Pi Hole Setup Linux A Comprehensive Guide
Pi hole setup linux is your key to a faster, more secure online experience. This guide delves into the process, from initial hardware considerations to advanced configuration and troubleshooting. Learn how to effectively manage your network’s DNS traffic, blocking unwanted websites and ads, and optimizing performance. We’ll explore different Linux distributions, installation steps, configuration options, and even advanced techniques for monitoring and security.
Whether you’re a seasoned Linux user or just starting your journey with Pi-hole, this guide provides a practical and comprehensive walkthrough. We’ll cover everything from basic installation to advanced customization, ensuring you have a solid foundation for a well-configured Pi-hole server.
Introduction to Pi-hole on Linux
Pi-hole is a powerful, open-source DNS server designed primarily to block unwanted advertisements and trackers. It intercepts DNS requests and redirects them to a clean DNS server, effectively filtering out malicious or unwanted content. This helps improve browsing experience, privacy, and security, especially on networks with multiple users.By running Pi-hole on Linux, you leverage the flexibility and stability of the operating system.
This allows for fine-grained control over network traffic, customization, and the potential for integration with other Linux-based tools. This approach is preferred by many users due to the versatility and control it offers.
Hardware Setup Considerations
A dedicated hardware setup for Pi-hole is not overly complex. A Raspberry Pi is a common choice, providing a low-cost, compact, and energy-efficient option. However, the choice depends on the anticipated volume of network traffic and the number of devices connected. For small to medium-sized networks, a Raspberry Pi 4 or 3 Model B+ is sufficient. If your network anticipates high volumes of traffic, a more powerful single-board computer or a dedicated server might be more suitable.
Consider factors such as processing power, RAM, and storage space when selecting the hardware. A stable power supply is also essential to avoid interruptions.
Common Use Cases
Pi-hole finds wide application in various scenarios. For home networks, it’s used to improve browsing experience by blocking ads and trackers, enhancing user privacy, and preventing children from accessing inappropriate content. Businesses can utilize Pi-hole to control network traffic, block unwanted websites, and improve productivity. Educational institutions can leverage Pi-hole to filter inappropriate content and maintain a safe learning environment.
The flexibility of the setup allows for many tailored applications.
Linux Distributions for Pi-hole
