Test Origin IP Exposed A Deep Dive
Test origin IP exposed is crucial for web security. Understanding how your application reveals its server’s IP address is vital for preventing potential attacks. This in-depth exploration covers everything from the basics of origin IP exposure to advanced mitigation strategies and troubleshooting techniques. We’ll delve into real-world examples and explore various testing methods, ensuring you have a comprehensive understanding of this critical security aspect.
From common vulnerabilities to the most sophisticated attacks, this guide will equip you with the knowledge and tools to proactively address the risk of exposed origin IPs. We’ll examine the impact of these exposures, the methods to identify them, and effective strategies to prevent and mitigate them.
Understanding the Concept of Test Origin IP Exposure
In the realm of web application and API development, security is paramount. One critical aspect of security testing is identifying potential vulnerabilities, including the exposure of a test origin IP address. Understanding how this exposure can occur and its implications is essential for robust application design and secure testing practices.
Meaning of “Test Origin IP Exposed”
A test origin IP exposed means that the actual IP address of the machine or server initiating the test is visible to the target application or API. This visibility is unintended and can potentially expose sensitive information or create unexpected interactions during the testing process.
Scenarios of Relevance
Test origin IP exposure is relevant in various testing scenarios. For instance, automated testing frameworks might inadvertently expose the testing machine’s IP, while manual testing using a local machine might also reveal the origin IP.
Contexts Where It’s a Concern
The exposure of a test origin IP can be a concern in several contexts. Web applications, APIs, and internal systems can all be impacted if test traffic originates from an identifiable IP address. This could lead to potential security breaches or unexpected results during testing.
Ever wondered how to test the origin IP address exposed? It’s a crucial step in web security, especially when dealing with potentially malicious requests. While the closing of the Danville Bowl after 64 years danville bowl closing after 64 years is a sad local story, understanding these technical aspects of web security is vital for preventing unauthorized access.
This knowledge helps prevent issues like data breaches or other vulnerabilities. Knowing how to test the origin IP exposed helps ensure your systems are secure.
Common Use Cases
Several common use cases highlight the importance of addressing test origin IP exposure. Testing load balancers, verifying API endpoints, and simulating user behavior all require careful consideration of the origin IP. Failing to account for this can lead to inaccurate results and security vulnerabilities.
Table Illustrating Applications and Potential for Origin IP Exposure
| Application Type | Potential for Origin IP Exposure | Impact |
|---|---|---|
| Web Application (eCommerce) | High. Automated load testing tools often expose the testing server’s IP. | Potential for revealing internal network details, causing inaccurate load balancing estimations, and possibly triggering security alerts. |
| Mobile API (Banking App) | Medium. Simulators and testing devices can be easily identifiable. | Potential for unauthorized access to API endpoints if the test origin IP is not properly masked. |
| Internal System (CRM) | Low. If the internal system has firewall rules to block external IPs, exposure may be less significant. | Exposure could still reveal internal network topology if not addressed. |
| Cloud-based API (Social Media) | Variable. Depends on the specific API and cloud provider configuration. | Misconfigured APIs can expose the origin IP, leading to unwanted traffic or security incidents. |
Impact and Consequences

Exposing your server’s origin IP address can open a Pandora’s Box of security vulnerabilities. While seemingly a minor detail, this seemingly innocuous information can be leveraged by malicious actors to launch various attacks, potentially leading to significant damage. This exposure creates a direct path for attackers to exploit your system, making it critical to understand the implications.Understanding the implications of exposed origin IPs requires a nuanced approach, going beyond simple technical descriptions.
It involves acknowledging the potential for substantial financial losses, reputational damage, and disruption of services. A comprehensive grasp of the risks and attack vectors is essential for effective mitigation strategies.
Security Implications of Exposed Origin IPs
Exposing origin IPs provides attackers with valuable information for launching attacks. This direct access allows for various malicious activities, from simple denial-of-service attacks to more sophisticated exploits targeting the underlying infrastructure. The severity of these attacks can range from minor inconveniences to catastrophic failures.
Potential Risks Associated with Exposed Origin IPs
The potential risks stemming from exposed origin IPs are multifaceted and serious. Attackers can leverage this information to launch targeted attacks, exploit vulnerabilities, and gain unauthorized access to sensitive data. The impact can extend beyond the immediate system, potentially affecting user data and services reliant on the exposed server.
