GitHub Setup Passwordless Auth Your Guide
GitHub setup passwordless auth is crucial for secure and streamlined workflow. This guide dives deep into various methods, from setting up SSH keys to implementing robust two-factor authentication (2FA). Learn how to ditch passwords and unlock a more secure, efficient GitHub experience.
We’ll explore the different passwordless authentication methods available on GitHub, detailing their benefits, security advantages, and setup complexities. We’ll provide step-by-step instructions, comprehensive comparisons, and troubleshooting tips, ensuring you navigate the process with ease.
Introduction to Passwordless Authentication on GitHub
Passwordless authentication is a revolutionary approach to accessing accounts, eliminating the need for traditional passwords. Instead of relying on remembering and typing complex passwords, users leverage alternative methods for verification, significantly enhancing security and user experience. This shift is driven by the growing awareness of password vulnerabilities and the desire for more secure and convenient login procedures.Passwordless authentication offers a compelling alternative to traditional password-based systems.
It reduces the risk of password breaches, making accounts less susceptible to hacking attempts. This approach also simplifies the login process, making it more user-friendly and less prone to errors. By eliminating the need for typing passwords, users can enjoy a smoother and more streamlined experience.
Benefits of Passwordless Authentication on GitHub
Passwordless authentication on GitHub provides several key advantages. It safeguards sensitive account data by reducing the risk of password compromise. It also simplifies the authentication process, enabling users to access their repositories and projects more efficiently. The adoption of passwordless methods enhances the overall security posture of GitHub, creating a more secure and reliable platform for developers.
Different Methods for Passwordless Authentication on GitHub
GitHub offers a variety of methods for passwordless authentication, each with its own strengths and weaknesses. Understanding these methods allows users to choose the approach that best suits their needs and security preferences.
Comparison of Passwordless Authentication Methods
| Method | Description | Security Advantages | Setup Complexity |
|---|---|---|---|
| SSH Keys | Using SSH keys involves generating a pair of cryptographic keys (public and private). The public key is added to GitHub, and the private key is kept secure. Access is granted by verifying the private key, eliminating the need for passwords for SSH connections. | SSH keys provide strong security through cryptography, making it extremely difficult for unauthorized access. The separation of keys enhances the overall security of the account. | The initial setup can involve a few steps, but once configured, it’s relatively straightforward. Properly securing the private key is crucial. |
| Two-Factor Authentication (2FA) | 2FA adds an extra layer of security by requiring a second verification method beyond a password. This often involves receiving a code via SMS, authenticator app, or hardware token. | 2FA significantly strengthens security by requiring two distinct verification steps. This makes it much harder for attackers to gain access, even if they have compromised the password. | Setting up 2FA is relatively simple and usually involves adding a trusted device or application. |
| GitHub’s Passwordless Authentication (Beta) | GitHub’s passwordless authentication (in beta) uses a combination of modern authentication methods. It relies on security keys, biometric verification, or other factors to provide a more streamlined password-free login. | This method is expected to enhance security by using multiple verification factors, increasing protection against various attacks. | The setup process is usually integrated within the GitHub platform, making it relatively user-friendly. |
Setting Up SSH Keys for Passwordless Access
SSH keys are crucial for secure and automated access to your GitHub repositories. They eliminate the need for typing your password every time you interact with your repositories, streamlining your workflow and enhancing security. This method leverages public-key cryptography to authenticate you without revealing your password.Generating and configuring SSH keys is a straightforward process that significantly improves your GitHub experience.
This guide provides detailed steps for all major operating systems. It Artikels the essential steps for generating keys, adding them to your GitHub account, and configuring them for specific repositories.
Generating SSH Keys
Generating SSH keys involves creating a unique pair of keys: a public key and a private key. The public key is shared with the server (in this case, GitHub), while the private key is kept securely on your local machine. This process ensures only authorized users can access your repositories.
- Open your terminal or command prompt. On macOS and Linux, use the command `ssh-keygen`. On Windows, you’ll typically use Git Bash.
- Follow the prompts to create the key pair. You’ll likely be asked for a file name and password for your private key. It’s recommended to keep your private key secure and not share it with anyone.
- The command will create two files: `id_rsa` (your private key) and `id_rsa.pub` (your public key). These files are crucial for passwordless access.
