HTTPOnly Secure Cookie Nginx A Deep Dive
Kicking off with httponly secure cookie nginx, this guide delves into the crucial security aspect of web applications. Understanding how to implement secure cookies using Nginx is paramount in today’s digital landscape, preventing vulnerabilities and safeguarding user data. We’ll cover everything from fundamental concepts to advanced configurations, including best practices and troubleshooting.
This comprehensive tutorial explains the importance of HTTPOnly and secure cookies, how to configure them with Nginx, and the security considerations to prevent common attacks. We’ll also explore cookie management, troubleshooting, and advanced customization options for optimal security.
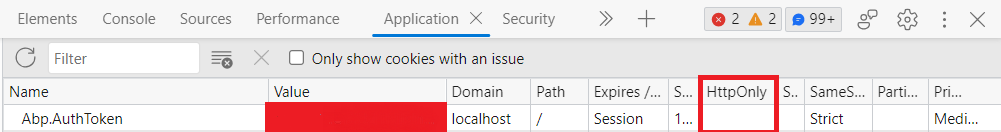
Defining HTTPOnly Secure Cookies: Httponly Secure Cookie Nginx
Cookies are essential for websites to remember user preferences and track sessions. However, improperly configured cookies can create significant security vulnerabilities. Understanding the nuances of HTTPOnly and secure cookies is crucial for building robust and trustworthy web applications.HTTPOnly cookies, a critical security measure, restrict access to cookies from client-side scripts, such as JavaScript. This significantly reduces the risk of cross-site scripting (XSS) attacks, a common method used to hijack user sessions.
Secure cookies, another important element, transmit cookies only over HTTPS connections, ensuring that data is not exposed during insecure network communication.
HTTPOnly Cookie Explanation
HTTPOnly cookies are a security feature that prevents client-side scripts, like JavaScript, from accessing the cookie values. This restriction significantly reduces the risk of XSS attacks, where malicious scripts can steal user session cookies. This is a critical safeguard against attackers who might exploit vulnerabilities in web applications to access these cookies.
Security Benefits of HTTPOnly Cookies
HTTPOnly cookies provide a robust defense against XSS attacks. Attackers using XSS can often hijack user sessions by stealing cookies. By restricting access to cookies from client-side scripts, HTTPOnly cookies mitigate this risk, as the malicious scripts cannot access the cookie data. This enhances the security of user sessions and prevents unauthorized access to sensitive data.
HTTPOnly Cookies vs. Non-HTTPOnly Cookies
Non-HTTPOnly cookies are accessible to client-side scripts. This vulnerability exposes them to XSS attacks, making them a significant security risk. In contrast, HTTPOnly cookies are inaccessible to client-side scripts, significantly reducing the threat of session hijacking and other malicious activities.
Secure vs. HTTPOnly Cookies
While both HTTPOnly and secure cookies enhance security, they address different vulnerabilities. Secure cookies ensure that cookies are transmitted over HTTPS, protecting against eavesdropping on insecure connections. HTTPOnly cookies, on the other hand, restrict access to cookies from client-side scripts, preventing malicious code from retrieving them. Both features are essential for robust cookie security.
Setting up HTTPOnly secure cookies in Nginx is crucial for web security. It prevents client-side JavaScript from accessing these cookies, a critical step in protecting user data. This is particularly important when dealing with APIs, like those used for image processing and optimization, image processing and optimization api , where sensitive data might be exchanged.
Robust security measures like HTTPOnly cookies are essential for maintaining the integrity of your application and safeguarding user information within your Nginx setup.
How HTTPOnly Cookies Prevent Client-Side Script Access
The HTTPOnly attribute, when set on a cookie, prevents client-side scripts from accessing the cookie’s value. This means that even if an attacker successfully injects malicious JavaScript into a website, the script cannot retrieve the cookie data. This is a critical difference compared to non-HTTPOnly cookies, which are directly accessible to JavaScript.
Comparison of HTTPOnly and Non-HTTPOnly Cookies
| Feature | HTTPOnly Cookie | Non-HTTPOnly Cookie |
|---|---|---|
| Accessibility by client-side scripts | No | Yes |
| Vulnerability to XSS attacks | Reduced | Increased |
| Security | Higher | Lower |
| Example Usage | Storing session information, user preferences | Storing session information, user preferences (potentially vulnerable) |
Implementing HTTPOnly Secure Cookies with Nginx
Setting HTTPOnly and Secure cookies is crucial for web application security. These attributes significantly mitigate the risk of cross-site scripting (XSS) attacks and client-side cookie theft. By restricting access to cookies from JavaScript, and ensuring only the server can transmit them, we bolster the defense against various vulnerabilities. This approach enhances the overall security posture of the application.Nginx, a powerful web server, offers a straightforward mechanism for implementing these security measures.
