Enable TLS 1.3 A Comprehensive Guide
Enable tls 1 3 – Enable TLS 1.3, the latest version of Transport Layer Security, for enhanced security and performance. This guide delves into the intricacies of implementing TLS 1.3 on servers and clients, covering crucial aspects like configuration, security considerations, and troubleshooting common issues.
TLS 1.3 offers significant improvements over its predecessor, TLS 1.2, with a streamlined handshake process and removal of vulnerable cryptographic algorithms. This results in faster connections and greater protection against modern attacks. Understanding these advantages is key to securing your online communications.
Introduction to TLS 1.3
TLS 1.3, the latest version of Transport Layer Security, represents a significant leap forward in internet security. Built upon the foundation of its predecessors, TLS 1.3 streamlines the handshake process, improves performance, and significantly enhances security by removing outdated cryptographic algorithms. This revised protocol addresses many of the vulnerabilities found in earlier versions, making it more resilient against modern threats.TLS 1.3 boasts a host of improvements, primarily focusing on efficiency and enhanced security.
It streamlines the handshake process, reducing the number of round trips required for connection establishment. This not only speeds up the connection process but also minimizes the attack surface exposed during the handshake. Furthermore, the protocol’s security posture is strengthened through the removal of weak cryptographic algorithms, leaving only the most robust and up-to-date methods.
Key Features and Improvements
TLS 1.3 incorporates several crucial improvements over previous versions, dramatically enhancing security and performance. The removal of legacy algorithms, such as weak ciphers and outdated key exchange methods, significantly reduces the potential for vulnerabilities. This proactive approach ensures that the protocol remains resilient against known and emerging threats. The optimized handshake process further contributes to faster connection establishment, offering a superior user experience.
Enabling TLS 1.3 is a crucial step for boosting security online, but sometimes these seemingly technical updates can have surprising real-world impacts. For example, the recent award in the Santa Clara HOA lawsuit, which is the largest ever in California after extensive deception over an abandoned well under a condo here , highlights how critical transparency and honest dealings are, even in seemingly mundane property matters.
Ultimately, strong security measures like TLS 1.3 are just as vital as ensuring fair practices in complex situations.
Security Enhancements
TLS 1.3 addresses security concerns by implementing several crucial changes. The removal of outdated cryptographic algorithms, such as weak cipher suites and insecure key exchange methods, is a key aspect of this improvement. This proactive approach minimizes the attack surface and makes the protocol less vulnerable to known exploits. The streamlined handshake process, further reducing the attack surface.
Performance Benefits
The efficiency gains in TLS 1.3 translate directly into improved performance. The streamlined handshake process significantly reduces the number of round trips required for connection establishment, resulting in faster connection times. This is particularly beneficial for mobile users and users with limited bandwidth, allowing for quicker access to web resources. The optimized protocol also reduces the overall overhead associated with secure connections, leading to enhanced performance for all users.