Several Linux distributions are suitable for running Pi-hole, each with its own advantages and disadvantages. Choosing the right distribution depends on your familiarity with the operating system and the specific needs of your setup.
| Distribution | Pros | Cons |
|---|---|---|
| Ubuntu | Widely used, extensive community support, readily available packages, easy to install and configure. | Can be resource-intensive compared to others, sometimes lagging in updates. |
| Debian | Stable, reliable, and long-term support. Known for its robustness and security. | Can have a steeper learning curve for new users, fewer readily available pre-built packages for Pi-hole. |
| Arch Linux | Highly customizable, lightweight, and excellent performance. Excellent for users seeking maximum control. | Steep learning curve, requires more technical expertise, and potential for instability if not properly configured. |
| Fedora | Focuses on bleeding-edge technology, regular updates, and access to the latest software. | Updates can be more frequent, potentially introducing instability, and requiring more technical expertise. |
Installation and Configuration
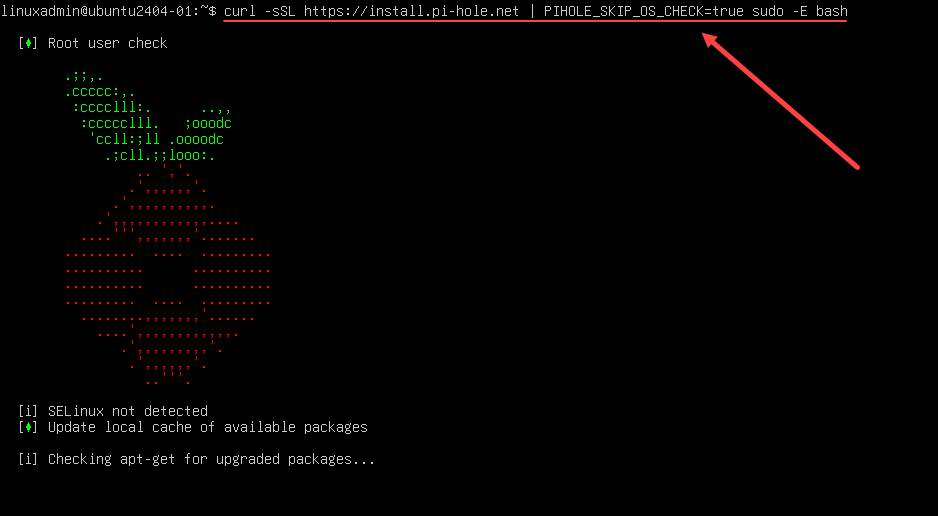
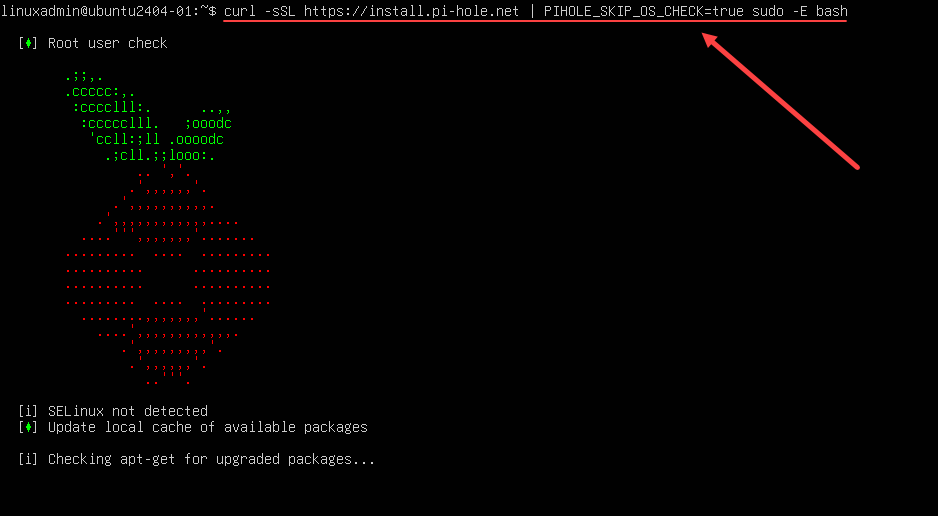
Setting up Pi-hole on your Linux machine is a straightforward process. This guide will walk you through the installation, configuration, and customization of Pi-hole to optimize your network’s DNS filtering. Proper configuration ensures that your network is protected from malicious websites and unwanted content.The configuration process involves installing the Pi-hole package, configuring DNS filtering settings, and managing custom blocklists.
Understanding these steps allows you to tailor Pi-hole to your specific network requirements and preferences.
Installing Pi-hole
The installation process varies slightly depending on your chosen Linux distribution. However, a common approach involves using your distribution’s package manager. For example, on Debian-based systems like Ubuntu, you can use `apt`. This method simplifies the installation by handling dependencies automatically. After installation, you need to configure Pi-hole’s settings for DNS filtering.
Configuring DNS Filtering
Pi-hole’s core function is DNS filtering. This involves configuring Pi-hole to act as your network’s DNS server. This server intercepts DNS queries and checks them against a blocklist of malicious or unwanted domains. This process prevents your devices from accessing these domains.Configuring Pi-hole’s DNS settings typically involves modifying your network’s configuration to point all DNS requests to Pi-hole’s IP address.
This ensures that Pi-hole handles all DNS queries for your network.