Adding SSH Keys to Your GitHub Account
To grant GitHub access to your SSH key, you must add the public key to your GitHub account settings.
- Open your GitHub account settings and navigate to SSH and GPG keys.
- Click the “New SSH key” button.
- Paste the content of your `id_rsa.pub` file into the “Key” field.
- Enter a descriptive title for your key (e.g., “My Personal Computer”).
- Click “Add SSH key”.
Configuring SSH Keys for Specific Repositories
Once your key is added to GitHub, you need to configure it for specific repositories where you want to use passwordless access. This step ensures the correct key is used for authentication.
Setting up passwordless authentication on GitHub is a game-changer for efficiency. It streamlines your workflow, especially when you’re juggling multiple projects. This is crucial for anyone looking to maximize their online presence and generate leads, like focusing on website online lead generation. Ultimately, a smooth GitHub setup is a solid foundation for any developer’s productivity and success.
- Verify the correct SSH key is in use. You can check your currently configured SSH keys by running `ssh -T [email protected]` in your terminal.
- If you encounter an error, it might indicate a problem with your SSH configuration. Ensure the correct key is added and configured in GitHub settings.
Step-by-Step Guide
This table provides a concise guide to setting up SSH keys across different operating systems.
| OS | Generate Key | Add to GitHub | Configure for Repo |
|---|---|---|---|
| macOS | `ssh-keygen` | GitHub settings -> SSH and GPG keys -> Add SSH key | Ensure SSH key is properly configured within the project |
| Linux | `ssh-keygen` | GitHub settings -> SSH and GPG keys -> Add SSH key | Ensure SSH key is properly configured within the project |
| Windows | Git Bash -> `ssh-keygen` | GitHub settings -> SSH and GPG keys -> Add SSH key | Ensure SSH key is properly configured within the project |
Implementing Two-Factor Authentication (2FA)
Two-factor authentication (2FA) adds an extra layer of security to your online accounts, significantly enhancing protection against unauthorized access. By requiring two distinct verification methods, 2FA makes it much harder for attackers to gain access even if they manage to obtain your password. This crucial security measure is highly recommended for all online accounts, especially for sensitive platforms like GitHub.FA works by verifying your identity using two independent factors: something you know (your password) and something you have (a dedicated authentication app or code).
This approach makes it nearly impossible for attackers to gain access even if they compromise one factor. It’s a simple yet highly effective strategy to safeguard your accounts.
Understanding Two-Factor Authentication (2FA)
Two-factor authentication, or 2FA, is a security process that requires two forms of verification to access an account. This involves using something you know (like a password) and something you possess (like a dedicated authentication app or a code sent to your phone). This dual verification greatly reduces the risk of unauthorized access.
Different Types of 2FA Methods
Various methods are available for implementing 2FA. Each method offers unique strengths and weaknesses, and the best choice depends on individual preferences and security needs.
- Time-based One-time Passwords (TOTP): These methods utilize a dedicated authenticator app (like Google Authenticator or Authy) to generate time-sensitive codes. These codes change frequently, making it difficult for attackers to intercept or predict them. This approach is widely used and generally considered highly secure.
- Software Tokens: Similar to TOTP, software tokens use algorithms to generate time-sensitive codes. They are often integrated into specific software applications or websites, making the authentication process seamless.
- SMS-based codes: This method involves receiving a one-time code via text message to your mobile phone. While convenient, SMS-based codes are generally considered less secure than TOTP or other methods, as interception of the messages is a potential vulnerability.
- Hardware Tokens: These are physical devices that generate unique codes. They offer a high level of security, but they are more expensive and less convenient than software-based solutions.
Security Advantages of Using 2FA on GitHub
Implementing 2FA on GitHub significantly enhances the security of your account. It adds an extra layer of protection, making it substantially more difficult for attackers to gain unauthorized access, even if they successfully compromise your password. This is crucial for protecting your repositories and sensitive data.
Setting up passwordless authentication on GitHub is super handy for streamlined workflow. While you’re diving deep into the technical side of things, it’s worth considering top GPU overclocking software for boosting your rig’s performance. Tools like top GPU overclocking software can help you get the most out of your hardware. Ultimately, though, having a secure and easy GitHub setup is key for efficient coding and collaboration.