Methods of Exploiting Exposed Origin IPs, Test origin ip exposed
Attackers can exploit exposed origin IPs in several ways. A common method involves using the IP address to identify the server’s location, enabling targeted denial-of-service (DoS) attacks. Further, the IP address could reveal valuable information about the server’s configuration, enabling more sophisticated attacks that exploit known vulnerabilities. The availability of the IP address significantly enhances an attacker’s ability to pinpoint and target the system.
Examples of Attacks Leveraging Exposed Origin IPs
Several types of attacks can be launched when origin IPs are exposed. One example is a geographically targeted DoS attack. By knowing the origin IP, attackers can flood the server with traffic from the same region, overwhelming the system and disrupting service. Another example is exploiting vulnerabilities that are specific to the server’s operating system or application, a risk significantly heightened by the exposure of the origin IP.
Knowing the origin IP can also lead to attacks aimed at specific services or applications.
Comparison of Attack Vectors and Potential Impact
| Attack Vector | Description | Potential Impact |
|---|---|---|
| Targeted Denial-of-Service (DoS) | Flooding the server with traffic from the same geographic location. | Disruption of service, potential website downtime, and impact on users. |
| Exploiting Known Vulnerabilities | Leveraging known weaknesses in the server’s operating system or applications. | Unauthorized access, data breaches, and potential compromise of the entire system. |
| Man-in-the-Middle (MitM) Attacks | Intercepting communication between the client and server. | Unauthorized data access, manipulation of data, and potential compromise of user credentials. |
| Resource Exhaustion Attacks | Overloading server resources, such as CPU or memory. | Disruption of service, potential crashes, and inability to handle legitimate requests. |
Methods for Testing
Uncovering exposed origin IPs is crucial for securing web applications. Improper configuration can leave these vital components vulnerable, exposing sensitive data and potentially impacting the entire system. This section delves into various testing methods, tools, and methodologies to identify and address these vulnerabilities effectively.
Identifying Exposed Origin IPs
A common method for identifying exposed origin IPs involves passively monitoring network traffic. Tools and techniques like port scanning, and packet capture can reveal servers listening on specific ports, which could potentially expose origin IPs. Careful observation of network traffic patterns, particularly those associated with web requests and responses, can often pinpoint servers that are not properly secured.
Tools can be configured to monitor for specific ports or protocols, such as HTTP or HTTPS, to focus the search.
Tools for Testing Origin IP Exposure
Several tools are available to aid in identifying exposed origin IPs. These tools offer varying capabilities, from simple port scanning to more sophisticated penetration testing functionalities. Choosing the right tool depends on the specific needs and scope of the test.
Testing Tools and Capabilities
| Tool | Capabilities |
|---|---|
| Nmap | A powerful and versatile open-source port scanner. It can identify open ports on target servers, allowing for the detection of potential origin IP exposures. Nmap can also provide detailed information about the services running on the detected ports. |
| Masscan | Known for its speed and ability to scan a vast number of IP addresses rapidly. It is ideal for large-scale network vulnerability assessments, effectively identifying potentially exposed origin IPs across extensive ranges. |
| Burp Suite | A comprehensive security testing platform, Burp Suite allows for more in-depth analysis of web applications. It can be used to identify misconfigurations that expose origin IPs during HTTP requests. |
| OWASP ZAP | Another open-source security testing tool that can be used to identify various vulnerabilities, including those related to origin IP exposure. It facilitates automated scanning and manual analysis to pinpoint potentially exposed IPs. |
Configuring Tools for Effective Testing
Proper configuration is essential for effective testing. This includes specifying the target IP range, ports to scan, and the protocols to monitor. Nmap, for example, offers a wide range of options for customizing scans, from basic port scans to more intricate OS detection. Tools like Burp Suite or OWASP ZAP often have user interfaces to help configure parameters for more targeted testing of web applications.
Penetration Testing Methodologies
Penetration testing methodologies provide a structured approach to evaluate the security of a system. The methodology should involve various stages, including reconnaissance, vulnerability analysis, exploitation, and reporting. Specific techniques for origin IP exposure testing involve examining HTTP headers, analyzing web application logs, and simulating various attack scenarios to identify potential vulnerabilities. During the exploitation phase, penetration testers can attempt to exploit vulnerabilities found in the analysis phase, to confirm whether a specific origin IP is exposed.
Thorough documentation of the process and findings is crucial to provide actionable insights.
Testing the origin IP address exposed can sometimes be tricky, especially when dealing with the economic growth of a city like San Jose. A robust retail sector, building new properties, and the overall real estate development in places like San Jose san jose store retail build property economy real estate develop jobs often requires careful consideration of network security.