Adding Custom Domains or Exceptions
Sometimes, you might want to allow access to specific domains that are on the blocklist. Pi-hole allows you to add custom exceptions. This process involves adding entries to Pi-hole’s configuration files, enabling specific domains to bypass the filtering process.To add a custom exception, you can either use the Pi-hole web interface or modify the configuration files directly. Adding exceptions allows you to control which domains your network devices can access.
Configuring DNS Settings for Different Network Environments
The DNS configuration process might vary depending on your network environment. For example, a home network typically involves configuring your router to forward DNS requests to Pi-hole. This setup ensures that all devices on your network use Pi-hole as their DNS server. A corporate network, however, may require more complex configuration, potentially involving a dedicated DNS server.Different network setups require different configuration strategies.
Setting up Pi-hole on Linux is surprisingly straightforward. It’s a great way to block ads and improve your network’s performance. Considering the current housing market in San Jose, finding affordable homes and apartments san jose affordable home apartment economy property real estate house is a challenge, but the benefits of a clean browsing experience are definitely worth it.
Once set up, your browsing experience will be noticeably cleaner and faster.
The correct configuration ensures that Pi-hole functions seamlessly within your network infrastructure.
Setting up Pi-hole on Linux can be surprisingly straightforward, especially if you follow a good tutorial. While that’s all well and good, it’s also important to remember the gravity of human tragedy, like the recent sentencing of a Daly City man to 15 years to life for killing his estranged wife while their son was in another room. This horrific event reminds us of the importance of strong community support and resources for those experiencing family conflict.
Thankfully, setting up Pi-hole can be a positive distraction from such weighty issues, and a great way to enhance your home network.
Common Configuration Options and Their Impact
| Option | Description | Impact |
|---|---|---|
| Blocklist | Specifies the list of domains to block. | Determines which domains are filtered from access. |
| DNS Server | The IP address of the Pi-hole server. | Directs DNS queries to Pi-hole for filtering. |
| Update Frequency | How often Pi-hole updates its blocklist. | Impacts the timeliness of blocking malicious or unwanted domains. |
Advanced Configuration and Customization
Pi-hole, while offering a streamlined setup, allows for extensive customization to tailor its behavior to specific network needs. This advanced configuration unlocks performance optimization, enhanced security integration, and detailed monitoring capabilities. This section delves into the nuances of fine-tuning Pi-hole beyond the basic installation.Beyond the initial configuration, Pi-hole offers granular control over its operation. These advanced options provide administrators with the tools to optimize performance and security, adapting Pi-hole to their particular network infrastructure.
Fine-Tuning Pi-hole’s Behavior
Pi-hole’s advanced configuration options allow for precise control over its functionality. These settings enable administrators to optimize DNS resolution, manage access lists, and fine-tune its interaction with other network elements. Adjusting the cache time, for instance, can improve responsiveness while maintaining data integrity. Implementing custom DNS rules empowers users to implement specific filtering and redirecting strategies.
Monitoring Pi-hole’s Performance and Logs
Effective management of Pi-hole hinges on diligent monitoring. Regular review of performance metrics and logs helps in identifying bottlenecks, troubleshooting issues, and understanding the overall health of the system. Pi-hole’s logs provide valuable insights into its activities, enabling administrators to diagnose and rectify problems.Pi-hole’s logging system provides a comprehensive record of its activities. This allows administrators to identify and address issues promptly.
By analyzing access, query, and block logs, they can understand how Pi-hole is performing in their network.
Optimizing Pi-hole’s Performance
Optimizing Pi-hole’s performance on different hardware configurations requires careful consideration of factors like CPU usage, memory allocation, and network bandwidth. Selecting the right hardware, ensuring sufficient RAM, and utilizing efficient configuration settings are crucial steps.For example, on resource-constrained systems, reducing the cache time or using optimized DNS servers can enhance performance. Conversely, on more powerful systems, expanding the cache time might offer improved response times.