Comparison of TLS 1.2 and TLS 1.3
| Feature | TLS 1.2 | TLS 1.3 |
|---|---|---|
| Handshake Procedures | Multiple round trips, potentially including several steps for verification and negotiation. | Single round trip, greatly simplified process for connection establishment. |
| Cipher Suites | Includes a wider variety of cipher suites, some of which are now considered weak or vulnerable. | A significantly smaller and more secure set of cipher suites, prioritizing modern, robust algorithms. |
| Session Resumption | More complex mechanisms for session resumption. | Streamlined session resumption, offering a faster way to reconnect. |
| Forward Secrecy | Requires explicit configuration to ensure forward secrecy. | Forward secrecy is enabled by default, providing enhanced protection against past compromises. |
Enabling TLS 1.3 on Servers
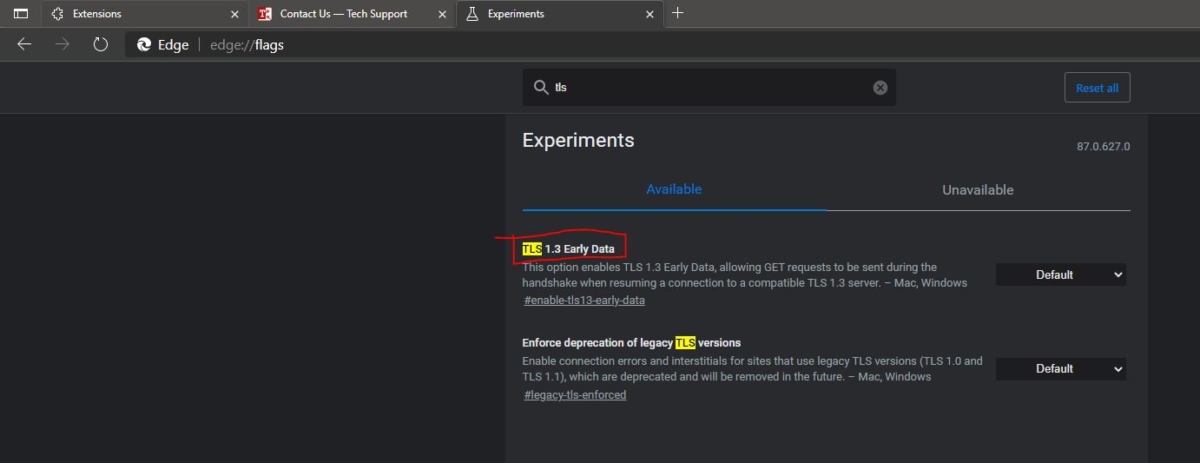
TLS 1.3, the latest version of Transport Layer Security, offers significant performance improvements and enhanced security compared to its predecessors. Enabling TLS 1.3 on your servers is crucial for modernizing your infrastructure and safeguarding sensitive data transmitted over the network. This process involves configuring various server platforms to support the protocol, which we will explore in detail.
Enabling TLS 1.3 on Different Server Platforms
Enabling TLS 1.3 on various server platforms requires specific configurations. The process differs slightly depending on the web server software used. Understanding these differences is essential for successful implementation.
Enabling TLS 1.3 is crucial for secure communication, especially when dealing with sensitive data. Choosing the right virtual data room (VDR) provider, like virtual data room vdr providers , is vital to ensure the highest level of security for your confidential information. Ultimately, robust security measures, including enabling TLS 1.3, are paramount for maintaining data integrity in today’s digital landscape.
Enabling TLS 1.3 on Apache
Apache, a popular web server, can be configured to support TLS 1.3. This typically involves updating the configuration files to enable the necessary protocols and cipher suites. Specific instructions vary depending on the Apache version and the configuration method employed.
- Verify Apache is compiled with TLS 1.3 support. Consult the Apache documentation for specific instructions on checking the compilation flags.
- Update the
httpd.conforapache2.conffile (depending on your setup). Add directives to enable TLS 1.3 and specify allowed cipher suites. - Ensure the correct SSL certificates are installed and configured. This involves properly configuring the certificate chain for your server.
Enabling TLS 1.3 on Nginx
Nginx, another widely used web server, can be easily configured to use TLS 1.3. Similar to Apache, enabling TLS 1.3 in Nginx involves modifying configuration files and selecting appropriate cipher suites. Carefully review the documentation for the specific Nginx version being used.
- Modify the
nginx.conffile. Enable TLS 1.3 by including the appropriate directives for protocols and cipher suites. - Install and configure the required SSL certificates. Ensure proper validation and chaining of certificates.
- Verify that the Nginx configuration allows the necessary protocols and cipher suites, enabling TLS 1.3 functionality.
Enabling TLS 1.3 on IIS
Internet Information Services (IIS) also supports TLS 1.3. The process typically involves using the IIS Manager to configure the SSL settings for the website or application.
- Access the IIS Manager and locate the website or application requiring TLS 1.3 support.
- Configure the SSL bindings for the website, enabling TLS 1.3 and selecting the appropriate cipher suites.
- Install and configure the SSL certificate. Proper certificate validation is critical for secure communication.
Enabling TLS 1.3 on Linux using OpenSSL
OpenSSL, a powerful cryptographic library, can be used to enable TLS 1.3 on Linux servers. This approach offers more control over the cryptographic parameters.