Setting Up 2FA on GitHub
Setting up 2FA on GitHub is straightforward. Follow these steps:
- Navigate to your GitHub account settings.
- Locate the “Two-factor authentication” section.
- Select the desired 2FA method (e.g., Google Authenticator).
- Follow the instructions provided by GitHub to complete the setup.
- Verify your identity using the generated code from the authenticator app.
Comparison of 2FA Methods
The table below compares various 2FA methods based on their security rating, ease of use, and other relevant factors.
| Method | Description | Security Rating | Ease of Use |
|---|---|---|---|
| Google Authenticator | Generates time-based codes via a mobile app. | High | High |
| Authy | Similar to Google Authenticator, offering mobile app-based codes. | High | High |
| SMS-based codes | Receives codes via text message. | Medium | High |
| Hardware Tokens | Physical devices that generate unique codes. | Very High | Medium |
Managing and Troubleshooting Passwordless Authentication
Setting up passwordless authentication on GitHub is a significant step towards enhanced security. However, like any system, it can encounter issues. This section details common problems, troubleshooting strategies, and key management procedures for maintaining a secure and reliable passwordless workflow.Troubleshooting passwordless authentication on GitHub involves identifying and resolving various issues. Understanding the root causes of problems is crucial for effective solutions.
This section provides a comprehensive guide to navigating common pitfalls and restoring seamless access.
Common Issues with Passwordless Authentication
Passwordless authentication, while convenient, can sometimes encounter problems. These issues range from simple connectivity problems to more complex key management challenges. Common issues include:
- Incorrect SSH key configuration:
- Network connectivity problems hindering SSH key verification.
- Issues with the SSH key’s permissions or the SSH server configuration.
- Problems with the authorized_keys file.
Troubleshooting Passwordless Authentication Problems
Troubleshooting passwordless authentication problems involves a systematic approach. Start with the simplest checks and progressively move to more complex solutions.
- Verify network connectivity:
- Ensure your internet connection is stable and reliable. Test connectivity to GitHub servers using a web browser or other tools.
- Check SSH key configuration:
- Verify the SSH key is properly added to your GitHub account and correctly configured on your local machine. Confirm that the public key is correctly placed in the `~/.ssh/authorized_keys` file on your system.
- Inspect the authorized_keys file:
- Ensure that the public key is correctly formatted and that there are no typos in the key. Review permissions and ownership for the file. Verify the authorized_keys file has the correct permissions, typically 600, for the user and is readable only by the user.
- Investigate SSH server configuration:
- Check the SSH server configuration on GitHub for any issues. Contact GitHub support if necessary.
Revoking SSH Keys, Github setup passwordless auth
Revoking SSH keys is essential for security. A compromised key can grant unauthorized access.
- Locate the public key:
- Find the public key associated with the account on your local machine. It’s usually located in the `~/.ssh/` directory.
- Remove the public key from the authorized_keys file:
- Remove the public key from the `~/.ssh/authorized_keys` file on your GitHub account. Ensure that the key is completely removed.
- Generate a new SSH key pair:
- Generate a new SSH key pair. Use this new key pair for future connections to GitHub.
Disabling or Re-enabling Two-Factor Authentication (2FA)
Two-Factor Authentication (2FA) adds an extra layer of security. Disabling or re-enabling 2FA is necessary if you want to change how you access your account.
- Accessing 2FA settings:
- Navigate to your GitHub account settings and locate the 2FA section.
- Disabling 2FA:
- Follow the instructions provided by GitHub to disable 2FA. Be cautious and ensure you understand the implications of disabling 2FA.
- Re-enabling 2FA:
- Follow the instructions provided by GitHub to re-enable 2FA. This will require you to re-configure your authentication methods.