Understanding these exposed IPs is crucial for maintaining safety and stability, which in turn influences the growth of the economy and job creation.
Mitigation Strategies
Protecting your web application’s origin IP address is crucial for security and preventing potential attacks. Knowing how to effectively mitigate this exposure is vital to maintain confidentiality and integrity. This involves understanding the various methods available to mask the server’s identity and implementing robust security measures across all components.
Common Approaches for Mitigation
Several strategies are employed to shield origin IPs. These include using proxies, load balancers, and CDNs (Content Delivery Networks). These methods act as intermediaries between the client and the origin server, obscuring the server’s true IP address.
Techniques for Configuring Web Servers and Applications
Proper configuration of web servers and applications is paramount. A common technique is to utilize reverse proxies. These proxies sit in front of the origin server, receiving client requests and forwarding them to the appropriate backend server. This effectively hides the origin server’s IP address from direct client interaction.
Best Practices for Securing APIs and Web Applications
API security plays a significant role in mitigating origin IP exposure. Using API gateways and rate limiting can help manage access and prevent abuse. Employing proper authentication mechanisms, such as OAuth 2.0, ensures only authorized users can access the API. Regular security audits and penetration testing are also crucial for identifying vulnerabilities and addressing them proactively.
Steps to Implement Security Measures
Implementing security measures is a multi-step process. A prioritized list for mitigating origin IP exposure is presented below:
- Identify Potential Vulnerabilities: Conduct a thorough security assessment of your web application and APIs to pinpoint potential entry points for attackers seeking to exploit origin IP exposure. Tools and techniques for identifying vulnerabilities should be used.
- Implement Reverse Proxies: Utilize reverse proxies such as Nginx or Apache to sit in front of your origin servers. This hides the origin server’s IP address behind a proxy server.
- Employ Load Balancers: Distribute traffic across multiple servers using a load balancer. This obscures the origin server behind a distributed network.
- Configure Secure Headers: Implement HTTP headers such as X-Forwarded-For and X-Real-IP. These headers allow your application to track the client’s IP address without revealing the origin server’s IP address. This is crucial for security and tracking user behavior.
- Regular Security Audits: Conduct routine security audits to detect and address any potential vulnerabilities. This helps to maintain a robust security posture and prevent potential breaches.
Secure Header Configuration
Configuring secure headers, particularly X-Forwarded-For and X-Real-IP, is essential. These headers provide crucial information about the client’s IP address without revealing the origin server’s IP. This configuration helps to maintain the privacy of the origin server and enhances the security posture of the application. Proper implementation of these headers significantly improves the security of web applications by preventing attacks that rely on knowing the origin server’s IP.
Practical Examples: Test Origin Ip Exposed
Understanding how origin IPs are exposed in web applications is crucial for securing them. This section delves into practical examples demonstrating the vulnerabilities and how to mitigate them. We’ll cover code examples in JavaScript and Python, modifications to mask origin IPs, proxy usage, and how different frameworks handle these issues.
JavaScript Example (Vulnerable)
A simple JavaScript fetch request can inadvertently expose the origin IP. This is due to the lack of proper proxying or headers manipulation.
fetch('/api/data')
.then(response => response.json())
.then(data => console.log(data));
This code directly communicates with the server. The server’s response headers, which might contain the client’s IP address, will be transmitted to the client’s browser. If the server is not configured to properly mask the IP, this is a potential vulnerability.
JavaScript Example (Masked)
Modifying the previous example to use a reverse proxy, which sits between the client and the server, effectively masks the client’s IP address.
fetch('https://proxy.example.com/api/data')
.then(response => response.json())
.then(data => console.log(data));
In this scenario, the client interacts with a proxy server. The proxy server then communicates with the actual origin server on behalf of the client, hiding the client’s IP address from the origin server.
Python Example (Vulnerable)
A Python script using the requests library can also expose the origin IP if not configured properly.
import requests
response = requests.get('http://api.example.com/data')
print(response.text)
The `requests` library, by default, might include headers that reveal the client’s IP address to the server.
Python Example (Masked)
The `requests` library can be configured to use proxies, masking the origin IP.
import requests
proxies = 'http': 'http://proxy.example.com:8080', 'https': 'http://proxy.example.com:8080'
response = requests.get('http://api.example.com/data', proxies=proxies)
print(response.text)
Using the `proxies` dictionary, the request is routed through a proxy server, obscuring the client’s IP.
Framework-Specific Handling
Different web frameworks handle origin IP exposure differently. Some frameworks have built-in mechanisms to hide the origin IP or provide methods for developers to configure proxying. Others require explicit configuration or the use of external libraries.