Its configuration allows for the precise control over cookie attributes, enabling developers to deploy secure and robust applications. This comprehensive guide will detail how to effectively configure Nginx to set HTTPOnly and Secure cookies, along with the importance of the Set-Cookie header.
Nginx Configuration for HTTPOnly Cookies
Nginx’s configuration directives are used to manage various aspects of how the server interacts with clients. Understanding the syntax and usage of these directives is essential for setting HTTPOnly and Secure cookies correctly. This section explains how to leverage Nginx’s capabilities to enforce these security measures.
Nginx Directives for Secure Cookies
The `set-cookie` directive in Nginx’s configuration file is the key for setting cookies with specific attributes. Using this directive, we can define cookies with `HttpOnly` and `Secure` attributes, thereby improving the security of the application.
- The `set-cookie` directive is used to specify the cookie’s name, value, and attributes.
- The `HttpOnly` attribute prevents client-side JavaScript from accessing the cookie.
- The `Secure` attribute restricts the transmission of the cookie to only HTTPS connections.
Examples of Nginx Configuration Snippets
The following snippets illustrate how to implement HTTPOnly and Secure cookies within Nginx configurations. These examples are crucial for practical application and demonstrate the syntax in a usable format.
location /
set-cookie $cookie_name $cookie_value expires=Fri, 31 Dec 9999 23:59:59 GMT HttpOnly;
set-cookie $cookie_name2 $cookie_value2 expires=Fri, 31 Dec 9999 23:59:59 GMT HttpOnly Secure;
# ... other server instructions ...
These examples demonstrate the flexibility of Nginx in configuring cookies with various attributes.
Syntax of Nginx Directives for Cookie Attributes
The table below Artikels the syntax for the `set-cookie` directive, detailing the essential attributes and their purpose.
| Directive | Attribute | Description |
|---|---|---|
set-cookie |
$cookie_name |
The name of the cookie. |
set-cookie |
$cookie_value |
The value of the cookie. |
set-cookie |
expires=... |
The expiration date of the cookie. |
set-cookie |
HttpOnly |
Prevents JavaScript access. |
set-cookie |
Secure |
Restricts transmission to HTTPS. |
Setting a Cookie with HttpOnly and Secure Attributes
The following example shows how to set a cookie with both the `HttpOnly` and `Secure` attributes in Nginx.
location /
set-cookie mycookie "value" expires=Fri, 31 Dec 9999 23:59:59 GMT HttpOnly Secure;
# ... other server instructions ...
This configuration ensures the cookie is only accessible via HTTPS and is protected from JavaScript.
Importance of the Set-Cookie Header in Nginx
The `Set-Cookie` header, generated by Nginx, is critical for communicating cookie information to the client’s browser. Without a properly configured `Set-Cookie` header, the browser will not receive or store the cookie, rendering the security measures ineffective.
Security Considerations and Best Practices
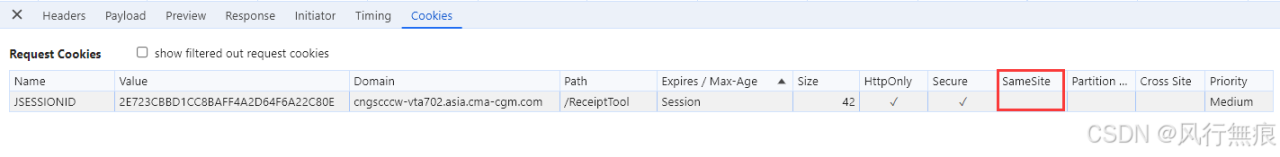
HTTPOnly and secure cookies are crucial for protecting user data, but they are not a silver bullet. Understanding potential vulnerabilities and implementing additional security measures is vital to safeguard against sophisticated attacks. This section explores potential risks and best practices to enhance the overall security posture of your web application.
While HTTPOnly and secure cookies significantly reduce the risk of cross-site scripting (XSS) and other attacks, they don’t eliminate them entirely. Understanding the remaining vulnerabilities and employing supplementary strategies is key to robust protection.