Troubleshooting Flowchart
The following flowchart illustrates the troubleshooting steps for various passwordless authentication errors. The flowchart guides users through a series of checks to identify the source of the problem and provide a solution.
| Problem | Step 1 | Step 2 | Step 3 |
|---|---|---|---|
| Network Connectivity Issues | Check network connection | Verify SSH client/server | Contact your network administrator |
| SSH Key Issues | Verify SSH key pair | Check authorized_keys file | Regenerate SSH key pair |
Best Practices for Passwordless Authentication
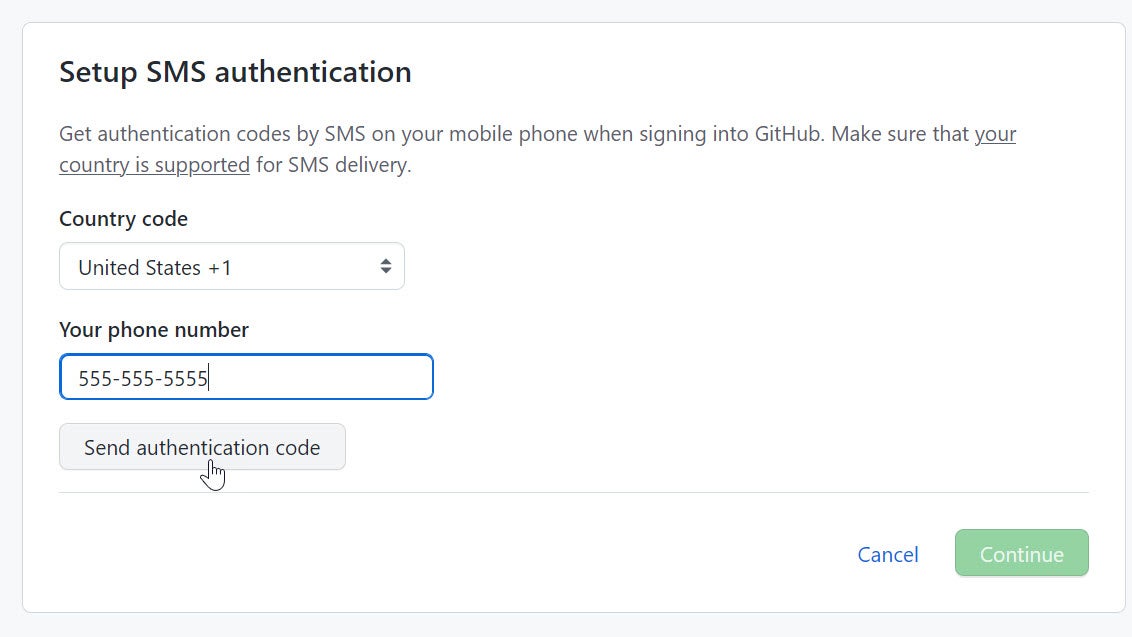
Passwordless authentication, particularly using SSH keys, offers significant security advantages over traditional password-based systems. By eliminating the need to type passwords, you drastically reduce the risk of credential compromise and improve overall system security. This approach, when implemented correctly, can enhance the robustness of your GitHub workflow. This section dives into the crucial best practices for securing your passwordless authentication setup.Implementing strong security measures is paramount when leveraging passwordless authentication.
Understanding the intricacies of SSH key management, choosing the right two-factor authentication (2FA) method, and safeguarding your keys is essential for maintaining a secure environment. This guide provides detailed strategies to fortify your passwordless authentication on GitHub.
Security Best Practices for SSH Keys
SSH keys are the cornerstone of passwordless authentication. Their security directly impacts the integrity of your GitHub access. Protecting these keys is critical. Proper handling involves several key practices.
Setting up passwordless authentication on GitHub is a game-changer for streamlining your workflow. It’s super helpful for avoiding those pesky password prompts, especially when you’re juggling multiple projects. Speaking of streamlining, did you hear about the groundbreaking froggy gets world premiere in walnut creek? This impressive event highlights the power of innovation, just like how passwordless authentication simplifies coding.
Ultimately, a smooth GitHub experience is key for productive coding, and passwordless authentication is a big step in that direction.
- Generate strong, unique SSH keys. Avoid using easily guessable or predictable key names and phrases. Utilize a robust key generation process that ensures the key pair is sufficiently strong. The key should be sufficiently long and complex to resist brute-force attacks and sophisticated cryptanalysis.
- Use a secure key storage mechanism. Do not store your private keys in easily accessible locations. Utilize dedicated key management solutions or securely encrypted files. Never commit your private key to a version control system like GitHub, as this poses a significant security risk. Store them in a password manager or a secure file location on your local system.
- Regularly review and update your SSH keys. This practice helps identify and mitigate any potential vulnerabilities in your authentication system. Check for any unauthorized access attempts or suspicious activity on your GitHub account. Regularly update and replace keys to keep your authentication robust and secure.