Integrating Pi-hole with Other Network Security Tools
Integrating Pi-hole with other network security tools can enhance overall network security. Integrating with a firewall, intrusion detection system (IDS), or other security appliances can create a layered defense strategy. This synergy strengthens network protection by combining the strengths of various security measures.For instance, integrating Pi-hole with a firewall can block malicious traffic originating from external sources before it even reaches the DNS server.
Logging Options for Pi-hole
Pi-hole’s logging capabilities provide detailed insights into its operations. This data is invaluable for troubleshooting, performance analysis, and security audits. Different log types capture varying aspects of Pi-hole’s behavior.
| Log Type | Description | Configuration |
|---|---|---|
| Access Logs | Records all DNS queries made to Pi-hole. | Enables detailed analysis of query patterns and origins. |
| Query Logs | Details the queries Pi-hole receives and how they are handled. | Essential for performance evaluation and troubleshooting issues. |
| Block Logs | Provides a record of blocked queries. | Helpful in identifying and managing blocked domains or IP addresses. |
Troubleshooting and Maintenance
Setting up Pi-hole on Linux can be a rewarding experience, but like any complex system, it requires attention to detail and proactive troubleshooting. This section delves into common issues and effective strategies for maintaining a stable and efficient Pi-hole environment. Addressing problems promptly can prevent frustration and ensure uninterrupted service.Troubleshooting a Pi-hole setup involves identifying the root cause of any observed issues.
A methodical approach, focusing on specific aspects like network connectivity, DNS resolution, and service stability, is crucial for efficient troubleshooting. By systematically investigating potential problems, you can restore optimal functionality.
Common Pi-hole Setup Issues
Troubleshooting begins with recognizing typical issues. These can range from network connectivity problems to DNS resolution failures and service disruptions. Understanding these common issues helps in isolating the problem and implementing effective solutions.
- Network Connectivity Problems: Issues with network connectivity are a frequent source of frustration. These can stem from incorrect network configuration on the Pi, firewall restrictions, or problems with the network infrastructure itself. Understanding how Pi-hole interacts with the network is vital to identify the cause of any connectivity problems.
- DNS Resolution Issues: DNS resolution failures can manifest as websites not loading or applications failing to connect. Incorrect DNS server configuration, conflicts with other network services, or issues with the Pi-hole configuration itself can be the culprit. Understanding how DNS queries flow through the network is important to resolve these issues.
- Pi-hole Service Instability: Pi-hole’s service may become unresponsive, causing various issues. This could be due to resource constraints on the Pi, conflicts with other running processes, or software bugs. Recognizing the symptoms of service instability is key to resolving the underlying problem.
Troubleshooting Network Connectivity
Network connectivity problems are often the first hurdle in Pi-hole troubleshooting. Identifying the specific network issue is crucial for implementing a targeted solution.
- Verify Network Configuration: Ensure the Pi’s network configuration matches the local network settings. Double-check IP address, subnet mask, gateway, and DNS server settings. Using the `ip addr` command in the terminal can verify the network interface configuration. Misconfigured settings can lead to connectivity problems.
- Check Firewall Rules: Firewalls can block Pi-hole’s communication. Ensure the firewall on the router and/or the Pi allows necessary ports (usually port 53 for DNS). Firewall rules can be adjusted using the router’s configuration interface or the `ufw` command on Linux.
- Examine Network Cables and Connections: Verify that all network cables are properly connected and functioning correctly. Loose or damaged cables can cause intermittent connectivity issues. Inspect the network cables and ensure the connections are secure.
Resolving DNS Resolution Issues
DNS resolution issues can stem from various causes. Carefully diagnosing and resolving these issues is vital for Pi-hole’s smooth operation.
- Verify Pi-hole’s DNS Configuration: Ensure Pi-hole is configured to use the correct DNS servers. Verify that the DNS settings within Pi-hole match the network configuration. Incorrect DNS settings can lead to DNS resolution failures.
- Check for Conflicts with Other Services: Conflicting services running on the same network or the Pi itself can interfere with DNS resolution. Identify and resolve any conflicts to ensure smooth operation. Conflicting services can interfere with Pi-hole’s operation.