Framework Comparison Table
| Framework | Origin IP Handling | Comments |
|---|---|---|
| Django (Python) | Can use proxies; often requires middleware or custom configuration for masking. | Requires additional configuration if the default settings don’t mask the IP. |
| Flask (Python) | Similar to Django; can be configured using proxies. | Flask is flexible, allowing developers to implement custom proxy solutions. |
| Express.js (Node.js) | Uses middleware to handle proxying; developers need to explicitly use a proxy. | Provides great flexibility with middleware. |
| Ruby on Rails | Generally requires explicit proxy configuration. | Rails frameworks often have mechanisms to handle proxies. |
Troubleshooting Exposed IPs
Pinpointing and rectifying exposed origin IPs requires a systematic approach. This involves understanding potential causes, identifying misconfigurations, and implementing robust validation techniques to safeguard against future exposures. Careful analysis and diligent troubleshooting are crucial to restoring security and preventing further issues.
Common Troubleshooting Steps
A structured troubleshooting process is essential when dealing with exposed origin IPs. Initial steps involve confirming the exposure, determining the affected systems, and gathering relevant logs and configurations. These logs often contain valuable clues regarding the cause of the exposure. Thorough examination of these records is crucial to pinpoint the root cause and initiate corrective actions.
Figuring out how to test the origin IP exposed can be tricky, but it’s important for security. Thinking about safe play environments for babies, like soft and safe baby mats for playtime fun , also highlights the need for secure online environments. Ultimately, understanding and securing your origin IP is key to both protecting digital spaces and creating safe spaces for little ones.
Potential Causes of Origin IP Exposure
Several factors can contribute to origin IP exposure. Misconfigured server settings, particularly within web servers or application gateways, are a primary cause. Incorrectly configured headers, such as X-Forwarded-For, are another frequent culprit. Furthermore, outdated or vulnerable software versions on the origin server can leave it susceptible to exploitation, exposing its IP address. Finally, insecure coding practices, such as lack of proper input validation, can lead to vulnerabilities that allow exposure.
Identifying Misconfigurations Leading to Exposed Origin IPs
Precisely identifying misconfigurations that lead to exposed origin IPs necessitates a detailed review of server configurations. Focus on header settings, particularly X-Forwarded-For and similar headers. Examine the server’s firewall rules and access controls to identify any potential loopholes that might be exposing the origin IP. Examine the application codebase for vulnerabilities that could be exploited to expose the origin IP.
Identifying and Correcting Misconfigured Headers
Misconfigured headers are a common source of origin IP exposure. Thorough analysis of header configurations is paramount. Inspect server logs for instances of improperly formatted or missing headers. Consult documentation and best practices to ensure that headers are configured correctly and in compliance with security standards. Modify server configurations to implement appropriate header settings to prevent origin IP exposure.
Validating Origin IP Protection Measures
Validating origin IP protection measures is a critical step in ensuring that implemented safeguards are effective. Employ penetration testing methodologies to simulate potential attacks and identify vulnerabilities. Analyze logs to track requests and responses, confirming that the origin IP is not exposed in legitimate traffic. Review and update security policies to reflect the implemented measures. Regularly audit and update security policies to ensure that protection measures remain effective and aligned with current threats.
Employ security tools and techniques to proactively monitor and detect potential exposures.
Advanced Concepts
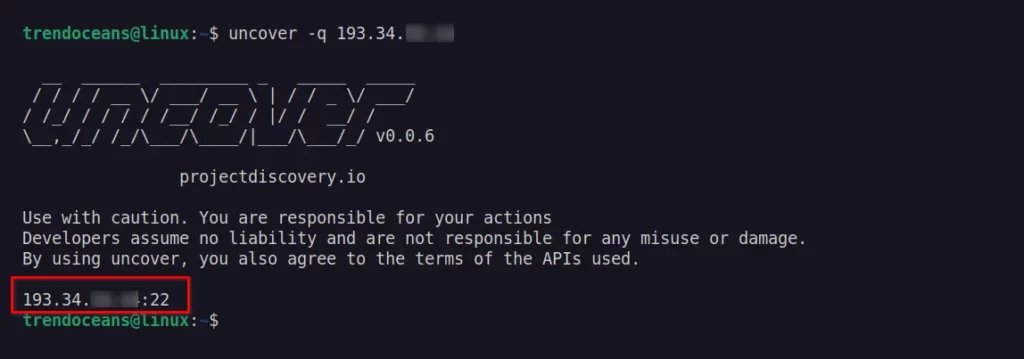
Diving deeper into the world of origin IP exposure, we encounter sophisticated techniques for testing and mitigation. Beyond basic scans, advanced methods often involve exploiting application vulnerabilities or employing specialized tools to uncover hidden connections. Understanding these advanced approaches is crucial for proactively securing applications and preventing potential breaches.Advanced testing methods often involve leveraging specialized tools and techniques to identify vulnerabilities and exposed origin IPs.