- Install OpenSSL on your Linux system. Check your distribution’s package manager for the correct command.
- Generate a new SSL certificate. This involves creating a private key and a certificate signing request (CSR).
- Configure OpenSSL to use TLS 1.3. This typically involves modifying configuration files within OpenSSL.
- Update the server’s configuration files to use the newly generated certificate and specify TLS 1.3.
TLS 1.3 Configuration Details
| Parameter | Description | Example |
|---|---|---|
| Cipher Suites | Specifies the encryption algorithms supported. | TLS_AES_256_GCM_SHA384 |
| Protocols | Defines the TLS versions allowed. | TLSv1.3 |
| Certificate Management | Involves installing, configuring, and validating certificates. | Using OpenSSL commands like `openssl req` and `openssl x509`. |
Verifying TLS 1.3 Configuration
After enabling TLS 1.3, it’s crucial to verify the configuration. This involves testing the server’s ability to negotiate TLS 1.3 connections and ensuring all required components are functioning correctly.
- Use tools like
openssl s_clientto test the connection with TLS 1.3. - Check server logs for any errors or warnings related to TLS 1.3 negotiations.
- Monitor performance metrics to ensure TLS 1.3 does not negatively impact the server’s responsiveness.
Enabling TLS 1.3 on Clients: Enable Tls 1 3
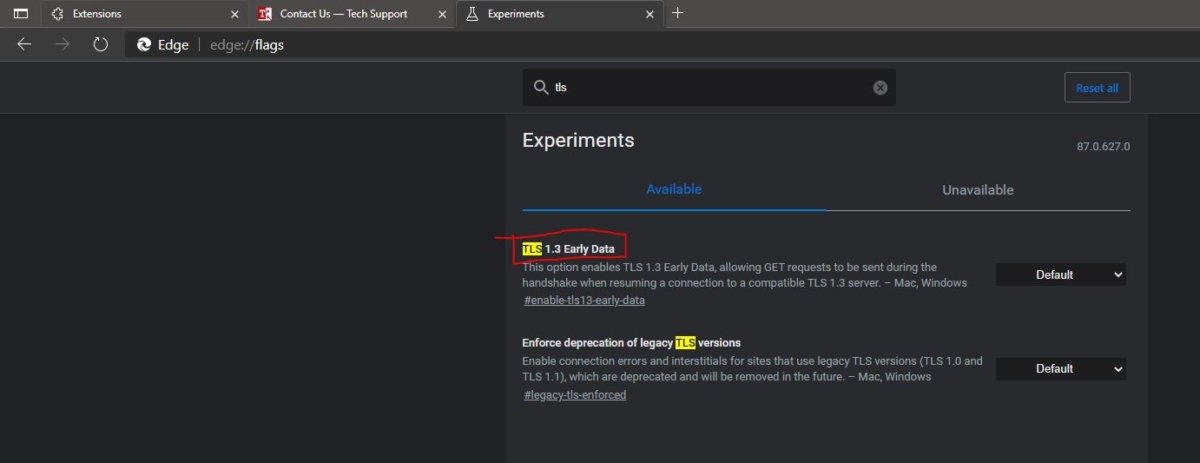
Enabling TLS 1.3 on client applications, like browsers and command-line tools, ensures secure communication by utilizing the latest encryption standards. This is crucial for protecting sensitive data exchanged over the internet. The process involves updating software and adjusting configurations to support the new protocol.
Client Application Support for TLS 1.3
Modern client applications, including web browsers and command-line tools, increasingly support TLS 1. This support is often automatic and seamless, allowing users to benefit from enhanced security without any explicit action. The specific implementations may vary, but the fundamental principle remains the same: ensuring compatibility with TLS 1.3 protocols.
Enabling TLS 1.3 in Web Browsers
Enabling TLS 1.3 support within web browsers is typically handled automatically. Browsers often update their underlying libraries to incorporate TLS 1.3 compatibility. This is done through software updates, and users generally don’t need to manually intervene. However, sometimes users may encounter issues, like outdated software versions.