- Check DNS Server Availability: Confirm that the DNS servers Pi-hole is using are accessible and operational. If the DNS servers are unreachable, the issue must be resolved before continuing with the troubleshooting steps.
Backing Up and Restoring Pi-hole Data
Regular backups are essential for safeguarding your Pi-hole configuration. Data loss can be catastrophic, so consistent backups are crucial.
- Using `pihole-cli`: The `pihole-cli` tool provides a simple and efficient way to back up and restore Pi-hole data. This command-line tool streamlines the process and ensures data integrity. Use `pihole-cli backup` and `pihole-cli restore` commands to back up and restore data.
- Manual Backup of Configuration Files: Back up the `pihole.conf` file and other relevant configuration files to a secure location. Manual backups offer flexibility but require more attention to detail.
Common Error Messages and Solutions, Pi hole setup linux
A clear understanding of common errors and their solutions is essential. This will help quickly resolve issues.
| Error | Solution |
|---|---|
| “Pi-hole not responding” | Check for resource constraints (CPU, RAM) on the Pi. Restart the Pi-hole service. If the issue persists, investigate potential conflicts with other services or processes. |
| “DNS resolution failure” | Verify Pi-hole’s DNS configuration. Check for conflicts with other network services. Ensure the DNS servers Pi-hole uses are accessible and functional. |
Security Considerations: Pi Hole Setup Linux
Running a Pi-hole on Linux, while offering significant benefits, introduces security concerns that must be addressed proactively. Proper configuration and vigilance are crucial to prevent unauthorized access and potential data breaches. A well-secured Pi-hole not only protects your network but also maintains the privacy of users accessing your network.Protecting your DNS infrastructure is paramount, as it forms the foundation of your network’s communication.
A compromised Pi-hole can expose your network to various threats, ranging from simple disruptions to sophisticated attacks. This section delves into critical security aspects, offering practical recommendations for bolstering the security posture of your Pi-hole server.
Securing the Pi-hole Server
A secure Pi-hole server starts with robust access controls. Restricting access to the Pi-hole server is paramount to prevent unauthorized modifications or exploitation. Employing strong passwords and enabling SSH key authentication enhances the security posture considerably.
- Restrict Network Access: Limit network access to the Pi-hole server using firewall rules. Only allow connections from trusted sources to prevent unauthorized access from external networks.
- Strong Passwords: Utilize strong, unique passwords for all accounts, including SSH and Pi-hole administrative accounts. Employ a password manager to generate and store these complex passwords securely.
- SSH Key Authentication: Implement SSH key authentication to eliminate the need for passwords and enhance security by using SSH keys for authentication.
Configuration Security Best Practices
Careful configuration is critical to maintaining the security of your Pi-hole server. The default configuration may not be sufficient for all environments.
- Firewall Rules: Configure firewall rules to only allow necessary traffic to the Pi-hole server. Block unnecessary ports and services to reduce the attack surface.
- DNSSEC Configuration: Implementing DNSSEC (DNS Security Extensions) strengthens the integrity and authenticity of DNS responses, preventing spoofing attacks.
- Regular Updates: Keep the Pi-hole software and any dependencies up-to-date to patch security vulnerabilities. Follow the official Pi-hole release schedule for timely updates.
Handling Sensitive DNS Data
DNS queries often contain sensitive information. Protecting this data is essential for maintaining user privacy. Proper logging and data handling procedures are crucial.
Setting up Pi-hole on Linux is surprisingly straightforward, especially if you’re comfortable with the command line. While researching different methods, I stumbled across some fascinating discussions about, say, asking Eric Thomas about his dominant daughter-in-law , which, frankly, had me slightly distracted. But, back on topic, a well-configured Pi-hole can significantly improve your network’s performance and security.
