attacks in the last quarter. |
| Custom Reporting | Tailored reports based on specific criteria. | Report on vulnerabilities affecting web servers. |
| Dashboards | Customizable dashboards with widgets. | Dashboard displaying real-time attack attempts and blocked IPs. |
| Real-time Monitoring | Dynamic displays of current threats. | Map showing active phishing campaigns in real-time. |
| Alerting | Automated alerts based on pre-defined criteria. | Alert triggered when a known malware is detected on the network. |
| Visualizations | Various chart types for effective data representation. | Network graph visualizing the connections between compromised systems and malicious actors. |
Platform Architecture and Scalability: Best Threat Intelligence Platforms

Threat intelligence platforms need robust architecture and scalability to handle the ever-increasing volume and velocity of threat data. Modern platforms are designed with modularity and flexibility in mind, allowing them to adapt to changing security landscapes and the needs of diverse organizations. This adaptability is crucial for maintaining a proactive security posture.The architecture of a threat intelligence platform significantly impacts its ability to process, analyze, and disseminate information effectively.
A well-designed architecture ensures efficient data flow, minimizing latency and maximizing the value derived from intelligence. Scalability is equally critical, allowing the platform to accommodate expanding data sources and increasing user demands without compromising performance.
Leading Platform Architectures
Leading threat intelligence platforms employ various architectural designs. Commonly, they leverage distributed systems with microservices architecture, enabling independent modules to handle specific tasks like data ingestion, analysis, and visualization. This approach facilitates horizontal scaling and allows for rapid updates and improvements. Centralized management dashboards provide a unified view of the entire threat intelligence landscape, offering insights into data sources, analysis results, and user activity.
This centralization is vital for security operations teams to efficiently manage and monitor the entire intelligence cycle.
Choosing the best threat intelligence platforms is crucial for any organization. Understanding the latest security threats is paramount, and staying ahead of the curve is key. Speaking of important events, did you know that the 50th Charlie Wedemeyer Santa Clara All-Star Football Game is happening? Check out what to know about the 50th Charlie Wedemeyer Santa Clara All-Star Football Game for all the details.
Ultimately, the best threat intelligence platforms provide actionable insights to defend against these emerging threats, ensuring businesses are protected.
Scalability Considerations
Scalability is a key factor in choosing a threat intelligence platform. Platforms must be able to handle the increasing volume of data from various sources, including open-source intelligence (OSINT), security feeds, and internal logs. This requires a platform architecture that can dynamically adjust to the growing data volumes. A critical component of scalability is the platform’s ability to efficiently process and analyze this data.
For instance, some platforms employ distributed caching mechanisms and advanced algorithms to accelerate analysis and reduce response times. Platforms also need to scale storage and compute resources to maintain optimal performance. Cloud-based solutions often excel in this regard, offering on-demand scaling capabilities.
Deployment Options
The choice between cloud, on-premises, or hybrid deployment depends on the organization’s specific needs and security policies. Cloud-based platforms offer greater scalability and cost-effectiveness, particularly for rapidly growing organizations. On-premises deployments provide greater control and security for organizations with stringent regulatory requirements. Hybrid deployments combine the benefits of both, allowing for a mix of cloud-based and on-premises solutions.
Cloud providers typically offer a wide range of services, such as storage, compute, and networking, allowing for easy and rapid scaling. Organizations need to carefully consider factors like security posture, regulatory compliance, and internal infrastructure before choosing a deployment model.
Integration with Security Tools
A critical aspect of a threat intelligence platform is its ability to integrate with existing security tools. This integration enables the platform to leverage the existing security infrastructure and provide a unified view of the threat landscape. Many platforms offer APIs and connectors to integrate with SIEMs, SOARs, and other security information and event management (SIEM) tools. This integration allows for automated workflows, data sharing, and enhanced threat detection and response capabilities.
For instance, if a threat is identified, the platform can automatically trigger alerts and actions in connected security tools.
Platform Comparison Table
| Platform | Architecture | Scalability | Deployment Options | Integration |
|---|---|---|---|---|
| Platform A | Microservices-based, distributed | Excellent, dynamic scaling in cloud | Cloud, hybrid | Extensive API support for SIEM/SOAR |
| Platform B | Monolithic, centralized | Moderate, limited scaling options | On-premises, limited cloud | Basic integration capabilities |
| Platform C | Microservices-based, distributed | Excellent, supports both on-premises and cloud | Cloud, on-premises, hybrid | Robust API support, pre-built connectors |
User Experience and Ease of Use
Threat intelligence platforms need to be more than just repositories of data; they need to be intuitive and user-friendly tools that empower security teams to quickly identify and respond to threats. A seamless user experience significantly impacts an organization’s ability to leverage threat intelligence effectively. This section dives into the crucial aspects of user interface design, navigation, and usability features in top threat intelligence platforms.