- Ensure your SSH key is properly authorized. Verify that the SSH key you’re using is authorized to access the intended resources. Configure appropriate permissions for the key to limit potential damage from unauthorized access.
Choosing the Right 2FA Method
Two-factor authentication (2FA) adds an extra layer of security to your passwordless authentication. Selecting the appropriate 2FA method is crucial for maximizing security.
- Consider the security strength of various 2FA methods. Some methods, such as authenticator apps, offer strong security compared to others, such as SMS-based verification. Assess the security strength of each option before selecting a 2FA method.
- Prioritize methods with strong security standards. Methods using hardware tokens often provide the highest security level. Choose a method that meets your security needs and comfort level.
- Evaluate the ease of use and reliability of the chosen method. A reliable 2FA method should be easy to set up and use, minimizing the chance of errors or complications. Select a 2FA method that fits your workflow and ensures ease of access and reliability.
Maintaining SSH Key Security
Protecting your SSH keys is critical to maintaining a secure authentication system. This involves a combination of best practices.
- Regularly monitor your SSH logs. Track any suspicious activity, such as unauthorized access attempts, and take prompt action to mitigate potential risks. Monitor your SSH logs for any unusual or unauthorized activity. This proactive monitoring can prevent potential breaches and help identify and address security issues quickly.
- Use strong passwords for any accounts associated with your SSH keys. If you use password managers, ensure they are well-protected. Use strong, unique passwords for accounts associated with your SSH keys and ensure your password manager is securely protected.
- Employ strong password management techniques. Utilize robust password management solutions for added security. Use a reputable password manager to store and manage your passwords securely.
Security Recommendations for GitHub Passwordless Authentication
A robust passwordless authentication setup requires a multifaceted approach.
- Regularly review and update your SSH keys. Checking for potential vulnerabilities and updating your SSH keys is critical for maintaining the security of your authentication setup. Regularly update and review your SSH keys for any security vulnerabilities or issues. This proactive approach helps maintain a strong security posture.
- Utilize strong passwords and 2FA. Combined, these measures significantly enhance the security of your account and minimize the risk of unauthorized access. Use strong passwords and enable 2FA for all associated accounts.
- Avoid sharing your SSH keys with others. Maintaining the confidentiality of your private keys is essential to prevent unauthorized access. Do not share your private SSH keys with anyone.
Comparison of Passwordless Authentication Methods
Passwordless authentication methods offer significant improvements over traditional password-based systems, reducing the risk of breaches and improving user experience. Different methods cater to varying needs and security requirements. Understanding their strengths and weaknesses allows users to choose the best approach for their specific use cases.
SSH Keys
SSH keys provide a robust and secure method for passwordless authentication. They rely on cryptographic keys to verify user identity, eliminating the need for remembering and typing passwords. This approach is particularly suitable for command-line interactions and automated tasks.
- Strengths: SSH keys offer a high level of security, as the private key is never transmitted over the network. They are ideal for automated tasks and command-line interactions, where typing passwords is inconvenient and error-prone. They are widely supported across various operating systems and tools.
- Weaknesses: Setting up SSH keys requires a bit more technical knowledge than other methods. Users must ensure proper security measures to protect their private key, as compromising it can lead to unauthorized access. If a key is compromised, it may require more effort to revoke access compared to a password.
- Use Cases: SSH keys are excellent for developers accessing remote servers, automating tasks, and integrating with CI/CD pipelines. They are well-suited for situations where a high degree of security and automation are critical, such as managing infrastructure or deploying applications.
Two-Factor Authentication (2FA)
Two-factor authentication adds an extra layer of security by requiring two forms of verification. This usually involves a combination of something you know (e.g., a password) and something you have (e.g., a code from a mobile app). GitHub’s 2FA enhances the overall security posture, making it more difficult for unauthorized access.
- Strengths: 2FA significantly enhances security by adding a second layer of verification. It’s relatively easy to implement and can be used in conjunction with other passwordless methods. GitHub’s implementation is robust and widely used, providing a high level of trust and confidence.