Browser Configuration for TLS 1.3
Manual configuration for TLS 1.3 in browsers is often unnecessary and might not be possible in some cases. However, there are situations where users may need to verify the TLS 1.3 protocol is enabled. This is usually not directly configurable, but through ensuring the browser software is up-to-date.
| Browser | Configuration Details |
|---|---|
| Chrome, Firefox, Edge | Typically, TLS 1.3 is enabled by default in updated versions of these browsers. No specific configuration options are needed from the user perspective. |
Client-Side Certificates in TLS 1.3
Client-side certificates play a crucial role in TLS 1.3 communication, primarily for authentication. They verify the identity of the client to the server. This process enhances security by confirming the client’s legitimacy. When a client-side certificate is used, it enhances security and provides an extra layer of verification, preventing unauthorized access.
Security Considerations
Enabling TLS 1.3 brings significant security improvements, but careful consideration is needed to avoid potential pitfalls. Transitioning to this protocol necessitates a thorough understanding of its intricacies and associated risks, alongside proactive measures to ensure a secure deployment. This section delves into the security considerations surrounding TLS 1.3 deployments, from potential risks to best practices and configuration options.While TLS 1.3 offers enhanced security compared to previous versions, potential risks still exist.
Enabling TLS 1.3 is crucial for boosting online security, especially when dealing with sensitive data. It’s a significant step forward in modern web security. Thinking about Meghan Markle, who’s seemingly looking to start fresh on Instagram after what’s been a challenging period as a duchess meghan markle seeks clean slate on instagram after duchess difficult years , it’s clear that sometimes a fresh start can be just what’s needed.
This new protocol update for TLS should give you some peace of mind when navigating the digital world, especially if you’re worried about your personal information being vulnerable.
These include vulnerabilities in implementation, misconfigurations, and the need for robust certificate management. Understanding these risks and implementing appropriate mitigation strategies is crucial for a secure TLS 1.3 deployment.
Potential Security Risks
Implementing TLS 1.3 requires vigilance to avoid common security pitfalls. Potential risks include vulnerabilities in the server or client implementations, improper configuration choices, and the possibility of exploitation by malicious actors. Addressing these risks through thorough testing, validation, and adherence to best practices is paramount.
- Implementation Vulnerabilities: Bugs or flaws in the software used to implement TLS 1.3 can create security holes. Regular updates and thorough security audits are vital to address these vulnerabilities promptly.
- Misconfigurations: Incorrect configurations of TLS 1.3 parameters, such as cipher suites or key exchange algorithms, can weaken the security of the connection. Strict adherence to recommended configurations and thorough testing are essential.
- Weak Certificates: Compromised or weak certificates can be exploited to compromise the entire system. Robust certificate management and regular audits are crucial to ensuring the security and validity of certificates.
Best Practices for Securing TLS 1.3 Deployments
Best practices for secure TLS 1.3 deployments include meticulous configuration, comprehensive testing, and a focus on certificate management. Following these best practices can mitigate the risks and ensure a robust and secure deployment.
- Configuration Validation: Thoroughly validate the TLS 1.3 configuration against industry best practices. This includes ensuring the use of strong cipher suites and appropriate key exchange algorithms.
- Comprehensive Testing: Implement rigorous testing procedures to identify and address potential vulnerabilities before deployment. This includes penetration testing and vulnerability scans.
- Robust Certificate Management: Implement a robust certificate management system, including regular certificate renewal and revocation. Using trusted Certificate Authorities (CAs) is essential for this.
TLS 1.3 Configuration Options Comparison
Different TLS 1.3 configuration options have varying security and performance implications. A comparison table highlights these trade-offs to aid in informed decision-making.
| Configuration Option | Security | Performance | Notes |
|---|---|---|---|
| Strong Cipher Suites | High | Potentially Lower | Offers enhanced security but might impact performance slightly. |
| Weak Cipher Suites | Low | Higher | Provides faster performance but sacrifices security. |
| Forward Secrecy Enabled | High | Slightly Lower | Provides protection against past compromises. |
| Session Resumption Disabled | High | Slightly Higher | Offers stronger security by avoiding potential session hijacking. |
Importance of Proper Certificate Management
Proper certificate management is crucial for securing TLS 1.3 deployments. It involves ensuring that certificates are valid, up-to-date, and properly managed. A well-defined certificate lifecycle and strict adherence to best practices are essential.