User Interface and Navigation
Modern threat intelligence platforms prioritize intuitive user interfaces (UIs) and clear navigation. Effective navigation allows analysts to quickly locate relevant information, filter data, and visualize patterns. The best platforms often employ a dashboard-centric approach, presenting key metrics and visualizations at a glance. This immediate overview is essential for quickly assessing the threat landscape and prioritizing investigations. Search functionality is also critical; a robust search engine allows analysts to pinpoint specific threat actors, indicators of compromise (IOCs), or events with precision.
Intuitive Dashboards and Interactive Visualizations
Effective dashboards provide a bird’s-eye view of the threat landscape. Top platforms often feature customizable dashboards, allowing analysts to configure displays to match their specific needs and priorities. Dynamic visualizations, such as heatmaps, graphs, and timelines, effectively present complex data, revealing trends and patterns that might otherwise be missed. Interactive elements, such as drill-down capabilities, enable users to explore details behind summarized data, fostering a deeper understanding of the threats.
For example, a heatmap showing the frequency of specific malware across different regions can highlight potential emerging threats and allow for targeted responses.
User Roles and Permissions
Access control is paramount in threat intelligence platforms. Robust user roles and permissions systems ensure that only authorized personnel have access to sensitive data and actions. Different roles, such as analysts, administrators, and executives, have varying levels of access, preventing unauthorized access and data breaches. A granular permissions system allows organizations to control who can view, modify, or delete information, maintaining data security and compliance.
Best Practices for Efficient Platform Utilization
Efficient platform utilization is crucial for maximizing the value of threat intelligence. Platforms should be tailored to the specific needs of the security team, enabling efficient workflows. Implementing clear workflows and standardized procedures for threat analysis will help streamline responses to potential threats. Training and knowledge sharing are essential to ensure analysts understand the platform’s features and utilize them effectively.
A well-documented platform with tutorials and support resources empowers analysts and accelerates their learning curve.
Table: User Interface and Usability Features
| Platform | User Interface Design | Navigation | Dashboards | Visualizations | Search Functionality |
|---|---|---|---|---|---|
| Platform A | Clean, intuitive design with clear visual hierarchy | Easy navigation with intuitive menus and shortcuts | Highly customizable dashboards with key metrics | Interactive graphs, maps, and timelines | Powerful search engine with advanced filtering options |
| Platform B | Modern, minimalist design | Hierarchical structure with logical grouping of data | Pre-built dashboards with configurable widgets | Data visualization tools with drill-down capabilities | Real-time search and filtering capabilities |
| Platform C | User-friendly interface with clear labeling | Simple and straightforward navigation | Customizable dashboards with dynamic updates | Intuitive visualization tools with data aggregation | Fast and accurate search based on various criteria |
Cost and Pricing Models
Choosing the right threat intelligence platform hinges significantly on its cost and pricing model. Understanding the various pricing structures, the factors influencing them, and the potential hidden costs is crucial for organizations to make informed decisions. A poorly chosen platform, even with impressive features, can quickly become a significant financial burden.Pricing models for threat intelligence platforms are diverse and often complex, reflecting the varied nature of data, features, and support services offered.
Understanding the specific terms of each model is essential to avoid surprises down the line and to ensure the platform aligns with the organization’s budget and needs.
Different Pricing Models
Various pricing models exist for threat intelligence platforms, each with its own advantages and disadvantages. Common models include subscription-based pricing, usage-based pricing, and tiered pricing. Subscription models offer predictable monthly or annual fees, while usage-based models charge based on the amount of data consumed or features used. Tiered models provide varying levels of service at different price points, often scaling with the number of users or the volume of data processed.
Factors Influencing Platform Pricing
Several factors significantly impact the price of a threat intelligence platform. The breadth and depth of data sources, the sophistication of analytical tools, and the level of customization are key determinants. A platform offering comprehensive data from various sources and advanced analysis will generally command a higher price point compared to one with limited coverage. User count also plays a crucial role; larger organizations with numerous security personnel require platforms with more robust user access and management features, driving up costs.
Data volume is another critical factor; platforms that process large volumes of data require more processing power and storage, thus influencing pricing.
Hidden Costs
Beyond the advertised price, several hidden costs can impact the overall expense of a threat intelligence platform. These can include additional charges for specialized integrations with existing security tools, support services beyond the initial contract, or the cost of training personnel to effectively use the platform. Organizations must scrutinize the fine print to avoid unexpected expenses. For example, some platforms may impose limits on the number of alerts or reports that can be generated, requiring additional paid tiers or subscriptions to exceed these limitations.