Potential Vulnerabilities of HTTPOnly and Secure Cookies
HTTPOnly cookies, by design, prevent client-side JavaScript from accessing them. However, attackers can still exploit vulnerabilities in other parts of the application, such as server-side logic or data handling. Insecure coding practices can expose sensitive data, even if HTTPOnly cookies are used correctly. Also, while secure cookies encrypt the transmission of cookies, vulnerabilities in the server-side encryption or decryption processes can still compromise the security of the data.
Attacks Bypassing HTTPOnly Cookies
Some attacks can bypass HTTPOnly cookies. Cross-site request forgery (CSRF) attacks, for instance, can trick users into performing unwanted actions on a website without their knowledge. These attacks don’t directly target the cookie itself, but exploit weaknesses in the application’s interaction with the user. Similarly, server-side vulnerabilities, like SQL injection, can leak sensitive data even if HTTPOnly cookies are in place.
Enhancing Security Beyond HTTPOnly and Secure Cookies
Implementing robust security measures beyond HTTPOnly and secure cookies is essential. These measures include input validation to prevent malicious input, output encoding to prevent XSS, and using strong encryption techniques throughout the application’s architecture. A layered approach, combining various security controls, provides a stronger defense against a broader range of attacks. This involves implementing a comprehensive security model that covers every layer of the application, from client-side validation to server-side authentication and data encryption.
Mitigating Cookie-Related Attacks
Mitigation strategies include employing input validation to sanitize user input and prevent injection attacks. Input validation helps prevent malicious scripts from being embedded into user input, which can be used to exploit vulnerabilities. Implementing proper output encoding prevents reflected XSS attacks by encoding special characters, so they are rendered harmlessly in the output. Strong password policies and multi-factor authentication enhance account security.
Securing cookies with HTTPOnly and Secure directives in Nginx is crucial for web application security. This is especially important when dealing with sensitive data, like user credentials. Interestingly, a recent real estate transaction in San Jose, a single-family residence selling for $2.4 million , highlights the importance of robust security measures in other contexts. Properly configured cookies, like those protected with HTTPOnly and Secure, prevent client-side JavaScript from accessing them, adding another layer of protection against various attacks.
This is a key aspect of web application hardening, and something every developer should consider.
Protecting Cookies from XSS Attacks
To protect cookies from XSS attacks, it’s essential to implement robust output encoding mechanisms. Encoding user-supplied data before displaying it on the web page ensures that malicious scripts cannot be executed. This is critical because reflected XSS attacks can exploit vulnerabilities in the application’s rendering of user input. Validating user input is another crucial measure to protect against XSS.
Table of Common Cookie Security Vulnerabilities and Mitigation Strategies
| Vulnerability | Description | Mitigation Strategy |
|---|---|---|
| Cross-Site Scripting (XSS) | Malicious scripts injected into user input are executed by the browser. | Input validation, output encoding, Content Security Policy (CSP) |
| Cross-Site Request Forgery (CSRF) | Users are tricked into performing unwanted actions on a website. | CSRF tokens, double submit cookie, same-site cookies |
| SQL Injection | Malicious SQL queries injected into user input can compromise database security. | Parameterized queries, prepared statements |
| Session Fixation | Attackers hijack user sessions by setting a known session ID. | Session ID generation, session timeout |
Cookie Management and Handling
Cookies are essential for maintaining user sessions and providing personalized experiences on websites. Effective cookie management is crucial for security and functionality. This section delves into how Nginx manages cookie expiry, scopes, deletion, and the impact of domains and paths, along with various management approaches.
Nginx, acting as a reverse proxy, plays a vital role in the entire cookie lifecycle. From setting the initial cookie attributes to handling expiry and deletion, Nginx offers significant control over the cookie experience for users. Understanding these functionalities empowers developers to implement robust and secure cookie mechanisms.
Nginx’s Role in Cookie Expiry Management
Nginx allows precise control over cookie expiry dates. The `expires` attribute, configured within the `set-cookie` header, dictates when the cookie should be considered invalid. By specifying a future timestamp, developers can ensure cookies remain valid for a predetermined period. This functionality is crucial for maintaining user sessions and preventing unauthorized access after a user’s session has expired.
Nginx directly manipulates the expiry timestamp when sending the cookie header to the client.
Handling Different Cookie Scopes
Nginx supports different cookie scopes, allowing for tailored control over which parts of a website can access a specific cookie. The `domain` attribute dictates the scope of the cookie, determining which subdomains can access it. The `path` attribute defines the specific URL paths where the cookie is valid. This granular control is essential for preventing unintended access to sensitive information and ensuring the proper functionality of specific sections of a website.