These methods go beyond simple port scans and involve intricate analyses of application logic, network configurations, and security protocols. A comprehensive approach is needed to identify potential weaknesses and develop effective mitigation strategies.
Advanced Origin IP Testing Techniques
Advanced testing techniques go beyond basic port scanning, delving into the application’s logic and network configurations to find hidden or misconfigured connections that might expose the origin IP. These methods require a deep understanding of the application’s architecture and the network infrastructure.
- Fuzzing and Penetration Testing: These techniques involve systematically sending malformed or unexpected data to the application to identify vulnerabilities that might lead to revealing the origin IP. This proactive approach can uncover hidden pathways that expose the origin IP, providing insights for developing robust mitigation strategies.
- Application-Specific Testing: Some applications might have specific functionalities or APIs that inadvertently expose the origin IP. Careful analysis of these unique features is critical in identifying and patching vulnerabilities that are specific to that application.
- Network Traffic Analysis: Advanced tools and techniques can examine network traffic patterns to pinpoint instances where the origin IP is transmitted or leaked in headers or responses. This detailed analysis helps in uncovering the specific mechanisms that expose the origin IP.
Load Balancers and Reverse Proxies
Load balancers and reverse proxies play a critical role in hiding origin IPs. They act as intermediaries between the user and the server, distributing traffic and masking the actual server’s IP address. This strategy is fundamental in enhancing application security and preventing direct exposure.
- Load Balancers: Load balancers distribute incoming requests across multiple servers, preventing overload on any single server and hiding the origin IP behind the load balancer’s IP address. This approach is crucial for scalability and security.
- Reverse Proxies: Reverse proxies receive incoming requests and forward them to the appropriate server. This mechanism masks the origin IP, making it more difficult for attackers to target individual servers directly.
Different Types of Proxies
Various types of proxies serve different purposes in protecting origin IPs. Choosing the appropriate proxy depends on the specific security needs and application architecture.
- HTTP Proxies: These proxies specifically handle HTTP traffic, masking the origin IP in HTTP requests and responses. They are particularly useful for web applications.
- VPN Proxies: VPN proxies create a secure tunnel between the client and the server, encrypting the communication and further masking the origin IP. They offer enhanced security but might introduce performance overhead.
- Firewall Proxies: Firewalls act as intermediaries, inspecting traffic and blocking malicious requests while hiding the origin IP. They are integral in network security architectures.
Proxy Configurations and Security Implications
Different proxy configurations have varying security implications. The choice of configuration must align with the application’s security needs and the potential risks.
- Transparent Proxies: These proxies do not hide the origin IP, allowing users to see the original server address. This configuration is not recommended for security-sensitive applications.
- Anonymous Proxies: These proxies hide the origin IP but might not offer the same level of security as other proxy types. They might be suitable for specific scenarios.
- High-Security Proxies: These proxies use advanced encryption and authentication methods to provide strong protection against malicious attacks. They are essential for applications handling sensitive data.
Comprehensive Origin IP Security Review Process
A comprehensive origin IP security review process is essential for proactively identifying and mitigating risks. This process should involve multiple steps and stakeholders.
- Assessment Phase: Thorough analysis of the application architecture, network infrastructure, and security controls to identify potential vulnerabilities and areas where origin IPs might be exposed.
- Testing Phase: Employing various testing techniques, including vulnerability scanning and penetration testing, to identify exposed origin IPs and assess the impact of potential attacks.
- Mitigation Phase: Implementing appropriate mitigation strategies, such as configuring load balancers, reverse proxies, and secure proxies, to protect the origin IP and prevent exploitation.
- Monitoring Phase: Continuous monitoring of the application and network to detect any new vulnerabilities or security incidents related to origin IP exposure.
Epilogue
In conclusion, safeguarding against exposed origin IPs requires a multifaceted approach. By understanding the risks, employing appropriate testing methods, and implementing robust mitigation strategies, you can significantly enhance the security posture of your web applications and APIs. This guide provides a solid foundation for protecting your infrastructure from exploitation, emphasizing the importance of proactive security measures.