- Log Management: Implement a robust logging system for DNS queries, allowing for auditing and analysis of network activity. Store logs securely, adhering to relevant data privacy regulations.
- Data Retention Policies: Define clear data retention policies for DNS logs, ensuring compliance with legal requirements and privacy standards. Regularly review and purge unnecessary logs.
Mitigating Potential Vulnerabilities
Pi-hole, like any software, can have vulnerabilities. Proactive mitigation is essential.
- Vulnerability Scanning: Regularly scan the Pi-hole server for known vulnerabilities using tools like Nessus or OpenVAS to proactively identify and address potential weaknesses.
- Security Audits: Conduct periodic security audits to identify potential vulnerabilities in the configuration and implementation of Pi-hole, ensuring that the server is configured and implemented in a secure manner.
Protecting from Unauthorized Access
Unauthorized access can lead to significant security breaches. Protecting the Pi-hole server from such attempts is crucial.
- Intrusion Detection/Prevention Systems (IDS/IPS): Deploy an IDS/IPS to detect and block malicious network activity targeting the Pi-hole server, enhancing the security posture.
- Regular Monitoring: Monitor the Pi-hole server’s logs and system activity for unusual patterns or suspicious behavior. Promptly address any anomalies detected.
Monitoring and Reporting
Pi-hole’s effectiveness hinges on diligent monitoring and reporting. Understanding how your network is performing, which domains are being blocked, and overall traffic patterns is crucial for optimizing its functionality and maintaining network health. Regular monitoring allows for proactive identification and resolution of potential issues.
Performance Metrics Monitoring
Pi-hole provides a wealth of performance metrics accessible through its web interface. These metrics offer insights into various aspects of its operation, from the number of DNS queries processed to the CPU load. Regularly checking these metrics allows you to identify trends and potential bottlenecks.
Generating Reports on Blocked Domains and Traffic Patterns
Pi-hole’s reporting capabilities extend beyond basic statistics. It can generate detailed reports on blocked domains, categorized by type or frequency. This allows administrators to understand the types of content being blocked and the impact on user experience. Furthermore, it provides insights into traffic patterns, which can reveal trends in network usage and identify potential security concerns.
Utilizing Tools for Monitoring Pi-hole’s Status
Several tools are available for monitoring Pi-hole’s status. The built-in web interface is a fundamental tool, offering real-time insights into key metrics. Additionally, third-party monitoring tools can provide comprehensive dashboards, detailed reports, and alerts for specific conditions.
Creating a Pi-hole Monitoring Dashboard
Creating a custom dashboard for Pi-hole monitoring often involves integrating the Pi-hole web interface with other monitoring tools. This integration allows for visualization of critical metrics and facilitates trend analysis. For example, integrating Pi-hole with Grafana, a popular open-source data visualization tool, can create a dynamic dashboard displaying real-time performance data and historical trends.
Key Performance Indicators (KPIs) for Pi-hole
Monitoring Pi-hole’s performance is essential. The following table Artikels key performance indicators (KPIs) that are crucial for evaluating its effectiveness and identifying potential issues.
| KPI | Description | Target Value |
|---|---|---|
| DNS Queries per Second | The rate at which DNS queries are processed. | Dependent on network traffic and configuration. Ideally, should be sustainable without noticeable delays. |
| Blocked Domains | The number of domains blocked by Pi-hole. | Should correlate with the expected filtering activity. |
| Server CPU Usage | The percentage of CPU utilized by the Pi-hole server. | Should remain below 80% to avoid performance degradation. High usage might indicate a need for optimization or hardware upgrade. |
Last Point
In conclusion, setting up Pi-hole on Linux empowers you to take control of your network’s DNS traffic. This guide has provided a detailed roadmap, from initial setup to advanced customization and troubleshooting. By following the steps Artikeld, you’ll gain valuable insights into optimizing your network’s performance and security, while enhancing your overall online experience. Remember to adapt the configurations to your specific needs and environment for the best results.