For example, a cookie intended for a specific section of a website should only be accessible on that specific path.
Cookie Deletion with Nginx
Nginx enables cookie deletion by setting the `expires` attribute to a past date. This effectively invalidates the cookie, preventing it from being used in subsequent requests. The `max-age` attribute can also be used to specify the number of seconds until the cookie expires, providing a convenient way to set a cookie’s lifetime. By explicitly setting the `expires` attribute to a date in the past, Nginx signals the client to discard the cookie.
Implications of Cookie Domains and Paths
The `domain` attribute dictates which subdomains can access a cookie. A well-defined domain is essential to prevent unauthorized access and maintain security. Similarly, the `path` attribute defines the URL paths where the cookie is valid. Restricting a cookie to a specific path prevents unintended access to sensitive information. For instance, a cookie intended for a shopping cart should only be valid within the shopping cart path.
Comparing Different Cookie Management Approaches
Various approaches exist for managing cookies. Server-side scripting languages can set cookies, but Nginx offers a more efficient and scalable way for handling cookies, especially in high-traffic environments. Using Nginx’s configuration for cookie management enhances performance by offloading cookie handling tasks from the application server.
Cookie Attributes and Impact
| Attribute | Description | Impact |
|---|---|---|
expires |
Specifies the date and time when the cookie expires. | Controls the cookie’s validity period. |
max-age |
Specifies the cookie’s lifetime in seconds. | Provides a convenient alternative to specifying the expiry date. |
domain |
Defines the domain where the cookie is valid. | Controls cookie access across subdomains. |
path |
Specifies the URL path where the cookie is valid. | Limits cookie access to specific parts of the website. |
secure |
Indicates that the cookie should only be transmitted over HTTPS. | Improves security by preventing eavesdropping. |
HttpOnly |
Indicates that the cookie should not be accessible by JavaScript. | Adds an extra layer of security against XSS attacks. |
Troubleshooting Common Issues
Setting up HTTPOnly and secure cookies with Nginx can sometimes lead to unexpected behavior. This section details common pitfalls and provides practical solutions to resolve issues encountered during the configuration and deployment process. Understanding these common problems and their remedies is crucial for maintaining a secure and functional web application.
Nginx Configuration Errors
Incorrect Nginx configurations are a frequent source of cookie-related problems. These errors often stem from syntax mistakes, misinterpretations of directives, or inconsistencies between the configuration and the application’s logic. Careful review and debugging are essential for identifying and rectifying these errors.
Potential Causes of Cookie Issues
Several factors can contribute to cookie problems. Mismatched settings between the Nginx server and the application, incorrect paths or domains specified in the cookie directives, and conflicts with other server configurations can lead to unexpected behavior. Additionally, issues with the application’s code handling the cookies can result in incorrect cookie setting or retrieval.
Debugging HTTPOnly and Secure Cookies in Nginx
Debugging cookie issues in Nginx involves a systematic approach. First, examine the Nginx error logs for any specific messages related to the cookie configuration. Then, analyze the server responses using tools like browser developer tools to inspect the headers and verify the presence and attributes of the cookies. Finally, ensure the application code correctly sets and retrieves the cookies.
Common Nginx Errors Related to Cookie Configuration
| Error Type | Description | Solution |
|---|---|---|
| Incorrect Syntax in `set-cookie` directive | The `set-cookie` directive might contain incorrect syntax, leading to the cookie not being set properly. | Double-check the syntax of the `set-cookie` directive, ensuring correct formatting and the presence of required parameters. |
| Missing `secure` flag | The `secure` flag is omitted in the `set-cookie` directive, causing the cookie to be sent over unencrypted connections, compromising security. | Add the `secure` flag to the `set-cookie` directive. Ensure the flag is present to enforce secure transmission. |
| Incorrect `HttpOnly` flag | The `HttpOnly` flag is incorrectly implemented in the `set-cookie` directive. | Verify the `HttpOnly` flag is correctly included in the `set-cookie` directive. Ensure the case sensitivity of the flag matches the Nginx configuration. |
| Conflicting cookie directives | Multiple conflicting directives might be present in the Nginx configuration file, leading to inconsistencies in cookie settings. | Carefully review and eliminate any conflicting directives. Verify that all cookie directives are consistent and do not contradict each other. |
Using Logging to Troubleshoot Cookie-Related Issues
Logging provides valuable insights into the behavior of the Nginx server and helps pinpoint the source of cookie problems. Comprehensive logging, including the headers exchanged between the client and server, can reveal discrepancies and inconsistencies in cookie handling. This will help in identifying if cookies are being set correctly or if there are any errors in the process.