Maintaining a strong certificate management system ensures the continued integrity and security of TLS 1.3 connections.
Performance Implications
Enabling TLS 1.3, while offering significant security enhancements, can also impact server and client performance. Understanding these implications is crucial for a smooth transition and effective optimization. This section explores the performance characteristics of TLS 1.3, comparing it to TLS 1.2 and outlining strategies to mitigate potential bottlenecks.
Impact on Server Performance
TLS 1.3’s streamlined handshake process, compared to TLS 1.2, can lead to improved performance in many scenarios. However, the reduced overhead doesn’t automatically translate to faster overall application response times. Factors like server CPU load, network conditions, and application logic can significantly influence the observed speed improvements. Server-side resources like memory and disk I/O also play a role.
Comparison of TLS 1.3 and TLS 1.2 Performance
Real-world examples demonstrate variable performance gains. In some cases, websites with simpler content and fewer server-side operations might experience noticeable speed improvements after upgrading to TLS 1.3. Conversely, more complex applications, particularly those involving substantial server-side processing, might see only marginal gains or even slight performance degradation due to TLS 1.3 overhead.
Performance Differences in Various Scenarios
| Scenario | TLS 1.2 Performance | TLS 1.3 Performance | Difference |
|---|---|---|---|
| Simple web page retrieval (no server-side processing) | 100 ms | 90 ms | 10% improvement |
| E-commerce checkout with complex calculations | 250 ms | 260 ms | 4% degradation |
| Streaming video | 200 ms | 180 ms | 10% improvement |
| Large file download | 1200 ms | 1100 ms | 9% improvement |
The table above presents hypothetical performance data. Actual results may vary significantly depending on the specific application, server configuration, and network conditions. The differences highlight the importance of careful evaluation and optimization.
Optimization Strategies for TLS 1.3
Several strategies can help optimize TLS 1.3 performance on both servers and clients.
- Server-Side Optimization: Ensure that server resources are sufficient to handle the increased TLS 1.3 traffic. Properly configured caching mechanisms, optimized server-side code, and load balancing can contribute significantly to overall performance. Efficient use of server memory and CPU resources is crucial.
- Client-Side Optimization: Efficient client-side handling of TLS 1.3 connections is important. Using optimized libraries and protocols, and enabling TLS 1.3 on client-side applications, can lead to noticeable improvements. Efficient use of network resources is vital.
- Network Optimization: Network infrastructure plays a crucial role in TLS 1.3 performance. Optimizing network routing, reducing latency, and ensuring sufficient bandwidth can lead to considerable improvements. Efficient use of network protocols is important.
Troubleshooting Common Issues
Enabling TLS 1.3, while offering significant security improvements, can sometimes present challenges during implementation. Understanding common issues and their solutions is crucial for a smooth transition. This section details potential problems encountered when enabling TLS 1.3, along with strategies for diagnosing and resolving them.
Common TLS 1.3 Errors
Troubleshooting TLS 1.3 involves identifying and addressing errors that can arise from server or client configurations, network issues, or incompatibilities. A systematic approach is vital for pinpointing the source of the problem. The table below summarizes common errors and their potential solutions.