Staying ahead of cyber threats requires robust threat intelligence platforms. The rising number of abortions in the US, with women increasingly relying on medication and travel options, highlights the complex social landscape we’re navigating. This situation underscores the need for comprehensive threat intelligence that can identify and analyze evolving patterns, ultimately helping organizations bolster their security postures.
Effective platforms are crucial for protecting sensitive data and maintaining operational stability.
Support costs, often overlooked, can escalate quickly if the platform requires significant assistance to set up, configure, or troubleshoot issues.
Return on Investment (ROI)
The ROI of a threat intelligence platform depends heavily on how effectively it reduces security risks and improves incident response capabilities. A successful platform can lead to reduced downtime, minimized financial losses from breaches, and improved operational efficiency. Quantifying the ROI can involve assessing the potential financial losses avoided by proactively detecting and responding to threats. For instance, a platform that successfully prevents a ransomware attack could save a company millions in recovery costs and reputational damage.
Analyzing the platform’s impact on incident response time and the number of successful threat mitigations can provide a more precise understanding of the platform’s ROI.
Pricing Model Comparison
| Pricing Model | Description | Potential Costs | Example Platforms |
|---|---|---|---|
| Subscription-Based | Fixed monthly or annual fees based on features and user access. | Predictable costs but may not scale optimally for fluctuating data volume. | Many security platforms |
| Usage-Based | Pricing tied to data volume, features utilized, or alert generation. | Can be variable and unpredictable, potentially higher costs for high data volume. | Some advanced threat intelligence platforms |
| Tiered Pricing | Different pricing levels with varying feature sets and user limits. | Offers flexibility but requires careful selection to ensure the chosen tier meets needs. | Many security platforms |
Platform Support and Maintenance
Choosing a threat intelligence platform isn’t just about the features; it’s also about the ongoing support and maintenance. A robust platform provides reliable access to timely updates and helpful resources, minimizing downtime and maximizing the platform’s value. A well-maintained platform ensures the accuracy and effectiveness of the threat intelligence, enabling organizations to stay ahead of evolving cyber threats.
Support Services Offered
Different platforms offer varying levels of support, ranging from basic documentation to dedicated account managers. Some platforms provide 24/7 support via phone, email, or chat, while others rely primarily on self-service resources like FAQs and online communities. The level of support directly impacts the speed and efficiency of problem resolution, influencing the platform’s overall value. Comprehensive support ensures swift assistance when encountering issues, minimizing disruptions to the intelligence gathering process.
Maintenance Procedures and Updates
Platform maintenance encompasses regular updates, patching, and security enhancements. These procedures ensure the platform remains compatible with the latest technologies and safeguards against vulnerabilities. Maintenance schedules and update frequency are crucial aspects, as they directly affect the platform’s stability and performance. Understanding the platform’s maintenance procedures provides insights into its reliability and long-term viability.
Platform Documentation and Learning Resources
Thorough documentation and readily accessible learning resources are essential for efficient platform utilization. This includes comprehensive manuals, tutorials, and video guides, enabling users to navigate the platform effectively. Well-structured documentation simplifies the learning process, accelerates user proficiency, and empowers organizations to fully leverage the platform’s capabilities. Clear and accessible documentation is a significant factor in maximizing the value of the threat intelligence platform.
Successful Customer Support Experiences
Positive customer support experiences often stem from proactive responses, timely resolutions, and clear communication. Organizations should seek platforms with a history of responsive support, enabling swift problem resolution. Testimonials and reviews from existing customers can provide valuable insights into the platform’s support capabilities and user satisfaction levels. A platform’s support responsiveness and efficiency are often cited as key factors in customer satisfaction.
Summary of Support Options and Maintenance Procedures
| Platform | Support Options | Maintenance Procedures |
|---|---|---|
| Platform A | 24/7 phone, email, chat support; online knowledge base | Regular updates (quarterly); security patches (monthly); platform performance monitoring |
| Platform B | Email support; extensive online documentation; community forums | Bi-weekly updates; security patches (as needed); scheduled maintenance windows |
| Platform C | Dedicated account manager; online webinars; FAQs | Monthly updates; automated security scanning; proactive vulnerability management |
Final Thoughts
In conclusion, selecting the best threat intelligence platform is a significant step in bolstering your organization’s security posture. Careful consideration of factors like features, pricing, and scalability is essential. This guide has provided a comprehensive overview, equipping you with the knowledge to navigate the complexities of the threat landscape and make the right choice for your specific needs. Remember, a proactive approach to threat intelligence is paramount in today’s ever-changing cyber environment.