Setting up HTTPOnly secure cookies in Nginx is crucial for web security. Protecting sensitive data is paramount, especially when dealing with user authentication. This is particularly important when considering recent discoveries like NASA’s analysis of asteroid samples, potentially revealing a watery world. NASA’s asteroid samples watery world findings highlight the importance of robust security measures, emphasizing the need for HTTPOnly secure cookies to prevent cross-site scripting attacks and safeguard user data in online applications.
Stronger security measures are needed for online services, especially when dealing with new scientific discoveries.
Enabling detailed logging for Nginx’s access logs and error logs can significantly assist in diagnosing the root cause.
Diagnosing Cookie Problems in Production Environments
Diagnosing cookie problems in production environments requires a combination of tools and techniques. Monitoring the server’s resource utilization and response times can provide clues about bottlenecks and performance issues. Utilizing application performance monitoring tools and logging can reveal potential conflicts with other services or configurations. Additionally, analyzing user behavior and identifying patterns in cookie-related errors can provide crucial information for addressing the issue.
Employing tools for analyzing network traffic between the client and server can reveal potential communication issues.
Advanced Use Cases and Customization
Cookie management using Nginx goes beyond the basics of setting HTTPOnly and Secure flags. Advanced configurations allow for granular control over cookie attributes, crucial for complex web applications and enhanced security. This section delves into customizing cookie attributes, handling multiple cookies with varying properties, and managing cookies across subdomains and paths, showcasing Nginx’s flexibility.
Nginx offers a powerful mechanism for fine-tuning cookie behavior. By leveraging its directives, you can precisely control cookie attributes, making it adaptable to specific application requirements. This flexibility extends to creating cookies for different subdomains and paths, ensuring proper data management and preventing unauthorized access.
Customizing Cookie Attributes with Nginx Directives
Nginx provides directives to modify various aspects of cookies, enabling tailoring to specific needs. The `set-cookie` directive allows you to specify attributes like `expires`, `path`, `domain`, `secure`, `httponly`, and `max-age`. These attributes can be manipulated to manage cookie lifetime, accessibility, and security.
Advanced Nginx Configurations for Complex Cookie Scenarios
More complex scenarios require nuanced configurations. For instance, managing cookies for different subdomains or handling multiple cookies with distinct attributes necessitates advanced directives and careful consideration of scope and security implications.
Setting Cookies for Different Subdomains
Nginx allows you to set cookies for specific subdomains using the `domain` attribute within the `set-cookie` directive. This is vital for applications with multiple subdomains that need to share session data or maintain user authentication.
- Example: To set a cookie for `www.example.com` and its subdomains, use `domain=example.com` in the `set-cookie` directive.
- Example: To set a cookie for `blog.example.com` without affecting `www.example.com`, use `domain=blog.example.com`.
This ensures that cookies are only accessible by the intended subdomains.
Managing Multiple Cookies with Different Attributes
Applications may require several cookies with different attributes. Nginx facilitates this by allowing multiple `set-cookie` directives within a single location block. Each directive can define unique attributes for a particular cookie, ensuring that each cookie serves its intended purpose.
Creating Custom Cookie Domains and Paths
The `domain` and `path` attributes are fundamental to controlling cookie accessibility. Nginx allows you to specify custom domains and paths, ensuring that cookies are only accessible to the designated parts of the application. This approach improves security and prevents unwanted access.
- Example: Setting a cookie with a specific path, say `/user`, ensures that the cookie is only accessible within that path and its subdirectories.