- Weaknesses: 2FA relies on the user having access to the second factor (e.g., a phone). If the user loses access to their second factor, they may face difficulties accessing their account. There’s a potential risk if the second factor’s security is compromised. It might introduce slight inconvenience during the authentication process.
- Use Cases: 2FA is a crucial component for protecting any account, especially those containing sensitive information. It’s essential for protecting personal accounts, professional accounts, and business-critical systems.
Comparison Table
| Method | Strengths | Weaknesses | Use Cases |
|---|---|---|---|
| SSH Keys | High security, suitable for automation, widely supported | Requires technical knowledge, potential for key compromise | Remote server access, automated tasks, CI/CD pipelines |
| 2FA | Significant security boost, easy to implement | Reliance on second factor, potential for second factor compromise | Protecting accounts, enhancing overall security |
Security Considerations: Github Setup Passwordless Auth
Passwordless authentication, while offering significant advantages, introduces new security considerations. Proper implementation is crucial to avoid potential pitfalls and maintain the integrity of your accounts. This section will delve into the security implications, potential risks, and strategies for mitigating them, highlighting the importance of proactive security measures.The shift towards passwordless authentication necessitates a shift in mindset from relying on passwords to adopting more robust, often more complex, methods of verification.
Understanding the potential risks and implementing preventative measures is paramount to safeguarding your accounts and data.
Potential Risks and Vulnerabilities
Passwordless authentication, while eliminating the need for passwords, introduces new potential attack vectors. Compromised SSH keys, insecure storage of authentication tokens, and vulnerabilities in the underlying authentication protocols can all expose accounts to malicious actors. A compromised SSH key, for example, can grant unauthorized access to sensitive data and systems. The security of the entire system hinges on the security of the key.
Mitigating Security Risks
Several measures can effectively mitigate the risks associated with passwordless authentication. These measures address potential vulnerabilities and enhance the overall security posture.
- Strong Key Management: Implementing robust key management practices is crucial. This includes using strong, unique passwords for SSH keys, storing them securely, and regularly rotating them. Regular key rotation minimizes the impact of a compromised key, ensuring that any potential breaches are limited in scope.
- Secure Key Storage: Employing secure storage mechanisms for SSH keys is essential. Avoid storing keys in easily accessible locations or using insecure file sharing services. Utilize secure key management systems or dedicated key storage solutions. Encrypted storage of keys, preferably using hardware security modules (HSMs), is strongly recommended to enhance security further.
- Two-Factor Authentication (2FA): Implementing 2FA alongside passwordless authentication adds another layer of security. This method requires two forms of authentication (something you know, and something you have), making unauthorized access significantly harder. Consider using a combination of time-based one-time passwords (TOTP) or security keys.
Importance of Regular Key Rotation
Regular key rotation is a critical security practice for passwordless authentication. Compromised keys can have severe consequences, and rotating them limits the duration of potential exposure. Key rotation ensures that even if an attacker gains access to an old key, their access is limited to the period before the key was rotated.
- Frequency: The frequency of key rotation depends on the sensitivity of the data and the level of risk tolerance. Security best practices often recommend rotating keys at least annually or more frequently if there are heightened security concerns. For example, a high-profile organization with highly sensitive data may consider quarterly rotations.
- Impact on Workflow: Regular rotation may require adjustments to workflows. Users need to be aware of the process and how to update their configuration files with the new keys. Proper documentation and communication are essential for a smooth transition.
Protecting Against Phishing and Social Engineering
Phishing and social engineering attacks can exploit vulnerabilities in user behavior to compromise accounts. Users must be vigilant and aware of these tactics to avoid becoming victims.
- Educating Users: Training users on recognizing phishing attempts is essential. Educate them on the red flags of phishing emails, messages, and websites. Phishing attempts often use deceptive tactics to trick users into revealing sensitive information, such as their SSH keys.
- Verification Procedures: Implementing robust verification procedures, such as requiring confirmation from a trusted source or using secure communication channels, is crucial. Users should be skeptical of unsolicited requests for sensitive information.
Last Point
In conclusion, mastering GitHub passwordless authentication empowers you with a more secure and efficient development environment. By understanding the different methods and implementing best practices, you can significantly enhance your GitHub security posture. Remember to prioritize security and choose the authentication method that best suits your needs and risk tolerance. This guide provides a solid foundation for your journey toward a passwordless GitHub experience.