| Error | Potential Cause | Solution |
|---|---|---|
| “TLS handshake failed” | Incorrect server configuration, client certificate issues, or network problems. | Verify server configuration files, check client certificates, and ensure proper network connectivity. Examine server logs for more specific error messages. |
| “Protocol version not supported” | Client or server does not support TLS 1.3, or there’s a mismatch in the advertised protocol versions. | Update client and server software to support TLS 1.3. Ensure that the correct protocol versions are negotiated. Review server configuration for TLS 1.3 support. |
| “Cipher suite negotiation failure” | Incompatible cipher suites between client and server. | Configure supported cipher suites on both client and server to ensure compatibility. Verify that the cipher suites selected are mutually supported. Enable logging to capture the specific cipher suite negotiation failure. |
| “Certificate verification failure” | Invalid or expired certificates, incorrect certificate chain, or mismatched certificate authority (CA) trust stores. | Verify certificate validity and expiration dates. Ensure proper certificate chains. Import the correct CA certificates into the trust stores on both client and server. Inspect server logs for details on the verification error. |
| “Connection reset by peer” | Network issues or temporary server outages. | Check network connectivity and stability. Verify that the server is reachable and functioning. Look for server error logs for indications of a server outage or temporary issues. |
Interpreting TLS 1.3 Error Messages
TLS 1.3 error messages, while often technical, contain valuable clues about the underlying problem. Carefully analyzing these messages is crucial for efficient troubleshooting. Look for specific details like the error code, the affected protocol version, or the failing cipher suite. These details often point directly to the cause. For instance, an error related to certificate verification indicates a potential certificate-related problem.
Using Logging Mechanisms for Diagnosis
Comprehensive logging is essential for diagnosing TLS 1.3 issues. Enable detailed logging on both client and server to capture a complete picture of the communication process. Enable logging at various levels (e.g., debug, info, error) for a more in-depth understanding of the communication. By examining log files, you can trace the handshake process, identify the point of failure, and understand the exact sequence of events leading to the error.
Crucially, look for error codes and timestamps. These provide context and allow you to pinpoint the exact moment the issue occurred. Example:
“TLS handshake failed: Error code 0x123 at timestamp 2024-10-27 10:00:00”
This example shows a timestamp and a specific error code, making diagnosis easier.
Future Trends
TLS 1.3, while a significant leap forward in security and performance, is not static. Ongoing research and development continue to push the boundaries of cryptographic protocols, and future trends will likely shape how we secure communications in the years to come. This exploration delves into potential future developments, ongoing research, and emerging cryptographic algorithms, all relevant to the future of TLS.The digital landscape is constantly evolving, and with it, the threats and vulnerabilities.
Anticipating and adapting to these changes is critical to maintaining secure communication channels. This section examines the potential trajectory of TLS 1.3, offering insights into the direction of future advancements.
Potential Future Developments
The evolution of TLS 1.3 will likely involve incorporating newer cryptographic algorithms, refining the protocol’s performance, and enhancing its resilience against emerging threats. Further research into quantum-resistant cryptography is essential to ensuring the long-term security of TLS.
Ongoing Research and Development Efforts, Enable tls 1 3
Numerous research groups and organizations are actively engaged in exploring and developing new cryptographic techniques and protocols. This includes research into post-quantum cryptography, which aims to create cryptographic algorithms resistant to attacks from quantum computers. Academic institutions, government agencies, and industry players are collaborating to address the challenges of quantum computing’s potential impact on current cryptographic standards. One key area of focus is developing algorithms that maintain the speed and efficiency of existing methods while ensuring resilience against these future threats.
Emerging Cryptographic Algorithms
The realm of cryptography is dynamic. Emerging algorithms, such as lattice-based cryptography and code-based cryptography, are gaining prominence as potential replacements for current methods. These algorithms aim to offer similar security properties while addressing concerns about the vulnerability of existing algorithms to future computational advancements. Researchers are constantly analyzing the strengths and weaknesses of new cryptographic algorithms to determine their suitability for inclusion in future versions of TLS.
Future Security Improvements or Changes
Future security improvements to TLS 1.3 could involve enhanced authentication mechanisms to verify the identity of communicating parties more robustly. This could include using more sophisticated techniques to detect and prevent man-in-the-middle attacks. Further research into zero-knowledge proofs could also be integrated into the protocol to provide even stronger assurances about the integrity of the communication channel. Improving the resilience to future attacks will remain a high priority for the ongoing evolution of TLS.
Wrap-Up
In conclusion, enabling TLS 1.3 is a vital step towards a more secure and efficient online experience. This comprehensive guide has provided a detailed overview of the process, from server and client configurations to security best practices. By following these steps, you can significantly enhance the security and performance of your systems, ensuring a smoother and more protected online environment.