Table of Advanced Nginx Configurations for Managing Cookies
| Scenario | Nginx Configuration | Description |
|---|---|---|
| Cookie for subdomain | location / set-cookie mycookie=value; domain=example.com; |
Sets a cookie for `example.com` and its subdomains. |
| Multiple cookies with different attributes | location / set-cookie user_id=123; httponly; secure; path=/user; set-cookie session_token=abc; path=/; |
Sets two cookies with different paths and security attributes. |
| Custom cookie domain and path | location /api set-cookie myapi_token=value; domain=.myapi.com; path=/api; |
Sets a cookie for the `myapi.com` domain, accessible only within the `/api` path. |
Related Technologies and Concepts
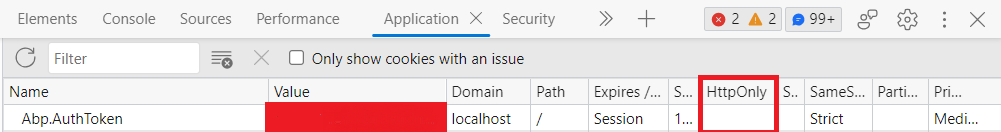
HTTPOnly and secure cookies are crucial components of a comprehensive web security strategy. Understanding their interplay with other security measures and related technologies is vital for building robust applications. This section explores the connections between cookies, sessions, security headers, storage limitations, server-side security, and other relevant technologies.
Comparison with Other Security Measures
HTTPOnly and secure cookies are part of a layered security approach. They prevent client-side script access to cookies, a common attack vector. Other security measures include input validation, output encoding, and secure coding practices. These combined defenses create a multi-faceted security posture, mitigating various attack vectors. For instance, input validation prevents malicious data from entering the system, while output encoding protects against cross-site scripting (XSS) vulnerabilities.
Secure coding practices help to prevent common coding errors that could introduce vulnerabilities. Each measure plays a specific role in strengthening overall security.
Relationship Between Cookies and Sessions
Cookies are often used to manage user sessions. A session is a series of interactions between a user and a web application within a specific timeframe. Cookies store session identifiers that the server uses to track the user’s activities across multiple requests. When a user logs in, the server creates a session and assigns a unique identifier, storing it in a cookie.
This cookie enables the server to recognize the user in subsequent requests without requiring re-authentication. This association between cookies and sessions is fundamental to maintaining user state during an online session.
Security Headers Beyond ‘Set-Cookie’, Httponly secure cookie nginx
Beyond the ‘Set-Cookie’ header, several other security headers enhance the security posture of a web application. These headers include Content-Security-Policy (CSP), X-Frame-Options, X-XSS-Protection, and Strict-Transport-Security (HSTS). CSP controls the resources a web page can load, mitigating XSS attacks. X-Frame-Options prevents clickjacking attacks. X-XSS-Protection provides browser-side protection against XSS attacks.
HSTS ensures that connections to a website are always over HTTPS, preventing man-in-the-middle attacks. These headers, in combination with HTTPOnly and secure cookies, form a robust defense against various attack vectors.
Impact of Cookie Size and Storage Limitations
Cookie size and storage limitations can impact user experience and security. Excessive cookie size can lead to performance issues and increase the risk of storage limitations on the client-side. Large cookies may also be more vulnerable to attacks that exploit data size limits. Server-side solutions and efficient storage strategies should be implemented to manage cookie size effectively.
Consider using techniques such as tokenization and data compression to reduce cookie size without sacrificing functionality.
Interplay Between Cookies and Server-Side Security
Server-side security measures are crucial in conjunction with cookies. Server-side validation, encryption, and access control are essential to protect sensitive data transmitted or stored in cookies. The server should always validate the data received from cookies and should not trust client-provided data implicitly. Strong encryption techniques should be employed to protect sensitive information within cookies. Access controls and authentication mechanisms must be properly configured to ensure only authorized users can access resources protected by cookies.
List of Related Technologies and Their Interactions with Cookies
- Session Management Systems: These systems manage user sessions and typically use cookies to store session IDs. The server uses the session ID to retrieve user data and maintain state throughout the session.
- Authentication Mechanisms: Authentication mechanisms, such as OAuth 2.0 or OpenID Connect, often rely on cookies to manage access tokens and user information. These tokens are used to verify user identity and grant access to protected resources.
- API Gateways: API gateways often use cookies for authentication and authorization, especially in the context of API-based interactions. The gateway verifies the validity of the cookie to ensure authorized access.
- Load Balancers: Load balancers can maintain session state across multiple servers by using cookies to track user interactions and route requests accordingly.
- WebSockets: WebSockets can maintain state information using cookies, allowing for continuous communication and session persistence.
Last Word
In conclusion, securing cookies with Nginx, specifically using the HTTPOnly and Secure attributes, is critical for modern web applications. This comprehensive guide provided a thorough understanding of the process, from implementation to troubleshooting and advanced use cases. By implementing these strategies, developers can significantly enhance the security of their web applications, protecting user data and maintaining trust.